Published
- 32 min read
Researching into Bad Actors OpSec

Update: The article received several smaller content updates, trying to keep it up-to-date and add missing information, clarifying sections that may’ve been confusing before and improving the order of things. This is one of our “list articles” (similar to topics like OSINT), that why we’ll continue to update these, as it makes more sense than to post new articles over and over.
—
While the usual tipps on Operational Security are rather generic, we took a deep dive and looked into TrueCrime cases - especially their OpSec (mistakes).
However, we will neither talk about specific cases, nor about high-profile / APT cases - rather we took information from everyday Cybercrime like fraud or scamming and compiled the results into this document.
This also marks the beginning of another journey we made, for several years we’ve been researching real crime, cases and their details. Now we’ll begin reporting, what we learned.
OPSEC - Anonymity - Pseudonymity - NDA
Usually the level of operational security and it’s byproducts is well-designed around a specific task or position. It highly depends on the confidentiality of these. For IT Security jobs, the lowest level, which we would consider the NDA, is found to be sufficient. This can of course differ depending on your employer and it’s contractors.
For a realistic Redteaming Operation, we take the stance that things like OpSec matter. Of course, we need to keep a safe distance from ethical and legal boundaries, but at the same time, we need to learn from allTheThingsOpSec, not only because one of our tasks is, to immitate Bad Actors, but furthermore, to protect our Legitimate Operations.
Learning about criminal activity has the side-effect of improving your personal OpSec to a level that you’re not completely unprotected, when for example researching between Secret Services on the left and real Blackhats on the right.
Who needs Operational Security
See anonymous
Who needs to be anonymous
- Members of a Special (covert) Unit
- Secret Agents / Secret Service employees
- Criminals
- Cloaked Frogs
Anonymity means to be absolutely, consistently unidentifiable, in all your actions, contacts and communication. It’s hard to impossible to truly achieve, usually we’re satisfied with “good enough”. When we talk about anonymity or how to achieve it, we talk about the good enough version. Pseudonymity is still one step below that.
Who needs to be pseudonymous
At the moment we’re unaware of any position in the private sector or a public office that requires pseudonymity. We’ll continue to research.
“Hide in the shadows, only come out when we need you.” - “but.. don’t hide that well, maybe we need to find you!”
How to achieve…
Buy a internet SIM card on a shady market in Eastern Europe. Use the Tails operating system on a Laptop, which you exclusively use for anonymity.
Be sure to unsolder anything from the Laptop you find suspicious, random chips, cameras, microphones, whatever. Use the Laptop only with a blanket over your head.
Mr. S. is your guide now (Free Snowden!), not only in terms of paranoia level, but also in regards to sacrifice. Be prepared to live in a even more shady country for the rest of your life and never have contact again with anyone you love(d). Nice.
On that Laptop, use full disk encryption, and only work inside VMs that also use full disk encryption. Delete the VMs each time you finish a task or close the Laptop (automatically by Tails). Make sure each subsequent account you use in your task(s) is from now on created and used only on that Laptop. Use TOR exclusively for all internet access, VPNs can be broken. TOR can also be broken through 3rd party security issues.
Of course, change everything about you, name, address, gender, except… wasn’t there some math trick that could identify you because you change everything about you?
Jokes Aside
The previous sarcastic paragraph had two intentions:
One
Showing, that it’s practically impossible to become fully anonymous and getting close already brings a fair share of sacrifices that most people won’t take.
Two
Explaining, that the level of Operational Security needs to match the actual Operation - if your Op has low risk, so can be your OpSec. If your Op brings high risk, you would need to adjust accordingly.
Bad Actors have been identified through:
- Username (also similar username)
- Private Email address
- Not using VPN
in many cases only a single time.
Evidence & Surveillance
We researched couple of years into Crime in general, not only Cybercrime. The “average criminal” (if there’s such a person) believes:
- The Police can hack / has hacked everything (Email, WhatsApp, their Webcam …)
- Police and Secret Services listen in, monitor and read chat logs constantly
- All encryption can be broken
This stems mostly from lack of technical understanding and awareness about their own OpSec mistakes, being in denial about how much information they gave away willingly - while claiming inside their circles, they would never talk to the Police, and more ofthen than not, accusing their former partners to have “ratted out” on them.
Boasting on Instagram about the iPad you've just stolen remains a classic, but certainly isn’t the only form today, how criminals show to the entire world, what they did.
Cooperation with Investigators
“You can hack everything - you just can’t be caught” - freely quoting Linus Neumann, now official speaker of the CCC, in a talk he gave more than a decade ago, explaining that you should always use VPN before you start testing the parameters of a random Webshop.
We’d like to take this philosophy one step further, and, contrary to popular oppinion and lawyer’s advice, explain that we think, it’s best to cooperate with Law Enforcement in almost all cases, at the same time you should use “your right not to incriminate yourself”.
This section might appear confusing, cause it resembles a mix of experience, from Truecrime cases as well as legitimate operations like Security Research.
Most people will cooperate with the Police, when charges are severe, even hardened, long-term career criminals.
If you find yourself in an investigation, you should always try to remain calm and at the same time, try to correctly estimate your chances to resist professional investigation & interrogation techniques, including the effects of demotivating actions, like:
- being held in a cell
- being raided at 4:30 a.m.
- losing access to all your posessions
- your existence hanging on one single phone call per week
- threats of long prison sentences
- everything that goes with it, like losing your partner or family, your appartment, your job (and never being able to return to your career)
- being extradited to a country with “lesser attention on human rights”
- losing citizenship / access to the EU
- being forced to live on the run
- the most scary: your lawyer’s invoices
Tactically cooperating up front, from the beginning, could be decisive. We know from lots of cases, chances to make a deal, no matter how small it is, are way higher in the beginning, than at any later stage.
That also means: Have some balls - you thought you had them, when you did the operation. Be a “man” and admit to your wrong-doings. It will make things easier for you.
Lawyers will give the opposite advice - but they also sleep in a comfortable bed, high up on a big pile of money.
That doesn’t mean, you should admit to things you haven’t done. Neither should you take the blame for actions that were legal - like a legitimate Pentest or Redteam operation. These are the cases, where you need to fight back, should you be accused for doing them.
Secure Deleting
https://www.heise.de/download/product/eraser-18980
Erasor provides military-grade deletion by overwriting files. For SSDs and NVME technology, this is no longer that important, for HDDs and SD-Cards it remains invaluable.
