Published
- 3 min read
AhMyth
AhMyth
AhMyth is a Android RAT capable of compiling malicous .apks that can control almost anything on a victim phone.
We’re going to use a modified version of the project, as the original isnt supported anymore, creds to Morsmalleo:
https://github.com/Morsmalleo/AhMyth
If You get any errors we didnt get, maybe try to check the Wiki, its really extensive and helpful: https://github.com/Morsmalleo/AhMyth/wiki/Page-8.-Troubleshoot
Installation
Notes: Please back up your system first as there were some unexpected side effects of the installation. Its important to install via Binary, we tried installing via source code, but this didn’t work even after we spent some time trying to fix it.
First, we install Java 11 Development Kit:
$ sudo apt-get install openjdk-11-jdk* -yThen we download a Binary Release for AhMyth v1.0-beta.5a for Linux from the Releases Section, we used amd64: https://github.com/Morsmalleo/AhMyth/releases/tag/v1.0-beta.5a
We navigate to the location of the download and just install the AhMyth Application Package.
$ sudo apt-get install ./AhMyth-Setup_amd64.debWe got one problem though: Restarting after the installation damaged our lightdm (One of the graphical interfaces for Kali), more specifcally Xorg, to fix this we just needed to do this:
$ sudo apt install xorg openboxUsage
After installing we should be ready to go, but we need to launch it with sudo for it to work:
