Published
- 3 min read
Install Pentesting Toolkit on non-rooted, modern Phone

Got your new Schmalaxy SXT9000 Smartphone with the great features and security, but it’s already boring? Let’s bring tools like Metasploit or SQLMap into your Pocket.
Transform Your Phone
without root. It’s pretty easy: First of all, you need to install Termux - just allow untrusted sources and either install it from GitHub or via F-Droid - we took the most recent version from GitHub.
Then simply start by:
$ pkg install root-repoWe wouldn’t worry too much about the older, “untested” repos. Just install python, git and you already made it half-way.
$ pkg install -y binutils python autoconf bison clang coreutils curl findutils apr apr-util postgresql openssl readline libffi libgmp libpcap libsqlite libgrpc libtool libxml2 libxslt ncurses make ncurses-utils git wget unzip zip tar termux-tools termux-elf-cleaner pkg-config ruby
$ python3 -m pip install requestsInstall Metasploit
https://github.com/gushmazuko/metasploit_in_termux/raw/master/metasploit.sh
At the time of writing, the script was clean and can safely be used to install metasploit.
$ cd ../usr/opt/
$ wget https://github.com/gushmazuko/metasploit_in_termux/raw/master/metasploit.sh
$ sh -c metasploit.shIf it errors, just use the individual steps from the script, it’s truly not difficult.
Metasploit DB
Not many issues here, again. It just works.
$ ./msfdb init
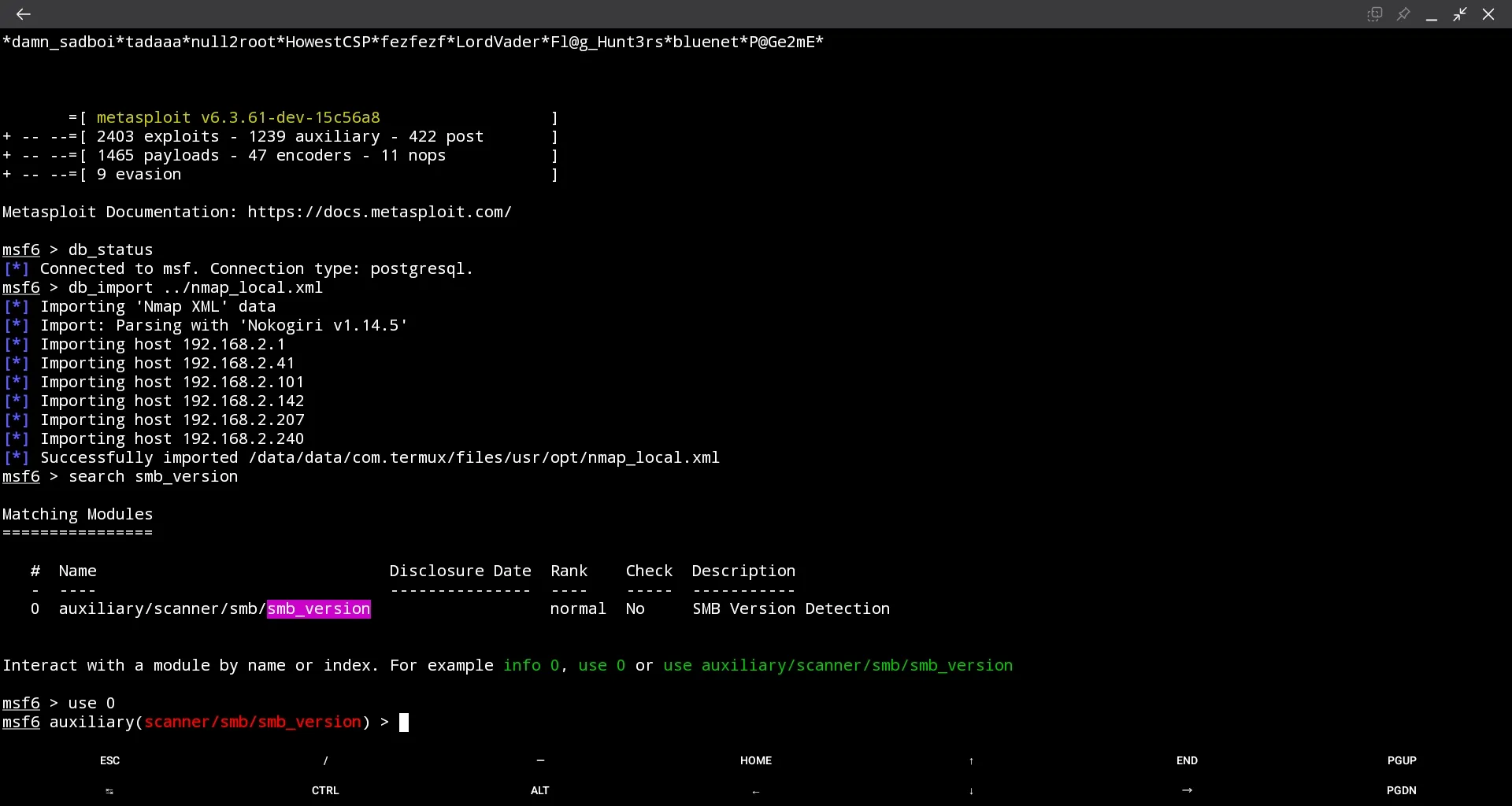
$ ./msfdb startWe import an nmap scan and run a test module on the nmap results. The magic command is:
msf6 > hosts -Rto use the IP addresses from the Database for the current module.