Good OpSec means, making it as hard as possible for someone to follow your tracks. Encrypt all your devices savely, so they cannot be cracked. Be informed about side-channel attacks, like someone distracting you to access your unlocked Laptop or installing Malware. Don’t keep data around, that you don’t need anymore, but that might be used as evidence against you.
Consider you might lose a device or access to it, as well as accounts being hacked and data leaked.
If you’re on a Mission: Be on a Mission - make a new Virtual Machine, make generic names for everything (i.e. Username Kali), use an Internet Access that’s not directly connected to you (at least VPN) and delete everything as soon as you’re done. Be quick. But know that, even people following all of these rules have been caught, when their actions were malicious.
Scanning Websites
with free online tools. These days, doing a Port Scan - if it’s not a high-value target - most likely won’t lead to legal or investigative action.
This reflects in the tools we have today: Many websites offer complete Vulnerability Scanners, free of charge, without registration. Same goes for Hosting, VPN services, Email, SMS, … you can practically do an entire Pentest using only 3rd party tools and IPs.
That doesn’t mean, doing an unauthorized scan of someone’s website has become legal but rather, it has become tolerated. It remains illegal.
Of course, if your scan is followed up by a succesful hack, that’s a different story and the investigative actions following up on such can be a lot more and a lot more severe.
Once again, we probably don’t need to tell you, you might have had good intentions, finding a vulnerability to disclose responsibly - yet a company owner or bystander might interpret your actions completely opposite.
Portscanner
https://www.ipvoid.com/port-scan/
Crawler
Download ThisPersonDoesNotExist
Much easier than pressing the button over and over. Keep downloading till you got a close match.
#!/bin/bash
for i in {1..10000}; do
img=$(curl -s "https://this-person-does-not-exist.com/new?...adjust params..." | grep "src" | cut -d ":" -f 5 | sed -E -e 's/\"|\}|\"\}//g')
wget "https://this-person-does-not-exist.com/img/$img"
sleep 4
doneWebsites / Data Collection
- https://kontactr.com/ - online form builder / post target
VPN
ProtonVPN
- Registration: Email required.
- Data Limit: Unlimited data.
- Note: Strong focus on privacy, with some servers supporting Secure Core protection.
TunnelBear
- Registration: Email required.
- Data Limit: 500MB per month, can tweet for an extra 1GB.
- Note: User-friendly with a strong focus on simplicity and ease of use.
Hotspot Shield
- Registration: No registration for the free version.
- Data Limit: 500MB per day.
- Note: Offers a daily data limit, which is quite generous for a free plan.
Hide.me
- Registration: Email for the free account.
- Data Limit: 10GB per month.
- Note: Offers a good balance of speed and security with a decent data cap.
Windscribe
- Registration: None (Email for 10GB traffic)
Proxy / SOCKS services
https://github.com/Network-Sec/bin-tools-pub/blob/main/proxy_pac.sh
https://github.com/Network-Sec/bin-tools-pub/blob/main/proxy_pac_tested.sh
Check out our scripts for automating proxy workflows - it’s just a starter, but will get you started.
Free Proxies
https://free-proxy-list.net/
https://hidemy.io/en/proxy-list/
https://spys.one/en/
https://www.proxynova.com/proxy-server-list/
https://vpnoverview.com/privacy/anonymous-browsing/free-proxy-servers/
https://github.com/rootcathacking/catspin
https://github.com/Yariya/Zmap-ProxyScanner
https://pythonhosted.org/http-request-randomizer/index.html <--- Warning, don’t run without checking the source
Not sure how much sense “anonymous” proxies still make - who actually runs them and collects your traffic. https won’t work on http proxies - on socks5 you may get lucky.
We wouldn’t normally use them - maybe to bypass a rate limiting, but when doing so, you should log your attempts, so you’re able to prove your intent.
Chances are, nobody would have ever noticed your activity, good or bad, but by using these proxies you suddenly find yourself within a more serious investigation by law enforcement of country X, cause somebody else commited a serious crime on the same IPs. Or someone sneaks in malicious data into your unencrypted stream. If something is for free, you’re the product being sold.
HideMyAss Free Proxy
- Registration: No need for registration for basic proxy use.
- Features: Offers free web proxy services with multiple server locations. It’s more for casual browsing due to potential security and privacy limitations.
ProxySite.com
- Registration: No registration required.
- Features: Lets you browse the web anonymously with the ability to choose between different server locations. Supports popular websites like YouTube and Facebook.
KProxy
- Untested
Free SOCKS Proxy List
$ git clone https://github.com/TheSpeedX/PROXY-ListBrowser in Browser
Serveral Browser in Browser providers exist, however we personally feel more watched than ever when using these. The general recommendation is with Browser in Browser, to never enter any credentials. We share this recommendation.
Providers:
- SquareX
- BrowserStack
- Sauce Labs
- LambdaTest
- CrossBrowserTesting
- Turbo.net
- a8silo.com
Free Hosters
Some only require an email address to sign up.
- https://www.heroku.com/
- https://glitch.com/
- https://replit.com/
- https://render.com/
- https://www.000webhost.com/
Privacy Hosters (VPS, Domain, *coin payment)
Docker Hosters / Playgrounds
- https://labs.play-with-docker.com/
- https://www.katacoda.com/courses/docker
- https://github.com/features/codespaces
- https://replit.com/ (Flask, React, or Streamlit)
- https://coder.com/
Jupyther Notebooks
Nowadays you can access an entire VM instantly, free of charge, only needing a Gmail Address. Here are some examples, what you can do on Google Colab.
