Published
- 2 min read
AMSI in pictures

Intro
When I studied AMSI evasion I was asked to make a little presentation - I probably didn’t do a good job, cause they never let me finish or present it.
But in this context, I made these two images.
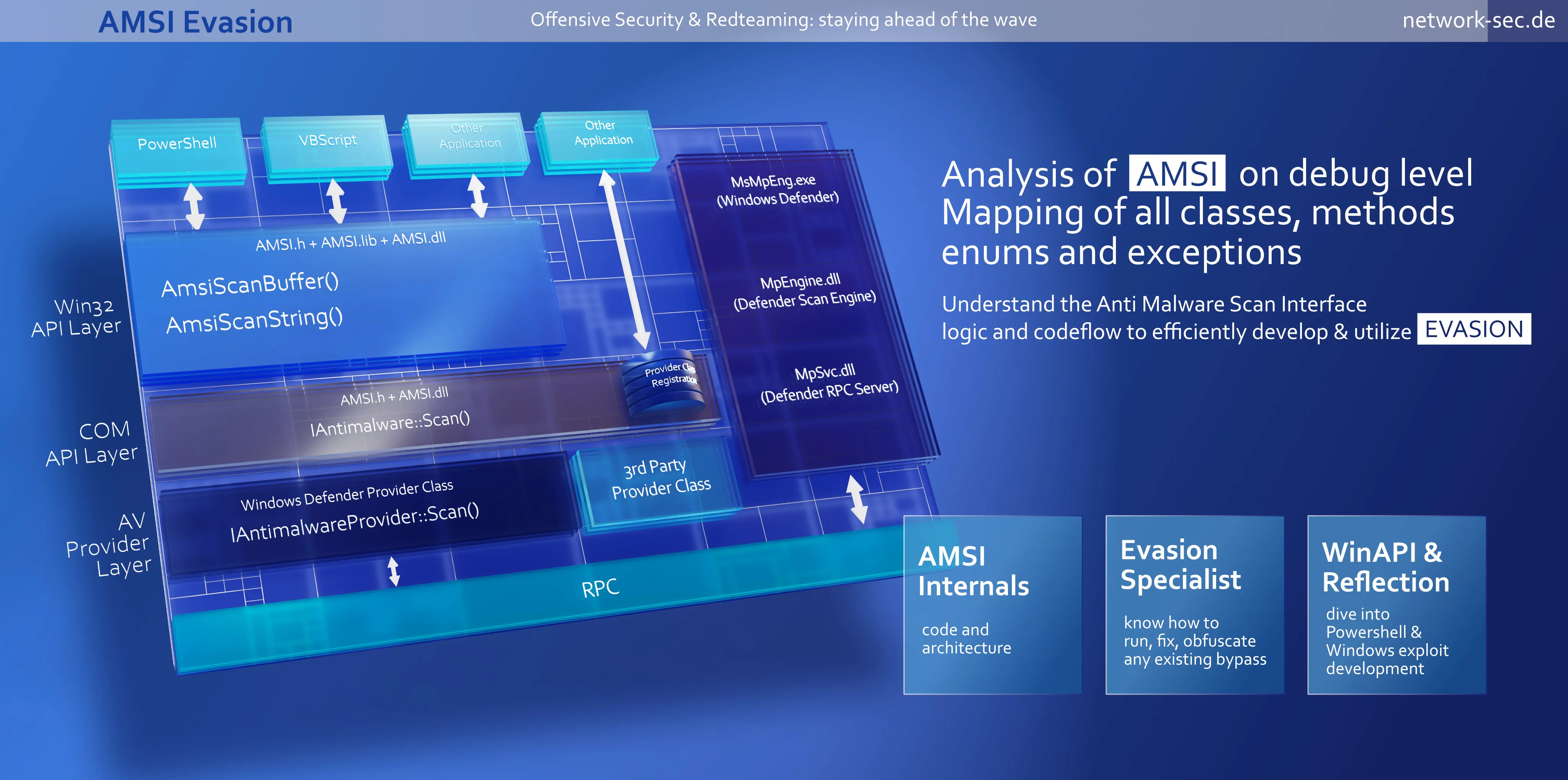
Architecture Overview
The first is just a mockup of a Microsoft architecture diagram. I added some shameless self-marketing on top.
How AMSI works
In the second one I tried to visualize, how AMSI works under the hood.