$ sudo ahmyth --no-sandboxThe visual interface is pretty self explaining, after building (or binding too) a .apk with all the options we want (camera, storage, mic, etc.) and our IP + Port, we can simply transfer the .apk to the victim phone.
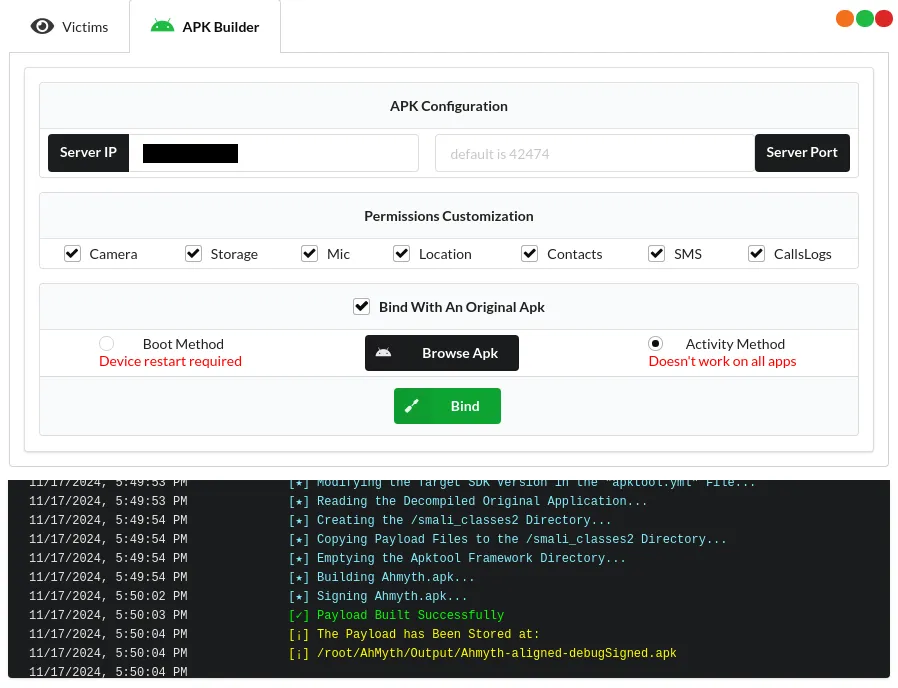
When binding with an .apk make sure that the file is in a user accessible directory (for example in home) and has the right permissions:
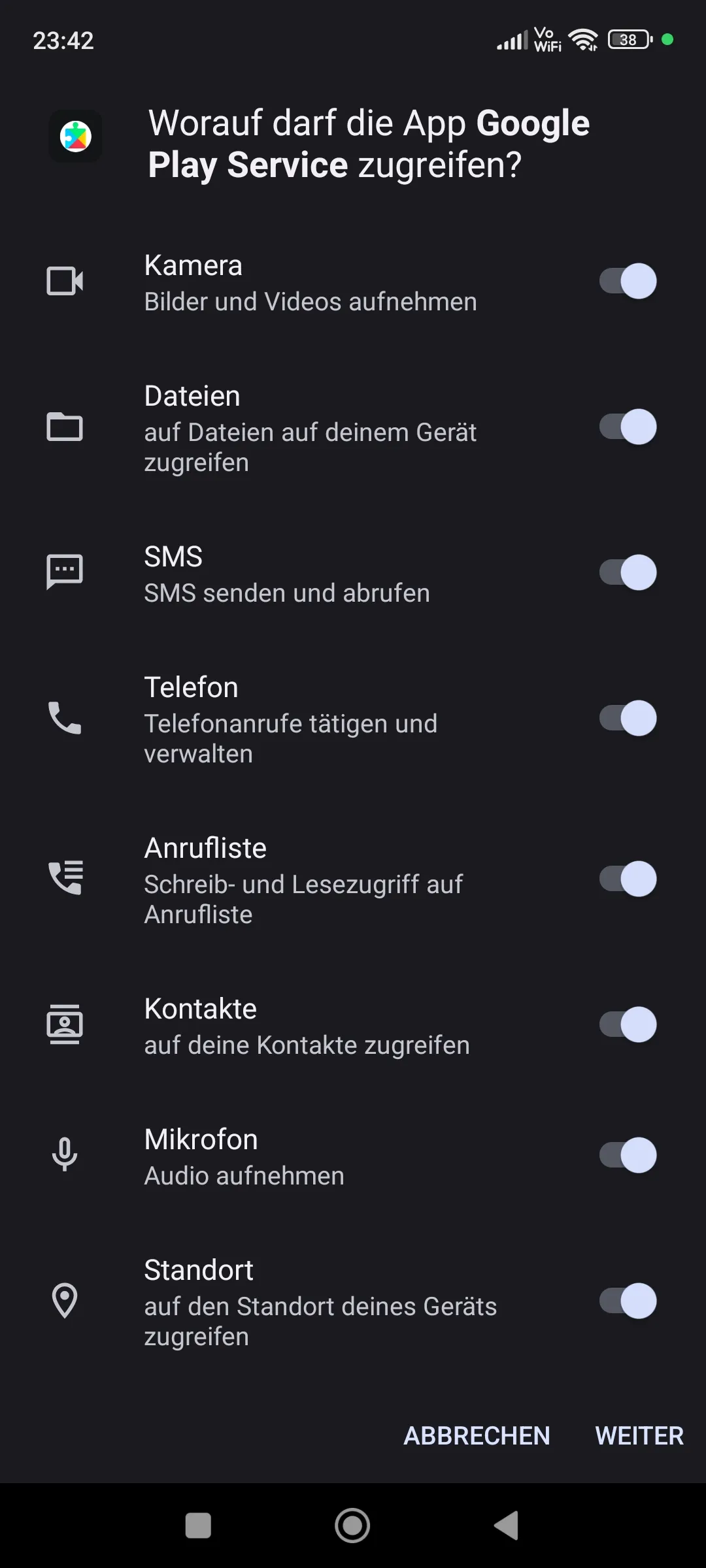
$ chmod +777 ~/app.apkWhile trying to install it, we get a block from Google Play Protect, but we just click More to install it anyways. What’s interesting though is that MIUI Security dosen’t recognize ANY threats in the app, so maybe dont rely on that…