Add User
!adduser --quiet --disabled-password --shell /bin/bash --home /home/newuser --gecos "User" newuser
!cat /etc/passwd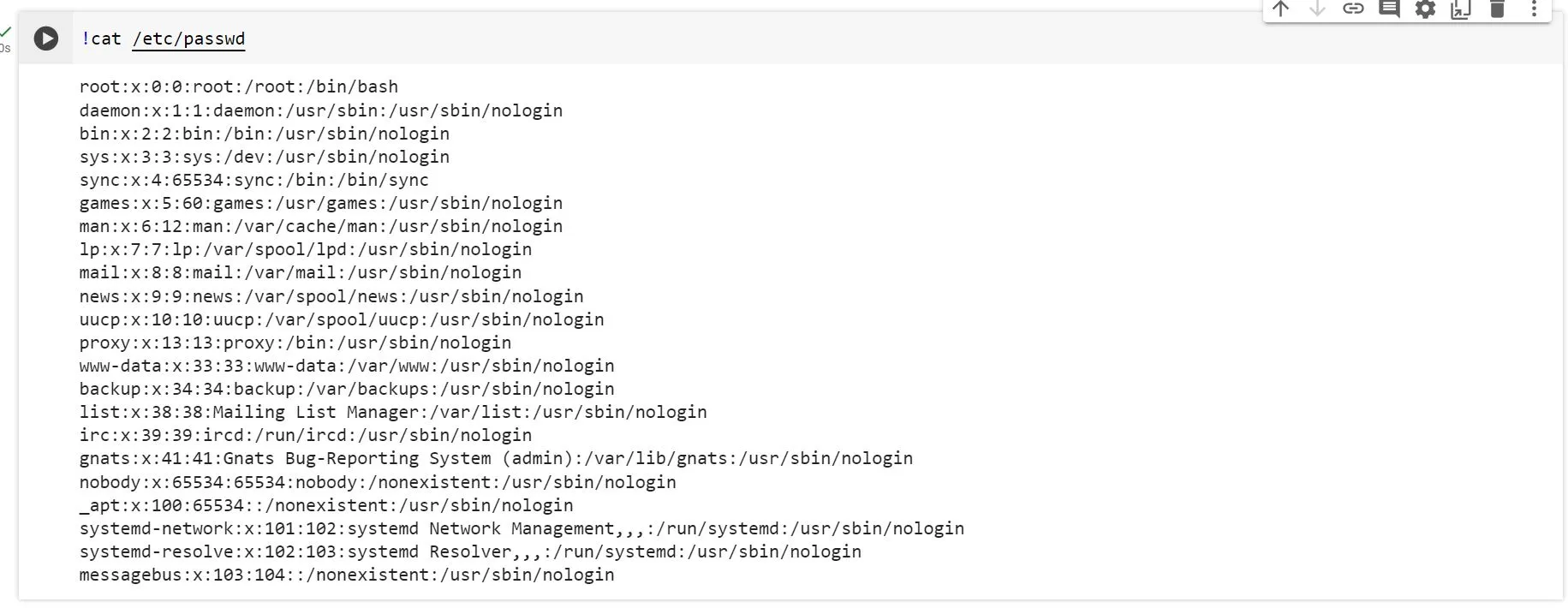
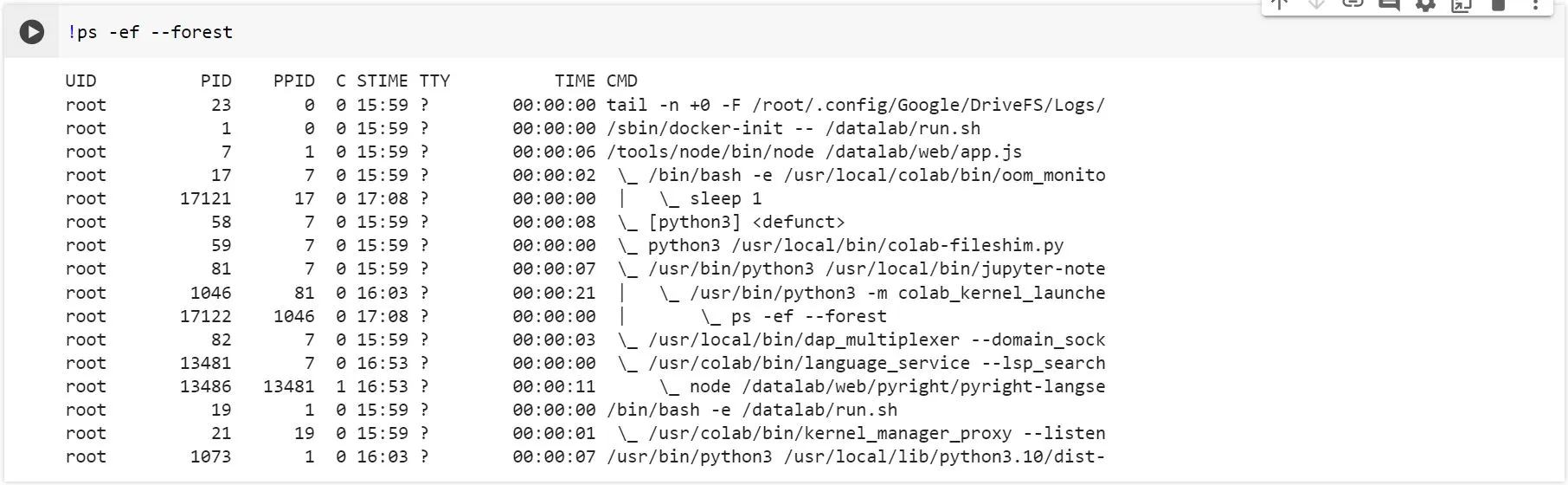
You can do most-things-linux on Colab:
Tor
We’ve not yet tested it, but you could use Colab as TOR proxy-bridge. Meaning, you could host your C2 on an onion server and use Colab as bridge between the DarkWeb and a Victim machine, just proxying traffic back and forth over Colab. As you can reach Colab from the TOR browser, this does make some sense - it’s rather too much than too little OpSec in our book.
