A full guide on how to get Nethunter onto a Pixel 4a.
redteam

This is gonna get worse before it gets better. Place your Yaesu FT-2000 donation on our doorstep.

You thought, Hackers are stupider than Scammers? Stupider like a fox?
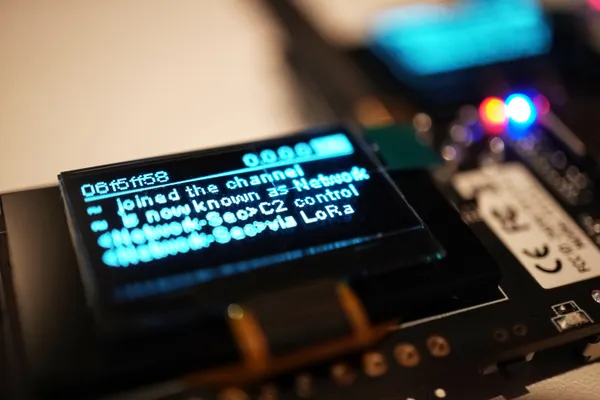
And all the small things.

Running rockyou.txt is easy enough - but nowadays hardly succesful, at least not as goto-solution.

A horrible year is finally ending. Even without resources or support, we upped our toolkit to create actionable Intelligence.
We create a physical Info-Stealer that is undetectable and leaves no traces.

Leasing a SIM on a garage sale: confidentiality, integrity, availability
This blog post will cover how to execute a payload on opening a powerpoint presentation.

Today, pretty much all tools and methods are fair game when it comes to both Offensive and Defensive Security, especially when we're talking about Social Engineering.
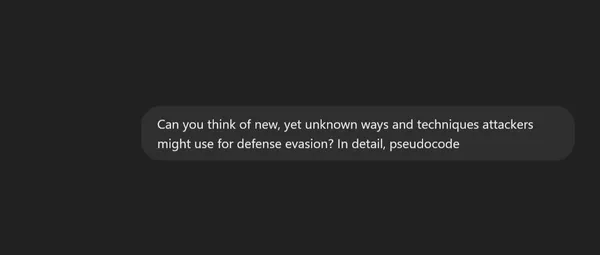
After a conversation about evasion techniques, we asked about new ones.

Too good to let it rot on the harddrive. Some older notes on Evasion and C# IL, Evasion attempts and more

We're looking at common tools and techniques that fully work in 2024, like the Aircrack-ng suite and additional tools for effective Wi-Fi security testing.

We're jammin, jammin - And we hope you like jamming, too.

We take a peek at two more recent publications in the field of Information Security, which are the legal pillars for Redteaming.

In our evasion series we take a look at the latest in evasion evolution: Freeze

Today we'll show you probably the best Repo for Cybersecurity Professionals - this is truly a gift.

KrbRelayUp is a no-fix method for privilege escalation - that's why it's still very interesting and usable.

Got your new Schmalaxy SXT9000 Smartphone with the great features and security, but it's already boring? Let's bring tools like Metasploit or SQLMap into your Pocket

We already explored many simple pathes to be able to run exe files while bypassing EDR like Defender. Now we go a step further.

About one year ago we proposed the use of alternative coding styles to evade code scanners. Guess we gotta prove that it works.

Using a few tricks we can make a PE payload, that looks like a PDF - including file name.

Exploiting suo and csproj files recently gained attention, used in attacks on Cybersecurity researchers. We found another way

Cognitive ease and cognitive strain are two essential concepts in social engineering and psychology, playing a role in everyday human interaction, in combo with Decision Fatique it's the ultimate tool

A suprise special for everyone, who knows what this date means to us.

Negative Manipulation 02 - looking at ways to weaponize provocation and how to create hate.

In this article we show to Average Joe, how you can communicate with unbreakable encryption and almost absolutely private.

At times, it will be handy to have all complementary evasion commands at hand. We tried to compile the ultimate list, without going overboard.

Let's have a look at how you can combine two techniques seemlessly for an evil plan, using a classic priming setup

Power vs Control. In this Social Engineering special, we compare negative manipulation tactics that occur in relationships, the workplace, religious- and other social communities.

The essence of social engineering lies in subtly guiding your target through a conversation without them ever realizing your true intentions. A combination of emotion-first strategy, hooking, and exchanged context forms a powerful toolkit for the adept social engineer.

Let's get deeper into the art and science of Social Engineering, uncovering the psychological underpinnings and tactical applications of emotion-first strategies, hooking, and context exchange. This installment reveals the nuanced techniques that shape influence and decision-making, tailored for enthusiasts and professionals in red teaming and social engineering.

We made the bold claim, that all AMSI evasions still work. But is that really true? Come in for a ride.
We created a custom reverse shell from scratch and made it persistent - the result is scary, to say the least.

Once made some architecture visualisations - maybe a chance to explain how these came to life and how I discovered: all evasions still work fine.

As promissed, we continue executing code using rundll32 on a fully updated system.

Today we're looking at one of the most simple evasions - it's always fascinating to wittness the beauty of traditional hacking exploration methods working to their full extend. The rundll32.exe comma bypass is one of these examples.
Diving deep into the art and science of Social Engineering, exploring its roots in psychology, manipulation tactics, and modern applications. From shocking surprises to exchanging context, uncover the techniques that shape this fascinating field.

Looking into every-day Mail Spoofing, often overlooked world of Email Spoofing, where SPF bypass techniques blur the lines between legitimate communication and cyber threats.