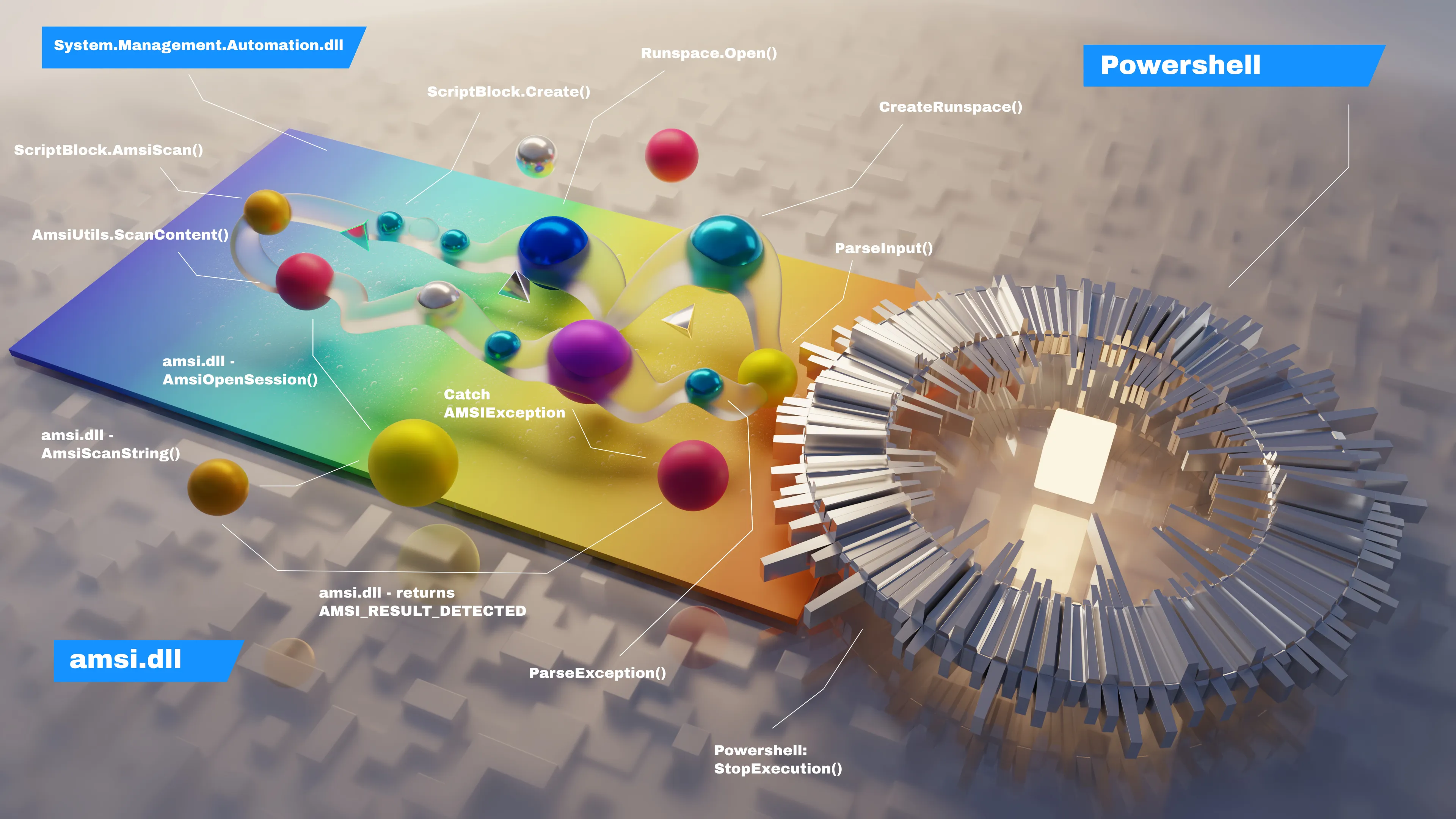
It’s the flow of the code inside the AmsiUtils class in System.Management.Automation.dll and amsi.dll.
All evasions still work fine?
Yeah. The AMSI architecture didn’t change. What’s happening is that Defender does it’s traditional game, probably a mix of hashing, scanning and regex techniques (haven’t looked at it recently, just from the top of my head), to identify, what is malicious. That means: Obfuscations / Variations of Matt Graebers first reflection may trigger an alert. Other variations, doing the same thing, still work fine.
I’m still keeping a few of those under the rug - I need them for RedTeaming. They still work. I hope, in an upcoming article, I can explain, how you can find your own variations.
Note
In my articles about evasion and AMSI I’m talking about a fully updated Defender on Windows 10 - not Defender ATP or other, very expensive, scanners. I can’t afford them so I can’t find anything on them.
BTW: I still got my C++ Reverse Shell running every day, sitting in my registry, trying to connect back to my Kali, and Defender doesn’t give a single. For almost 2 years now?