!apt install tor
!nohup tor &
!curl --socks5 127.0.0.1:9050 https://ident.me
!curl https://ident.me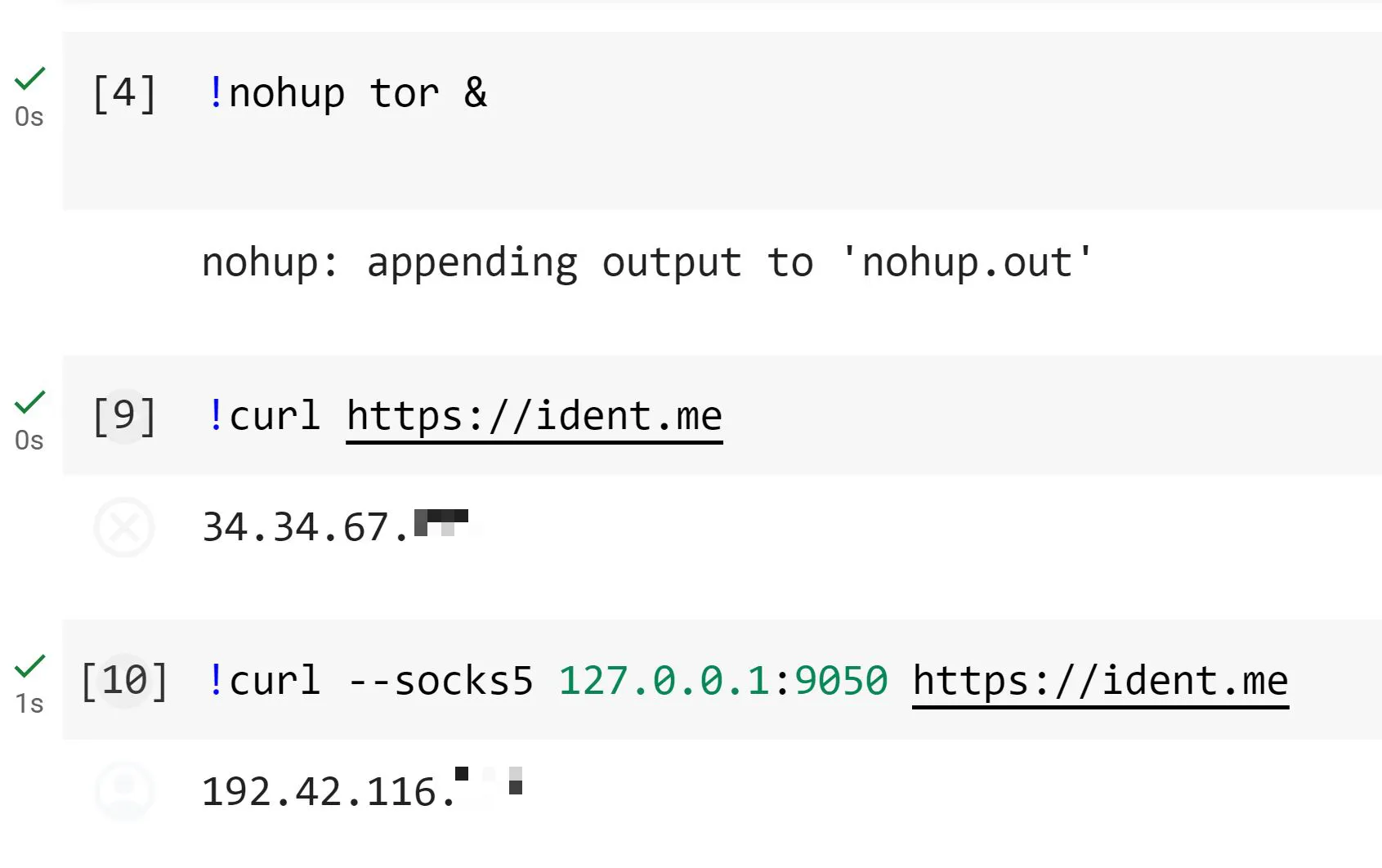
As usual, we don’t want to provide a manual but rather give pointers.
Simplest Server on Colab
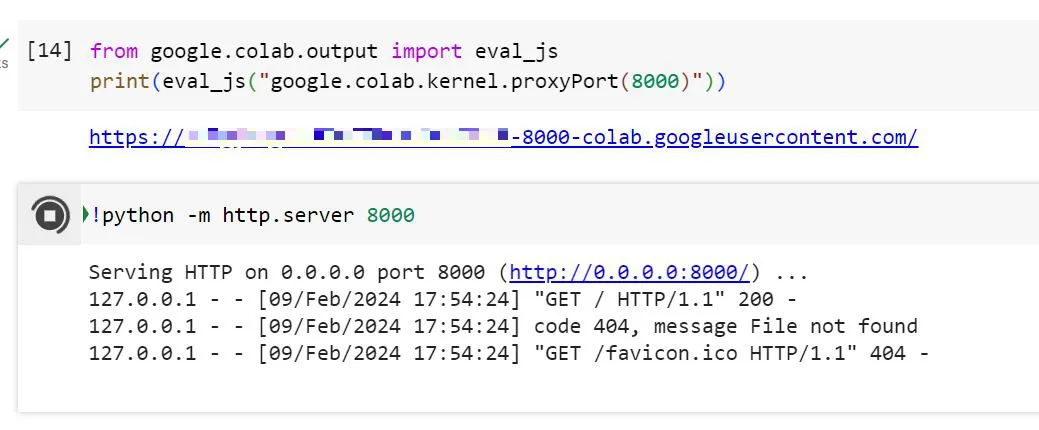
Makeshift HTML Server
Improvising a document-based Server on Colab.
from google.colab.output import eval_js
print(eval_js("google.colab.kernel.proxyPort(8000)"))
# https://................-8000-colab.googleusercontent.com/!echo "hello world" > test.html; python -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
127.0.0.1 - - [09/Feb/2024 17:57:36] "GET / HTTP/1.1" 200 -
127.0.0.1 - - [09/Feb/2024 17:57:36] "GET /favicon.ico HTTP/1.1" 404 -
127.0.0.1 - - [09/Feb/2024 17:57:37] "GET /test.html HTTP/1.1" 200 -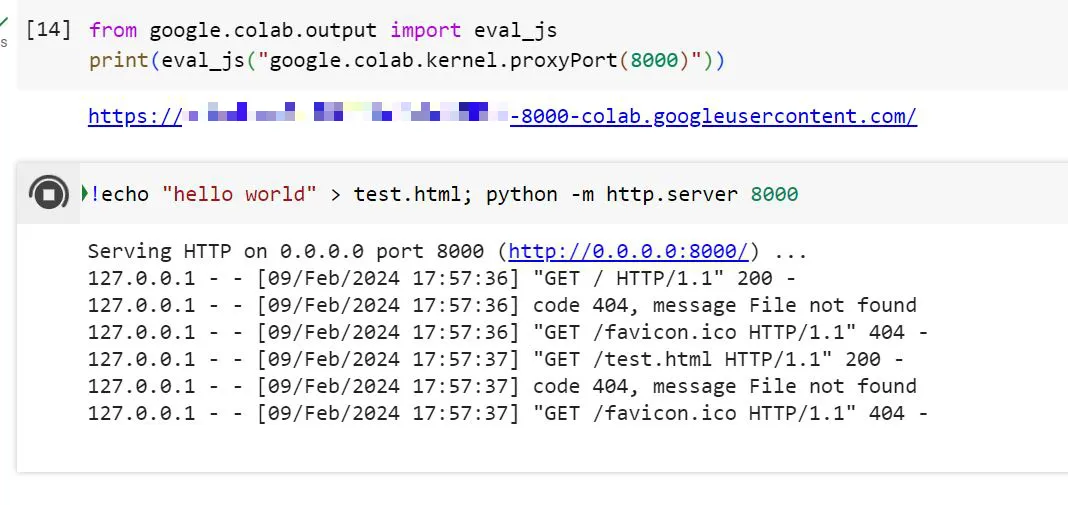
Another Colab Server
https://github.com/Network-Sec/bin-tools-pub/blob/main/simple_python_server.py
Host ngrok tunnel
https://github.com/Network-Sec/bin-tools-pub/blob/main/ngrog_tunnel.py
!pip install pyngrok --quietUsing Tor for Attack Tools
Be careful, TOR has many vulns and vectors. Using it as client is still the most safe usecase today, as long as your traffic is rather “normal” (not bursting scanners and keeping a connection up for hours).
