Published
- 3 min read
Want a cool tool + every CVE, PoC & Wordlist in Existence - Always Up To Date?

We shouldn’t tell you about this GitHub Repository - we also shouldn’t share the tool, that creates and updates it. Cause both will give you a huge advantage over your competitors.
Trickest
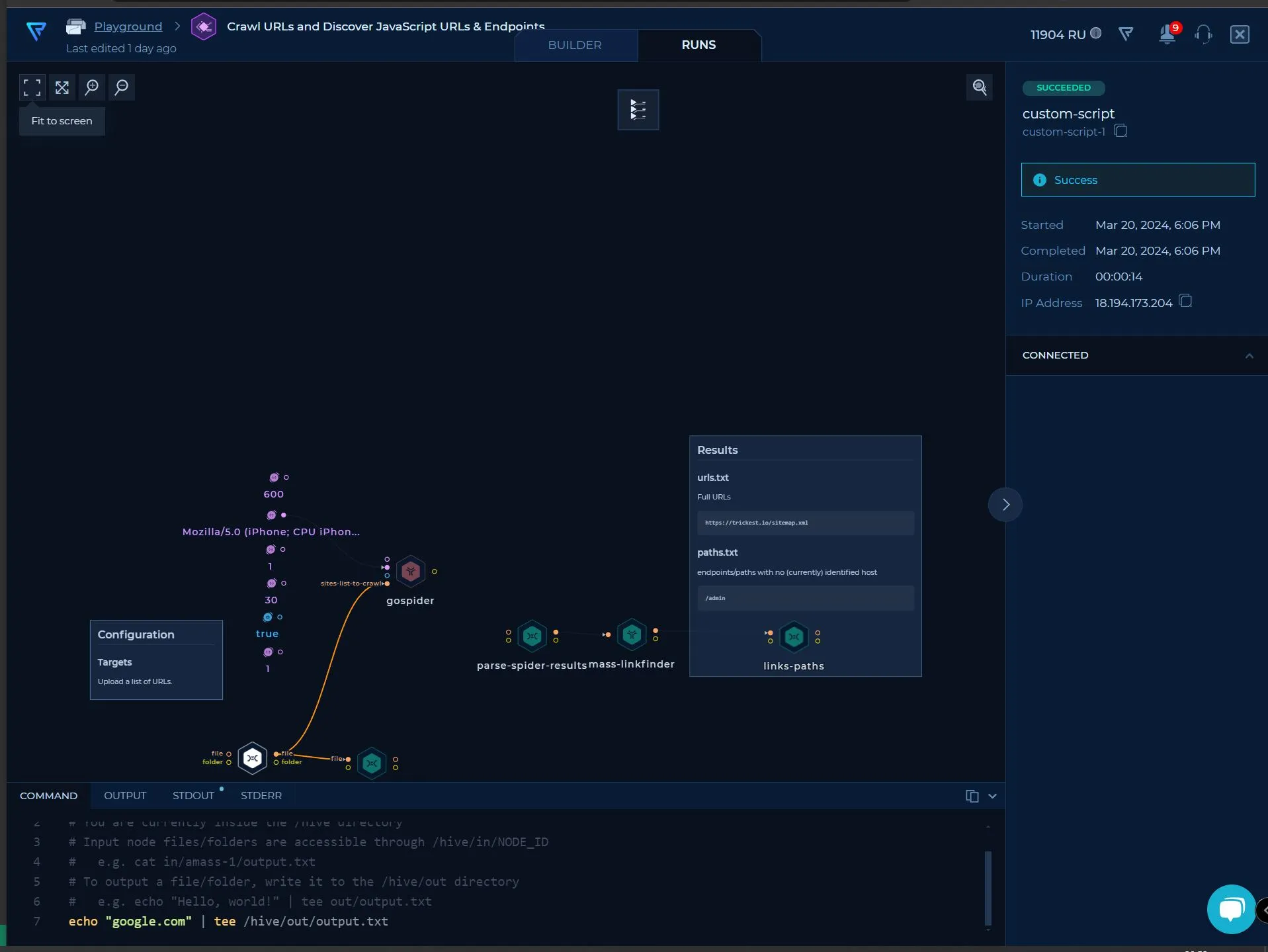
On the surface is Trickest just an Offensive Security Automation tool - it’s pretty cool: Node-based workflow, bash scripting, lots of templates and ready-to-use scanners, filters, and more.
The true, overwhelming power however becomes obvious, once you browse the repo, that Trickest creates and updates regularly. It holds:
- All CVEs of the last 2 decades
- All their PoCs and sources, most are compiled, ready-to-use
- Wordlists
- All Cloud
IPs - Insiders - BugBounty info you hardly can find anywhere else (if BugBounties were Stocks, these infos would be illegal)
and more. All while it’s always up to date. Impressive. It gets even more fun, when you follow into the stuff users created with Trickest and again, shared on GitHub.
Check it all out
literally. Here are couple of our one-liners we use to automate mirroring this sheer capacity into our own archives.
Extract all Urls
After cloning all Trickest CVEs locally, enter one of the year folders, e.g. 2023. Then run these:
Extract all GitHub PoCs
$ grep -Ri "#* github" -A 1000 | grep -Po "https://github.com/.*" | sort -u > all_github_PoCs.txtNote that only some of the PoCs reside on GitHub, other are blog articles or in other archives, Google Drive, Social Networks… we ignore them for now, but you could easily adjust the scripts.
Download all PoC Repos
$ for repo in $(cat all_github_PoCs.txt); do GIT_TERMINAL_PROMPT=0 timeout 120s git clone "$repo" || echo "Failed to clone $repo or it took too long. Skipping."; done;Extract all GitHub PoC Usernames
So you can use the one-liners below to clone all of their work.
$ grep -Ri "#* github" -A 1000 | grep -Po "https://github.com/.*/" | sort -u | cut -d "/" -f 4 > all_github_PoCs_Usernames.txtCheck out all Repos from User
$ username="<..github username...>"; [[ ! -e $username ]] && mkdir $username; cd $username; for repo in $(curl -s "https://api.github.com/users/$username/repos?per_page=1000" | grep -o '"clone_url": "[^"]*' | awk '{print $2}' | tr -d '"'); do GIT_TERMINAL_PROMPT=0 timeout 120s git clone "$repo" || echo "Failed to clone $repo or it took too long. Skipping."; done; cd ..;Check out all Gists from User
$ username="<..github username...>"; dir="${username}_gists"; [[ ! -e $dir ]] && mkdir -p "$dir"; cd "$dir";curl -s "https://api.github.com/users/$username/gists?per_page=100" | jq -c '.[] | {file: .files | to_entries[0].key, raw_url: .files | to_entries[0].value.raw_url}' | while read -r gist; do file=$(echo $gist | jq -r '.file' | tr '.' '_'); raw_url=$(echo $gist | jq -r '.raw_url'); mkdir -p "$file"; wget -O "./$file/${file}" "$raw_url"; done; cd ..Conclusion
We should’ve kept this for ourselfs. But we didn’t. Have fun - do good with it.