7 min read
Pentesting A full guide on how to get Nethunter onto a Pixel 4a.
A full guide on how to get Nethunter onto a Pixel 4a.

This is gonna get worse before it gets better. Place your Yaesu FT-2000 donation on our doorstep.

You thought, Hackers are stupider than Scammers? Stupider like a fox?
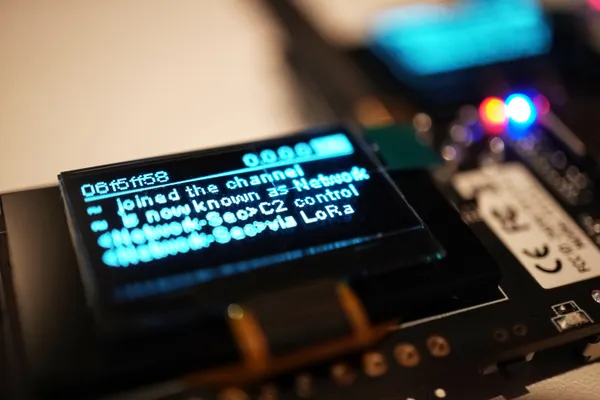
And all the small things.

Running rockyou.txt is easy enough - but nowadays hardly succesful, at least not as goto-solution.

A horrible year is finally ending. Even without resources or support, we upped our toolkit to create actionable Intelligence.