$ tor HTTPTunnelPort 127.0.0.1:9060 SocksPort 127.0.0.1:9050Social Media
Facebook & Instagram
TL;DR: Use Meta App
It gets harder every day to create a fake account. You need a phone number to verify, on top AI / heuristics seems to sort you out even after successful verification - also in the long run, if the account usage appears not normal.
The most easy path as of 2024 is to go over (former) Oculus / Meta accounts (Meta App), as VR is the big push and it’s normal to setup Avatar accounts.
Meta account path even allows for business type of accounts, required for some APIs.
Tipp for Account Creation
A general account creation tipp: Try without VPN - most larger Social Networks not only update VPN IPs in realtime, adding an extra level of suspicion. More importantly:
Lots, if not all, VPN IPs are burned due to over-use by bots.
Find Torrents of private IP
https://iknowwhatyoudownload.com/en/peer/
https://www.abuseipdb.com/
https://talosintelligence.com/
You’d want to check your VPN IP from time to time - you may be in for a surprise. If you’re on a poorly rated connection, you’ll get impossible hoops to jump on account registration.
Random User Generator API
Best AI Image Generators - Stable Diffusion etc.
Fooocus
https://github.com/lllyasviel/Fooocus
Fooocus is probably the best “quick and easy” platform to create high-res, photorealistic, fully AI generated people, face swaps and all kinds of artwork. Easy for beginners.
 Fully AI generated in 10 seconds (second attempt) using
Fully AI generated in 10 seconds (second attempt) using Fooocus, JuggernautXL (latest) model, few minor customizations.
Simple prompt:
Blonde female office worker in her mid-twenties, instagramNo input image (face swap / people mixer) used, Fooocus supports this with 2 clicks. On highres output you can see it usually on the eyes, slight disproportion on the lady in the background.
The takeaway should be here: we put zero effort in this.
There’s Youtube Tutorials aimed at AI Influencers that show Average Joe in 20 minutes, how to get close-to-perfect results, generate batches of real-life images of a “Base model”, at work, on the beach, with friends & family, etc. It’s like a 5-step workflow anyone can master and from there on, generate entire lifes, where you have to really look hard to not be fooled.
No cost, no limits, no restrictions or censorship, anyone can be cloned, including NSFW, if that’s your thing. Or the thing of the Social Engineering victim.
Once emotions come into play, people WANT to believe!
Hardware-wise: We like the gaming laptop as example, everyone can understand. As far as we know, CPU-only is also supported, having less strong hardware doesn’t mean, worse results. It only means, the creator needs more patience, but since it’s all automated, you can watch Netflix while it’s generating.
ComfyUI
https://github.com/comfyanonymous/ComfyUI
ComfyUI is more powerful, but needs more skills and time. Allows for automation, build your own batch people mixer with 4k output, endless features. If you can master it, it’s a game changer.
Both allow for many, free models you can download from HuggingFace or https://civitai.com/models/ and lots of 3rd party extensions, like IP Adapters and ControlNet, you can plug in Ollama to generate text prompts, there’s an entire Audio Nodes section. You can easily create a workflow for automated background removal and upscaling for thousands of photos and much more.
Note: Most AI tools need a powerful GPU to run, you’re best of with CUDA - meaning Nvidia - on Windows. OpenCL has made progress in many areas, but right now nothing beats a 4090 on Windows 10. We also can’t recommend the classic Automatic1111 Stable Diffusion WebUI as it couldn’t keep up with the other projects, has some unnecessary complexity, essentially trying to do ComfyUI stuff in a WebUI interface. With the rise of new features and methods, like IP Adapters, the UI format was kinda outgrown.

We didn’t just create this demo picture. We setup a workflow, that created about 1000 of them, same style, male, female, variations and all with automatic mask creation as separate PNG (black / white alpha masking), along with another copy, that has the mask integrated as alpha channel.
Krita AI Diffusion
The latest version of the FOSS Photoshop Clone comes with an amazing plugin that allows to use ComfyUI in realtime within painting mode. It’s like Adobes AI fillers, just better, more customizable and free. It can install it’s own copy of ComfyUI with one click, meaning you don’t have to be a Diffusion Pro to use it.
Realtime AI Video Face Swap
https://github.com/C0untFloyd/roop-unleashed
https://github.com/taicv/roop-unleashed
https://github.com/hacksider/Deep-Live-Cam
Uncensored face-swapping for images and videos without training with an easy-to-use GUI.
Based on roop. Allows for realtime video conferencing, using for example OBS Virtualcam. Just plug in a photo, get the stack going and join that Teams or Zoom meeting as someone else.
Can’t remember 100% which version of OBS we were using eventually, but you can try either:
- obs-ndi-4.13.2-windows-x64-Installer
- obs-virtualcam-3.1.1-windows-x64-Installer
It’s been a bit, since we last used it, if we recall correctly, you had to use an older version of OBS that you could install in parallel to the current one.
Realtime Voice Conversion (Pro Edition)
https://github.com/RVC-Project/Retrieval-based-Voice-Conversion-WebUI
Only chinese docs, needs a bit of work, to install correctly. Due to space constraints we installed a Miniconda environment into the same folder.