Install nmap
Almost the same way, we install nmap. But we need to build it. However, it works without issues, at least for nmap - building ncat failed, so we ran the script again with nmap as argument and it worked.
$ cd ../usr/opt/
$ git clone https://github.com/nmap/nmap
$ cd nmap/
$ python3 -m pip install setuptools
$ ./configure
$ make
$ make install
$ make nmap
$ chmod +x nmap
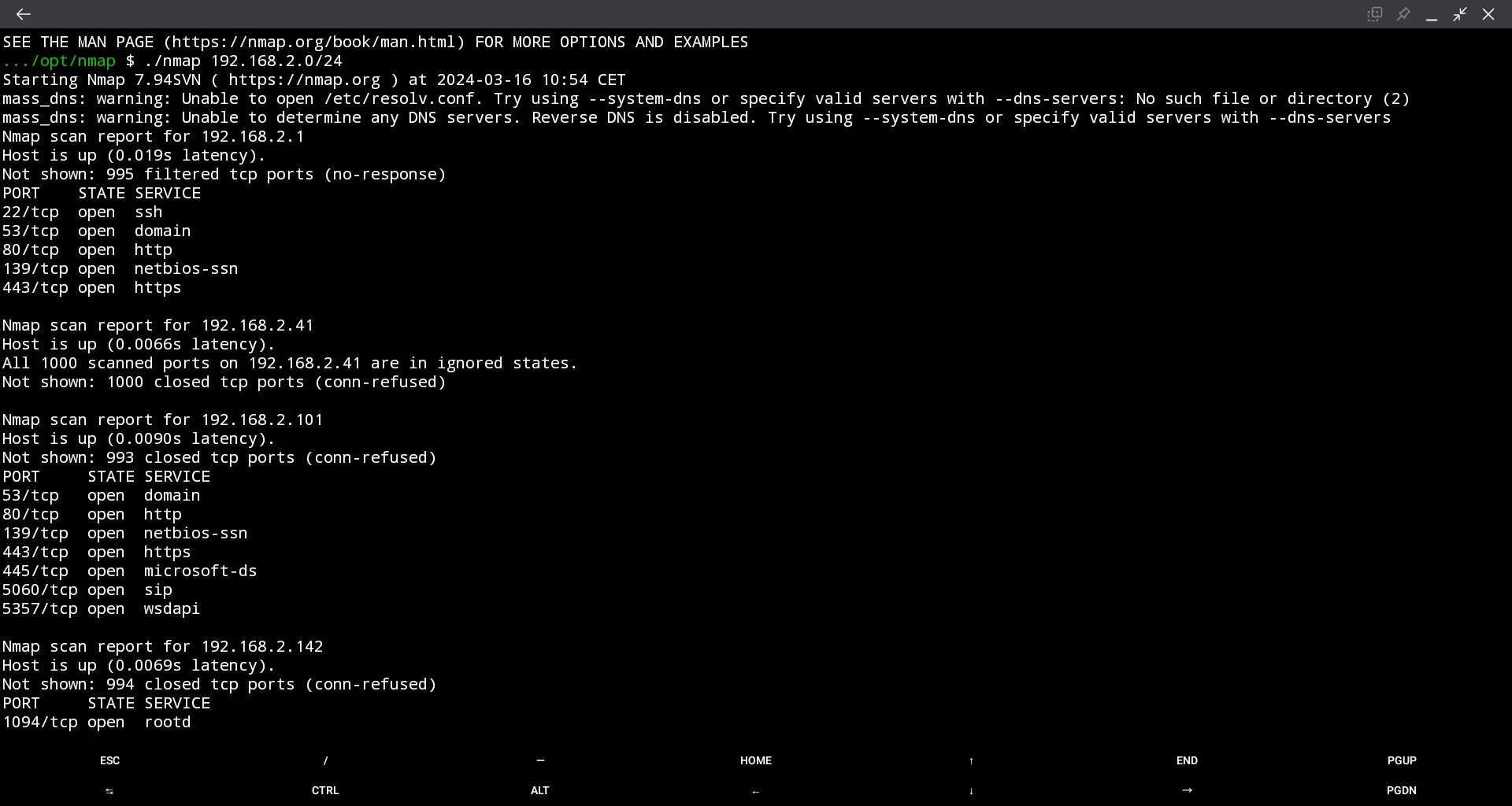
$ ./nmap 192.168.2.0/24 -oA ../nmap_local
We make a test-scan of our internal network - worked!
