Published
- 2 min read
Pentesting Flowchart for WebApps and CTF

Pentesting Flowchart
Take a look at our Pentesting Flowchart. They’re a bit aged but I think they still hold up for the bread-and-butter pentest.
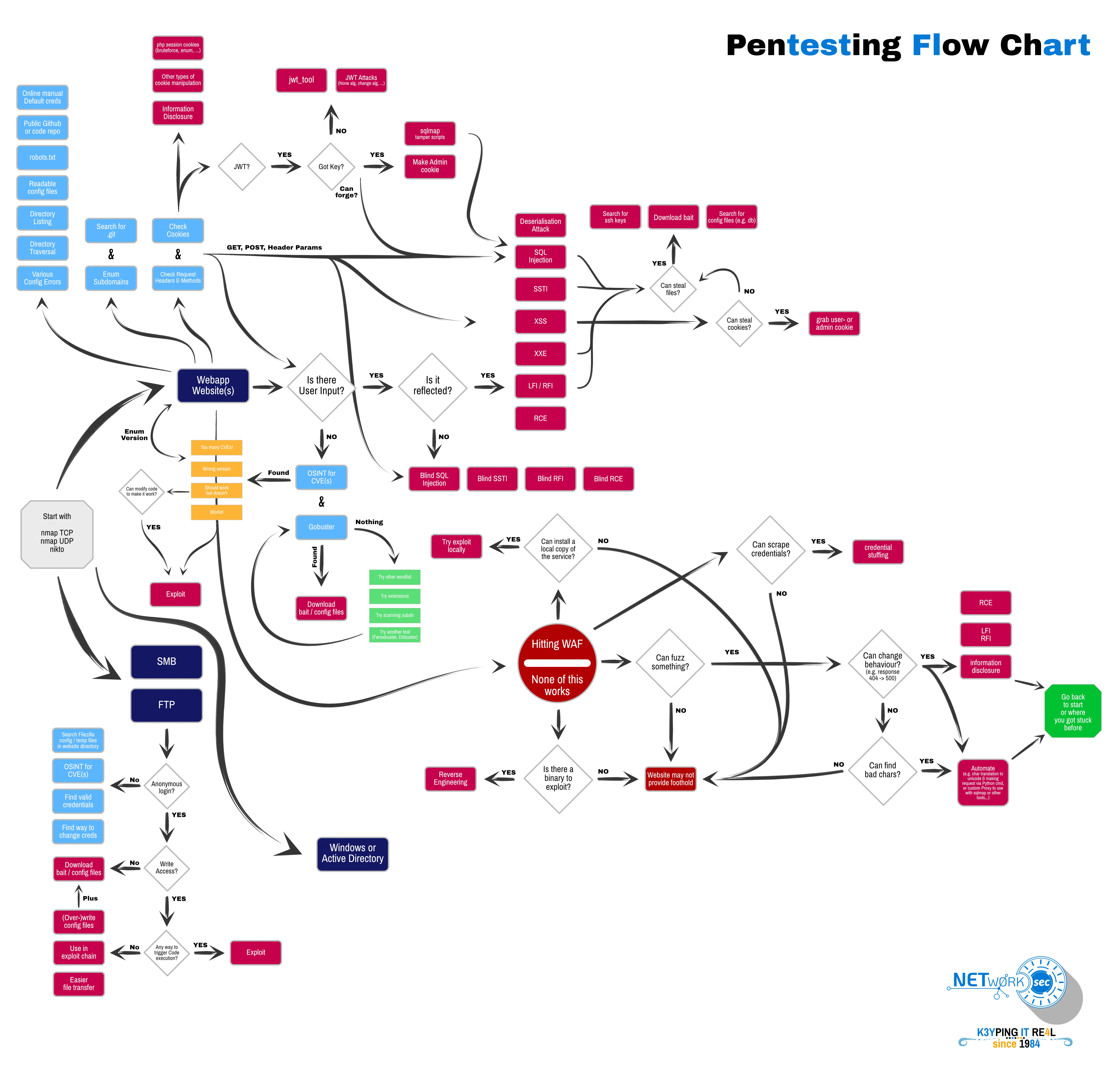
Of course, you could go in much more depth (I know there are fantastic flowcharts out there hugely better than this one) and it misses out on Active Directory aside from the complete basics that happen to overlap with WebApp testing. But it does get you started and may help when you’re lost in between.