Some of the steps:
# Preps
$ conda create --prefix ./conda_env python=3.10 -y
$ conda activate ./conda_env
# We made a conda env in same folder, so "pip install ..." command would
# actually be ".\conda_env\python.exe -m pip install ..." - reverted for simplicity
# Download and more preps
$ git clone https://github.com/RVC-Project/Retrieval-based-Voice-Conversion-WebUI
$ pip install --upgrade pip setuptools wheel
# Install and verify working torch + CUDA
$ pip install torch==2.3.1+cu121 torchvision==0.18.1+cu121 torchaudio==2.3.1+cu121 -f https://download.pytorch.org/whl/torch_stable.html
# requirements.txt needs an edit or it will fail: -> "PyYAML>=5.1"
$ pip install -r requirements.txt --use-deprecated=legacy-resolver
# Some deps need workarounds - downgrade pip
$ pip install pip==23.3.1
$ pip install omegaconf==2.0.6
# Fix for Model training fail
$ pip install matplotlib==3.9.4
# Downloader may need some manual editing if it fails along the way
$ python .\tools\download_models.py
# Alternatively, you can search yourself for models etc.
$ git clone https://huggingface.co/lj1995/VoiceConversionWebUI/
# Ready to go
$ python infer-web.py --pycmd conda_env\python.exe --port 7897Train your own Voice model
https://www.youtube.com/watch?v=nXpBlC6OBw4
First, go to the Train tab, then follow these steps:
Step 1: There you give the experiment a name, set the same rate to match your voice samples and optionally adjust the CPU settings for your system.
Step 2a: Here you select the path to the folder where your voice samples are located, they should be minimum 10 minutes long but ofcourse long and good quality is always better. Then just press Process data and wait till it says end process.
Step 2b: Leave everything here at default if you don’t have more than 1 GPU, then just click Feature extraction and wait till it says all-feature-done.
Step 3: Set Save frequency to 50, you can play around a bit with Total training, we would recommend ~150-250 depending on how much time you want it to take and how accurate it should be. Batch size is also dependant on your GPU and how much of it you want to use. Also change the save a small… option to yes. Everything else we would leave at default. Now you can just click Train Model. After a hour or two depending on your system you can now use your own new voice model.
Download Models
If you dont want to train your own voice model you can find other voice models here or by searching on Google using the term RVC and the name of the person:
After unziping the downloaded model move the .pth file to
\Retrieval-based-Voice-Conversion-WebUI\assets\weights\and the .index file to
\Retrieval-based-Voice-Conversion-WebUI\logs\`Now refresh voice list and your already able to select the downloaded voice from the dropdown bar. Everything else here is pretty self explanatory and we haven’t figured out the best presets yet, so try it out for yourself.
elevenlabs
https://elevenlabs.io/app/speech-synthesis
https://github.com/elevenlabs/elevenlabs-python
Both premade as well as custom made voice models with quite a bit of free quota to begin with.
Business Name & Logo Generator
Create Website NoCode
AI Website and Webapp Generator
That’s truly a great one. Free version will produce complex projects that are actually usable!
Honestly, whenever “Hackers” in 2024 still mention the classic Social Engineering Toolkit - for anything but historic purposes - a tool that “cloned” website frontends, before the age of TLS and Webapps, something feels a tiny bit off.
See above for more AI tools, to generate realistic people, clone your face on live video, etc.
Create Account images
- https://imagine.meta.com (Needs USA IP, try New York)
- https://this-person-does-not-exist.com/
- https://www.playform.io/facemix
- https://futuresight.org/webprojects/peoplemixer
CrossLinked
https://github.com/m8sec/CrossLinked
Basically a username / email / AD login generator.
Freemail Providers
| Country | Notable Freemail Providers |
|---|---|
| Germany | GMX, Web.de |
| United Kingdom | Gmail, Outlook.com, Yahoo Mail |
| United States | Gmail, Outlook.com, Yahoo Mail, AOL Mail |
| Switzerland | ProtonMail |
| Russia | Yandex.Mail |
| Netherlands | KPNmail (more business-oriented now, but has a history with free email services) |
| Sweden | Loopia (also more towards web hosting but offers email services) |
| Portugal | Sapo Mail |
| Italy | Libero Mail, Virgilio Mail |
| France | LaPoste, Orange Mail |
| Spain | Telefónica (Movistar) offers email services, though they’re more integrated with their other telecom services nowadays |
A Few Points to Note:
- Libero Mail and Virgilio Mail: Popular in Italy, offering services in Italian with a suite of features that cater to local users.
- Sapo Mail: A well-known provider in Portugal, offered by the Portuguese company Sapo. It’s in Portuguese and caters specifically to the Portuguese-speaking population.
- LaPoste and Orange Mail: In France, these providers offer services in French, with LaPoste being the national postal service that also provides digital mail services.
- Telefónica/Movistar: While primarily a telecom provider in Spain, it offers integrated email services for its users, reflecting how telecommunications companies in some countries provide bundled services including email.
Without phone verification, the next best options are ProtonMail and Microsoft Live - you can use one to verify the other, but you should definitely let time pass between, subscribe to some newsletters, generate a bit of mail traffic that appears normal - otherwise you’ll be hit quickly with an automated ban.
Both, a clean Android phone as well as a new Windows Installation will allow you to create GMail resp. Outlook accounts, without need for verification number.
Privacy Focussed Email Providers
- ProtonMail
- StartMail
- Tutanota
- mailbox.org
- privateemail.com
Domain Fronting
CloudFlare should be well-known. As you can get a free account with nothing more than an Email address, you can setup quite a high hurdle there. As with most things in OpSec: We wouldn’t steal the Queen’s Crown Jewels, solely depending on such a setup. For any legal gig, that someone maybe misinterpreted (there are enough people who think Responsible Disclosure is still a crime), it should be a high-enough protection, as long as you don’t make other OpSec mistakes.
Other Vendors offer similar services, e.g. AWS and Azure. Consider layering each step in your Offensive Infrastructure, like additional Jump Hosts, Proxies, disposible containers with a Forwarder… your creativity is the limit.
Email Fronting
TL;DR: Use CloudFlare's Mail forwarding to simulate a custom Domain Email - works in free account!
Other than that, we don’t know of any option to reliably protect your@custom.domain Mailserver like Cloudfront does for your Website’s IP. For the time being, we use mostly Freemail providers, or switch on/off custom domain mail, when we absolutely need such an address for certain services - meaning to turn off Domain Fronting and creating all needed Records to the true IP for a limited time period. These days, for working Email even the main domain needs to point to the correct IP, so you would need to turn off even Website Fronting temporarily.
If you have a little more budget, you can of course get another IP and setup Mail Exchange with a cloud IP - but you’ll have to pay constantly.
In case of money is not an issue best options are Outlook or GSuite Business.
Bypassing SMS Verification
We found this service in several bots of a Bad Actor - we haven’t tested the service and are not entirely convinced of it’s legitimacy.
SMS Verification and more
Provides updated list of various services that can be payed with crypto. Untested.