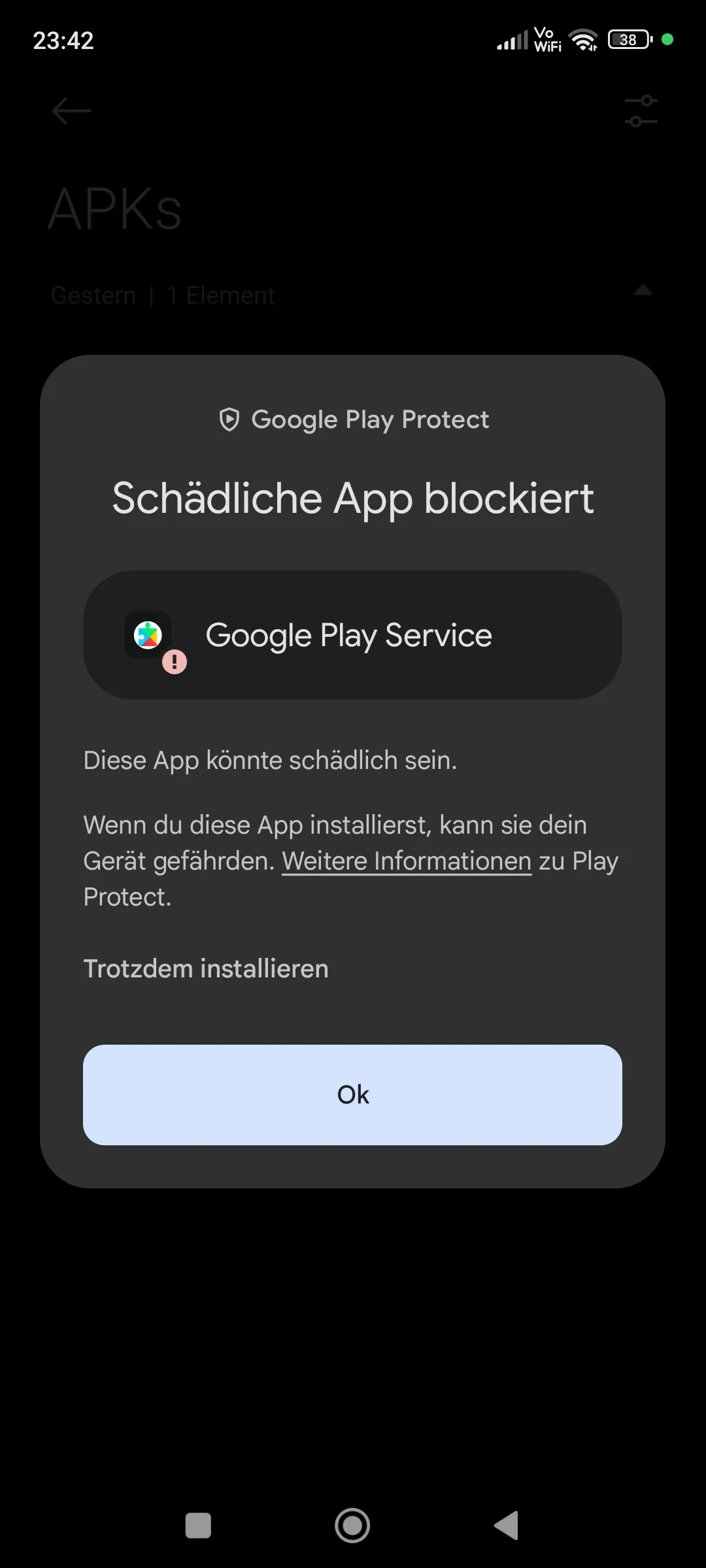 | 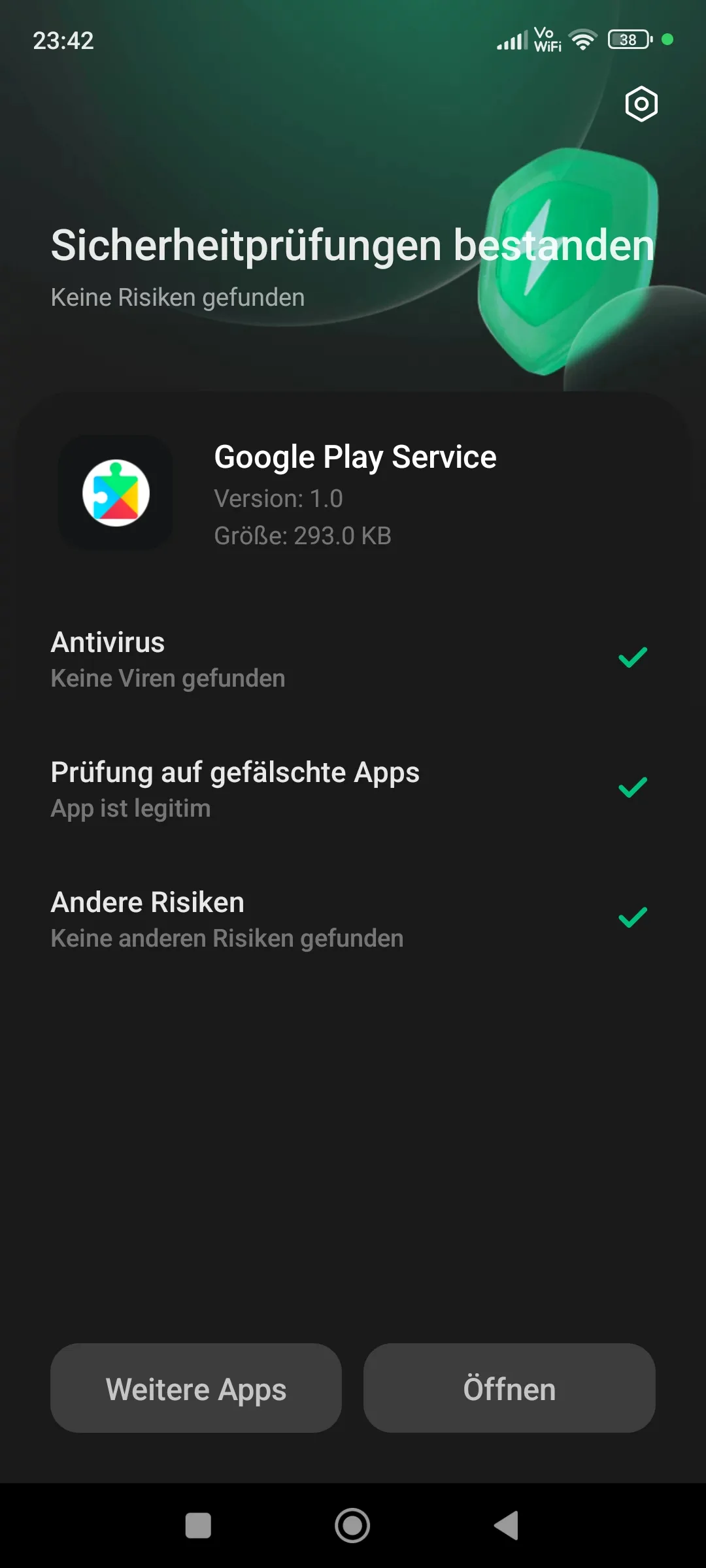 |  |
|---|
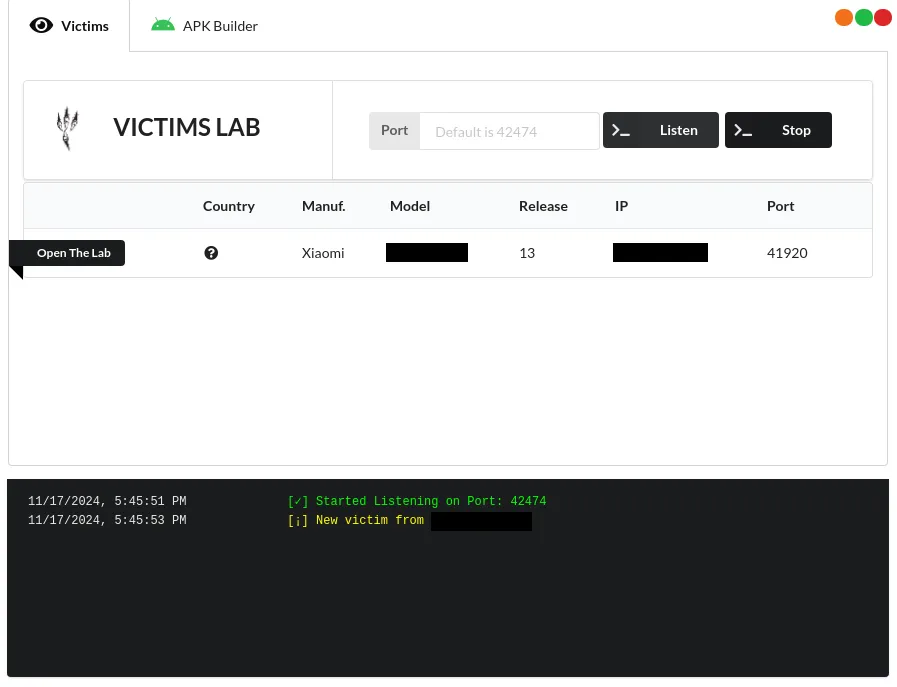
We then start a listener on AhMyth on our chosen Port and, after giving the app the permissions it wants and opening it, we get a connection.
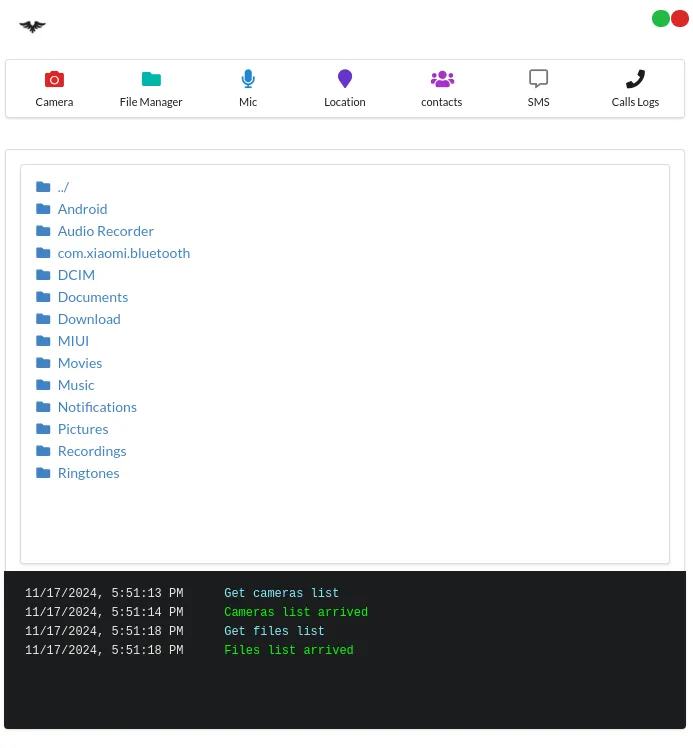
From here on we can do many things: access camera, files, mic, location, contacts, SMS(we can even write them ourselves!) and CallsLogs.
We tried almost all of the features and it seems that all of them worked, at least for us.
This guest article was provided by our trainee, which we proudly present. It was made autonomously and with only minimal help / a few cosmetic updates.