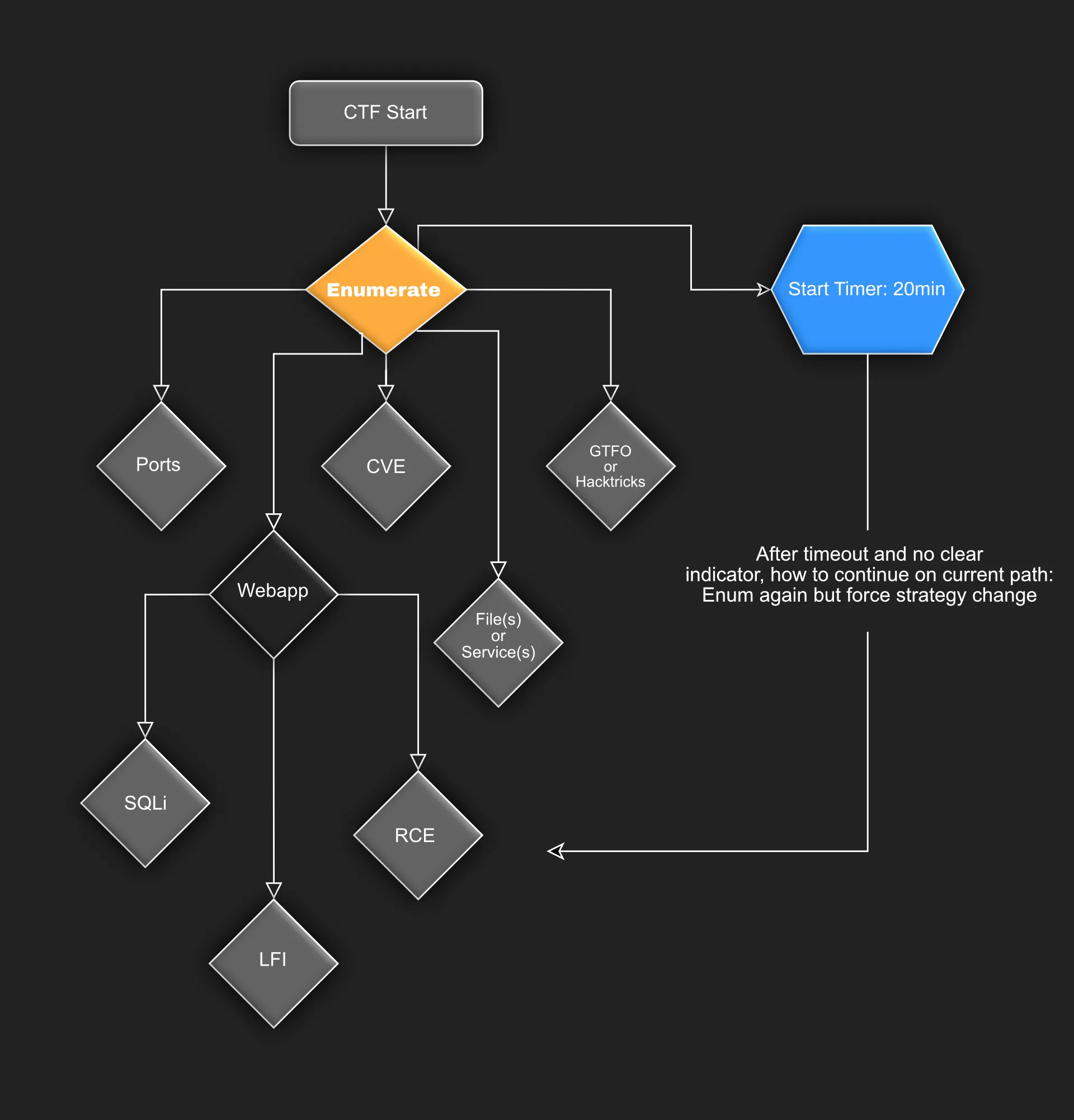
CTF Flowchart - When you tend to overlook a lot
while investing too much time in a potential rabbit hole (like me): I came up lately with this strategy. It can be applied generically to any Pentest or CTF, no matter if it’s a Webapp or AD - probably not for things like Crypt, Physical, SE or BinEx, which require more head- and less leg-work.
The branches are more of exemplary nature. The timeout will provide a neat function: Let’s assume, in 20min you’re not able to find 100%, but a good 95%. Yes, you’ll miss the final 5% that way, the harder stuff, the blind boolean time based ladida. But you can test very broadly and will hardly overlook obvious stuff anymore, the things that really piss you off, when you finally ask for a nudge or check a writeup.
For this to work there are at least two things important:
- Document your approach neatly, so you avoid duplicate attempts - and wasted time
- Test thorougly. When you look at all files through an LFI - then look at
all files, so you can cross it off
Quote of the day
“When you differ from the norm, how you are, behave or do things, only like 1 or 2 degrees, people will completely disregard you, noone will understand you, some may even hate or talk shit about you - unless your difference becomes popular.”