SendSMS Services
We left out Free Receive SMS services on purpose here, cause they’re a huge OpSec risk and most of the time don’t work for account registration. Also they’re only a Google search away. Providers pop up and disappear regularly, you can see all received SMSs publicly, which often includes private information. For account creation, save yourself the time and get another SIM.
SIM Cards
in Europe without ID:
- Lebara Netherlands - check that the card is preloaded with cash or you’ll need to top up and thus make another account connection
- Lycamobile Shops - untested, but rumors has it that some shops trade activated cards behind the counter
- Buying activated and charged cards on
eBay- While it’s an option, it’s not risk-free:
1.) You need an eBay buyer account, that again is hard to achieve anonymously
2.) You don’t know the seller. It could be a secret service or a criminal selling you his usedSIM - Stolen cards - we certainly don’t mean to suggest to do that, it’s just an option criminals use
SIM Country overview
| Country | EU Act for Mandatory ID | Practical Situation (ID requirements) |
|---|---|---|
| Austria | Yes | Passport or national ID required |
| Belgium | Yes | Passport required |
| Croatia | No | No ID required |
| Denmark | No | No ID required |
| Finland | No | No ID required |
| France | Yes | Passport or national ID required |
| Germany | Yes | Passport or national ID, sometimes address proof |
| Greece | Yes | Passport or national ID required |
| Hungary | Yes | Passport required, annual verification for prepaid SIMs |
| Iceland | No | No ID required |
| Italy | Yes | Passport required |
| Latvia | No | No ID required |
| Lithuania | No | No ID required |
| Netherlands | No | No ID required (Lebara, general situation unclear) |
| Norway | Yes | Passport required |
| Poland | Yes | Passport required |
| Romania | No | No ID required |
| Slovakia | Yes | Passport required |
| Spain | Yes | Passport required |
| Sweden | No | No ID required |
| Switzerland | Yes | Passport required |
| Turkey | Yes (for stays over 120 days) | IMEI details, sometimes passport required |
| United Kingdom | No | No ID required |
Free SIMs
(physical / eSIM, not virtual)
- https://gmx.net/handy/freephone/ (3GB free traffic, no hidden cost atm)
- https://www.netzclub.net/ (200MB traffic, EU-wide 25MB/s speed advertised, ad-sponsored)
Though ID required for registration, free is still attractive, depending on usecase. We often make OSINT accounts, where we don’t need to be truly anonymous, yet don’t want the other party to recognize our number, so: free is always great. We used Netzclub over a decade ago when we couldn’t afford a better SIM, and to be honest, you kinda expect that the ad-sponsoring will become the issue, however you only received an ad SMS from time to time - the real issue was the bad reception. It was long ago, things might have changed.
Bypass PlayStore ID check
https://f-droid.org/packages/com.aurora.store/
Ususally you can use Google PlayStore pretty anonymously. But for certain apps, like Telegram you will get stuck on Age Verification - which will ask for some type of ID or payment method, that again will provide a way to ID yourself.
To bypass Age / ID Verification Check on your OSINT device, you can use F-Droid in combination with Aurora Store - the later even has an anonymous login. It may not work on first attempt, but eventually it does. Using those two we were able to get most apps, including Termux, even onto our Meta Quest.
Deception
Some tipps, how to move.
1. Strict account separation: - if you got DarkNet Research accounts, don’t mix them with your personal accounts, or your BugBounty VPN. Harder than it sounds, but the new Chrome profiles feature can work in your favour, as well as Browser Extension based VPNs.
2. Take cover: - When creating a fake identity, immitate believable characters. E.g. for research you could make an account that looks like it was created by a private investigator, using the PI’s neighbours name and address, so it looks like the PI tried to create that fake account.
3. Fingerprints: - Don’t ignore smaller factors like Browser Fingerprinting, while focussing maybe too hard on your current IP address.
Some criminals also hack real accounts for OSINT and OpSec purposes, which we definitely wouldn’t recommend (but have wittnessed it several times, in attacks on us).
Nevertheless, trying to match someone else and the intentions they might have for the action will give you an enourmous benefit, leading investigators on a false trail.
However: Make sure you don’t cross the thin line into real Identity Theft. It is a lot harder to invent someone than it is to steal (copy) their identity, yet the later is a crime, while the further can be argued to be intended as pseudonymity. When copying real people, you practically frame someone, a real person who might already have enough problems in life and certainly isn’t amused being investigated. That’s why it is a no-go for us, yet we know for a fact that many Offensive Security (black, grey or white) don’t share the same view on the matter and prefer the easier route.
Payment
in Europe without ID
- Cash
- Bitcoin ATM
- Revolut App
- Other one-time Credit Card services
- Giftcards
- Paysafecard
- Private transaction (risky, even if you know the person)
Revolut and similar Services
Revolut offers onetime and virtual credit cards, CryptoCoins and exchange. Requires ID to register, but virtual CC are right now the best option we found to pay pseudo-anonymously for services.
Giftcards
Giftcards can also be used to charge Google PlayStore and thus use services that accept this payment (e.g. VPN). With payment you often need to think outside the box, but eventually you can find ways.
Note: Google Play credits are bound by country, meaning the country of the SIM Provider and the Play Credit must match, or you won’t be able to charge.
Once again the reminder, the thing about OpSec is: It’s relative. Given enough resources, our planet is small enough to eventually identify everyone and tie them to an operation. So the real question should probably be: How much resources is my operation worth, to the investigative side.
Used by Larger Crime Operations
- Hawala Banking - https://www.investopedia.com/terms/h/hawala.asp
- CryptoCoins - Ransomware’s favourite still - they use coinmixer services, accounts stored on the blockchain, fake IDs and money mules for cashing out
- Playstore Giftcards - prefered by scammers (i.e. Microsoft Support Scam)
- Western Union - no longer used as much
- Sending cash in a box - Some fraudsters use this method, trying to re-route the packet en-route several times by calling the driver, using cash mules to pick it up, etc.

While you can use Giftcards for legitimate privacy and OpSec, they’re used by Fraudsters for the same reasons: they’re hard to trace.
Giftcard Money Laundering Scheme
Recently we were made aware of more pathes, how Giftcards are being abused: Steam Giftcards seem to be now prefered by illicit “traders” as payment method - we were wondering, if the trader then goes ahead to sell the Giftcards on eBay. This already would be a form of Money Laundering, but it would also enable Investigators to search for local vendors of Giftcards on eBay and check what they’re up to.
The more sophisticated version of Giftcard Laundering goes by creating fake games on Steam - entire projects of trash games, which the Giftcard owner then buys himself.
