A full guide on how to get Nethunter onto a Pixel 4a.
cybersecurity

This is gonna get worse before it gets better. Place your Yaesu FT-2000 donation on our doorstep.

You thought, Hackers are stupider than Scammers? Stupider like a fox?
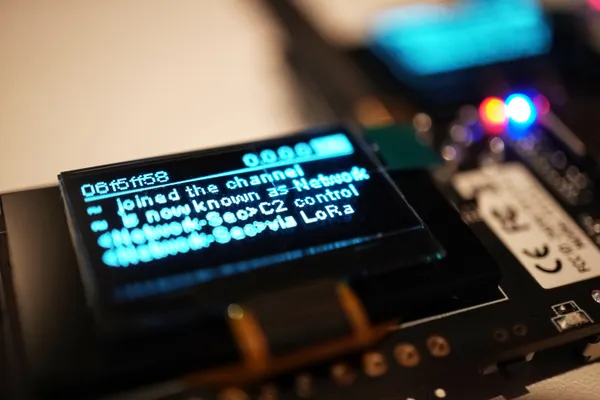
And all the small things.

Running rockyou.txt is easy enough - but nowadays hardly succesful, at least not as goto-solution.

A horrible year is finally ending. Even without resources or support, we upped our toolkit to create actionable Intelligence.

Let's use our knowledge and apply it to a common problem: Weaponized Fake Reviews

Many older devices still vulnerable, complete exposure of all traffic.

Leasing a SIM on a garage sale: confidentiality, integrity, availability
AhMyth is a Android RAT capable of compiling malicous .apks that can control almost anything on a victim phone.
This blog post will cover how to execute a payload on opening a powerpoint presentation.

Today, pretty much all tools and methods are fair game when it comes to both Offensive and Defensive Security, especially when we're talking about Social Engineering.
Exploring the rise of ransomware threats in 2023/2024, changes in attack methods, and the challenge of underreporting due to privacy laws.
After a conversation about evasion techniques, we asked about new ones.

Too good to let it rot on the harddrive. Some older notes on Evasion and C# IL, Evasion attempts and more

We're looking at common tools and techniques that fully work in 2024, like the Aircrack-ng suite and additional tools for effective Wi-Fi security testing.

When you start into Ethical Hacking, you may come from a lot of career pathes. For us this meant, we never before had contact or experience with the digital, criminal underworld. We had a lot to learn.

Adapting traditional Intelligence strategy to the modern Cybersecurity landscape.
As preparation exercise, building towards evasion using LOL Drivers, we look at IOCTLs on Windows and eject a USB disk.

We're jammin, jammin - And we hope you like jamming, too.

After we found an extensive guide, how to defraud Online Banking customers, we started analysing the topic.

We take a peek at two more recent publications in the field of Information Security, which are the legal pillars for Redteaming.

While doing OSINT recently, we stumbled across a way to enumerate Facebook Users - without being logged-in.

This is the latest, 2024 Germany & EU version of Open Source Intelligence. All tried and tested.

While the usual tipps on Operational Security are rather generic, we took a deep dive and looked into TrueCrime cases.
Well, well, well. What do we have here?

It's Friday, so let's go low key and look at one of many modern Enumeration and Hacking automation tools. Actually, there are 3 different versions of httpx.

In our evasion series we take a look at the latest in evasion evolution: Freeze

Today we'll show you probably the best Repo for Cybersecurity Professionals - this is truly a gift.

KrbRelayUp is a no-fix method for privilege escalation - that's why it's still very interesting and usable.

There are days in Hacking when things don't work as expected - such happened to our latest topic. Instead, we'll have a look at a more historic topic: Format String Exploits

Got your new Schmalaxy SXT9000 Smartphone with the great features and security, but it's already boring? Let's bring tools like Metasploit or SQLMap into your Pocket

We already explored many simple pathes to be able to run exe files while bypassing EDR like Defender. Now we go a step further.

About one year ago we proposed the use of alternative coding styles to evade code scanners. Guess we gotta prove that it works.

Using a few tricks we can make a PE payload, that looks like a PDF - including file name.
We dive into deeper water today, looking at GSM3 and briefly into SS7.

A suprise special for everyone, who knows what this date means to us.

A Comprehensive Guide for Modern Pentesters

At times, it will be handy to have all complementary evasion commands at hand. We tried to compile the ultimate list, without going overboard.

C2 Powershell Empire is a classic - but can you still use it with EDR (Defender) in place?

We made the bold claim, that all AMSI evasions still work. But is that really true? Come in for a ride.

Let's try and do things like they're done in real attacks. While the media recently was all over ConnectWise ScreenConnect, we instead focus on AnyDesk - which is used by many Cybercriminals these days - in an Assumed Breach scenario.

Once made some architecture visualisations - maybe a chance to explain how these came to life and how I discovered: all evasions still work fine.

Take a look at our Pentesting and CTF Flowcharts - they should help you especially in the beginning.
Explore tactical approaches to bypass PowerShell execution policies, a critical competency for offensive security professionals. This article unveils 15 distinct tactics for executing PowerShell scripts unrestricted, equipping practitioners with the knowledge to navigate and manipulate execution policies effectively.

Looking into every-day Mail Spoofing, often overlooked world of Email Spoofing, where SPF bypass techniques blur the lines between legitimate communication and cyber threats.