DNSRecon
Our favourite OSINT tool. Install is just as simple.
$ cd ../usr/opt/
$ git clone https://github.com/darkoperator/dnsrecon
$ cd dnsrecon/
$ python3 -m venv .
$ source bin/activate
$ pip install -r requirements.txt
$ chmod +x dnsrecon.py
$ ./dnsrecon.pyAfter running our resolv-conf script, dnsrecon works perfectly!
Python Resolv-Conf Errors
https://github.com/Network-Sec/bin-tools-pub/blob/main/termux_update_resolvconf.sh
$ cd ../usr/opt/
$ wget https://github.com/Network-Sec/bin-tools-pub/blob/main/termux_update_resolvconf.sh
$ chmod +x termux_update_resolvconf.sh
$ ./termux_update_resolvconf.shWe made a little script you can run after you installed tools like Impacket or DNSRecon. It will update all Python libs, including those in venv environments, so you don’t get an error.
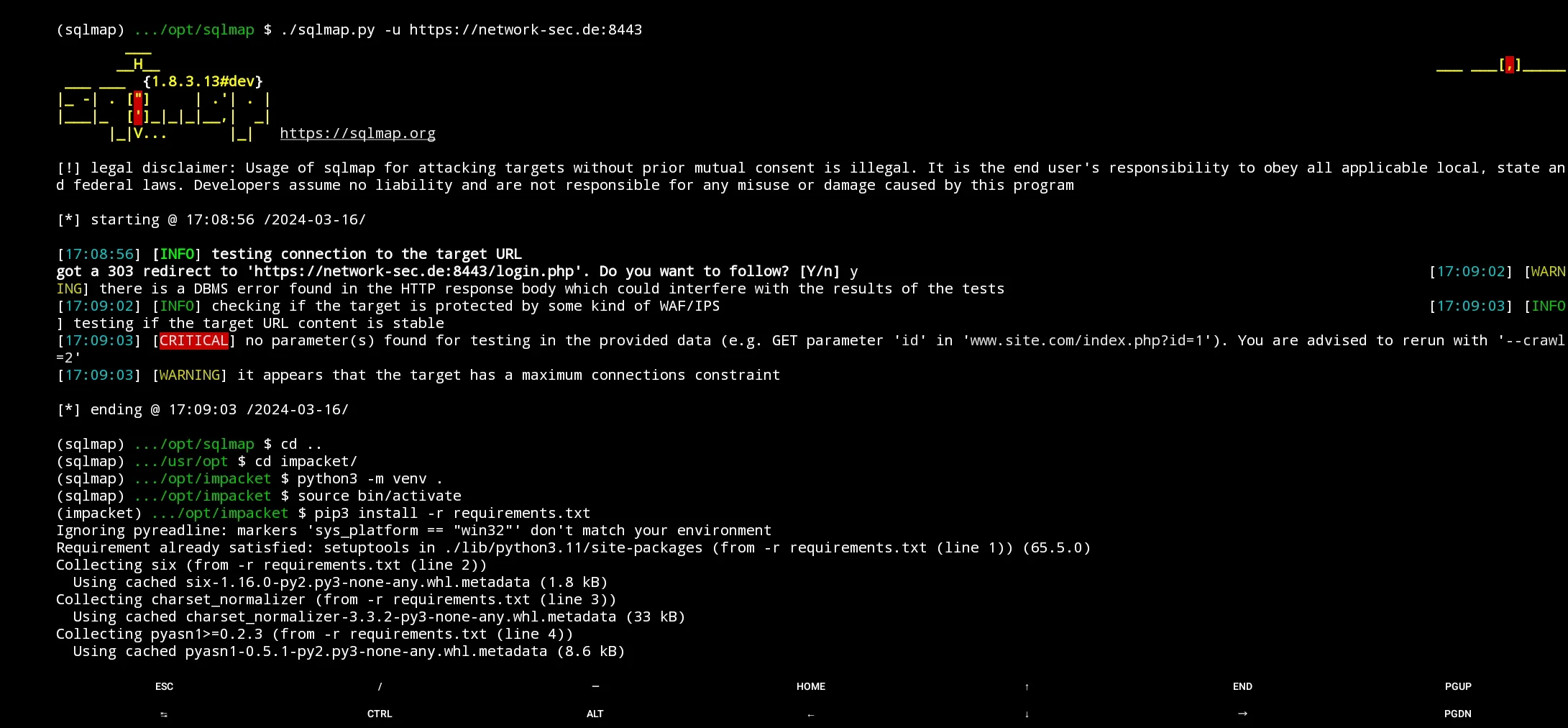
Impacket - SQLMap - Other
For more tools, it’s the exact same process, so we leave it with another screenshot. Most tools work, sadly we couldn’t get responder to work yet. Maybe on another day.