Coins and anonymity
Coins are traceable. Monero is the most anonymous coin, it’s recommended to use:
- Lots of intermediate accounts
- Lots of time
to counter deanonymisation by various attacks like EAA.
However: That goes far beyond Average Pentester’s ability. Furthermore, Monero is highly impracticle for regular Cybersecurity Operations, cause unlike BitCoin, you hardly can buy anything with Monero.
We left this information here only for the sakes of completeness and to provide a first contact with the world of Crypto. It’s definitely fun, but TL;DR: when you don’t do it for learning purposses, use Revolut or another, official Exchange instead.
Get Monero Wallet
https://web.getmonero.org/generator/
What is a wallet
- Monero Public Address: The public address is used to receive funds to the wallet. You give this to anyone who will be sending funds to your wallet.
- Monero Mnemonic Seed: The mnemonic seed is a method of storing the entire wallet that is easily recognizable to humans. This is all you need to restore your wallet at a later date.
- Monero Spend Key: The private spend key is used to send funds from the wallet.
- Monero View Key: The private view key is to view transactions entering the wallet. Commonly this is used to setup a view-only wallet which can see incoming transactions live on the blockchain as they are sent to a cold storage wallet.
Signature File
binaryfate key
https://raw.githubusercontent.com/monero-project/monero/master/utils/gpg_keys/binaryfate.asc
Verify Wallet
$ gpg --import binaryfate.asc
$ gpg --verify wallet-generator.html.ascMining
In theory, Coing Mining is a great option to generate money anonymously - however, practically you’ll convert energy-cost to coins at a rate of 100:1, if you don’t fail at any step. We did.
XMRRig
https://github.com/xmrig/xmrig/releases/download/v6.21.0/xmrig-6.21.0-gcc-win64.zip
https://github.com/xmrig/xmrig-cuda
Minerstat
Attacks on Monero
https://link.springer.com/chapter/10.1007/978-3-030-14234-6_5
Ecosystem Analysis Attacks (EAA)
Input Clustering
Assumes that all inputs of a transaction are controlled by the same entity. Exploits the fact that transactions often combine outputs from previous transactions controlled by the same user.
Output Amount Analysis
Before Monero implemented RingCT (Ring Confidential Transactions), transactions had visible amounts. Analyzing output amounts could potentially link transactions.
Timing Analysis
Transaction Timing
Looking at the timing of transactions to correlate them with user activity. If certain transactions consistently occur around the same time, they might be linked to the same user.
Ring Signature Attacks
Intersection Attacks
If a set of transactions shares a common set of mixins (the decoys in a ring signature), one might infer that the real spender is involved in all transactions.
Guess Newest Heuristic
Assumes the newest input to a transaction is the real one being spent. Early implementations of Monero might have made this heuristic more effective due to less sophisticated mixin selection strategies.
Blockchain Analysis
Chain Reaction
By identifying a single real output, an attacker might trace a chain of transactions backward or forward, potentially revealing other real outputs (less effective with improvements in Monero’s privacy features).
Knapsack Analysis
Early versions of Monero used a variation of the knapsack problem for ring signatures. This could potentially be exploited to deduce the real input among mixins.
Network-Level Attacks
Node Sybil Attack
Running multiple nodes to try and correlate transaction broadcasts to IP addresses. Monero’s use of Dandelion++ aims to mitigate this by obfuscating the propagation path.
Decoy Selection Flaws
Biased Decoy Selection
Early versions of Monero had less sophisticated decoy selection, which could make real inputs stand out more. Improvements have been made to make decoy selection more random and representative of the actual distribution.
Quantitative Analysis
Statistical Analysis of Ring Members
Statistical techniques to analyze the distribution and selection of ring members over time, possibly identifying patterns that reveal real inputs.
Monero has been constantly evolving to address these vulnerabilities, including implementing RingCT, improving the sophistication of decoy selection, and adopting Dandelion++ for network-level privacy. The arms race between privacy preservation and deanonymization techniques continues, with Monero developers actively working to stay ahead of potential vulnerabilities.
TTP
We’ve seen in countless cases, that criminal operations have adapted. They use similar methods as legitimate investigators, like OSINT, surveillance teams, GPS trackers and more.
On top, they have another toolbox containing illegal methods, like hacking, social engineering, bribery, blackmailing or threats - which enables them to access insider information, for example to do GSM tracking of a victim, via a partner inside a telecommunication company.
Where to go from here
Practical Cybersecurity can be a high risk profession, depending on your field.
In this lengthy article we took a superficial look, how serious OpSec is conducted. Of course, there are many more details and facettes to it, but it should give you a quick overview, what you’re actually dealing with.
Dark vs Light
In conclusion, indicators for investigators to tell good vs bad are Fake IDs, stolen SIMs, stolen Credit Cards or stolen devices, as well as Identity Theft. On the technical hacking side of things, we would suggest to draw the line at Info-Stealers, Cryptors, installation of real / long-term malware and services monetizing on unauthorized hacking. Operationally, we wouldn’t recommend to cross over into accessing private information intentionally, leaking data or any type of larger operation, that clearly does not focus on improving security.
One mayor issue we see with the current practice of Responsible Disclosure is the fact, that you can’t know that you’ll find anything, before you actually test it. This puts researchers doing unauthorized scans into a potentially bad position, leaving them with no fallback to prove their good intent, for the case when they don’t find a serious vulnerability.
Another issue, that we all know from the movies: when you start moving on the dark side, your white shirt will get stains, no matter how disciplined or how high your ethical standards are. Only the fact that you work beyond the line will be enough for some people to see you with prejudice and no longer trust you, while the reality of course is other way round (you’re at least transparent about what you do). When you openly announce that your job is for example “researching on the darknet”, any future mistakes you make - including small things like using rough language - will automatically be attributed to that (see also: List of human falacies - Halo Effect, Social Profiling).
Of course, it’s not like saying you’re a Hacker, who’s working on Rootkits in your spare time, won’t make Average Joe and Jane run away screaming in fear and panic anways, so… :D
Time will tell, if policy makers see things the same way - recent changes in german anti-hacking laws provided us with some hope, that they’re starting to catch up with the reality of IT security, while on the other hand, 2024 UN regulations brought to us by “countries with a little bit of communist roots” are a major setback for all Cybersecurity professionals.
This information is intended to create awareness, how real criminal activity is conducted, so you can defend against it. On top, we hope to help protecting your legitimate Cybersecurity Operations and for the most part, wanted to show that:
Real hacking is not a game.