Published
- 2 min read
Email Spoofing: Navigating SPF Bypass

In the intricate web of cybersecurity, Email Spoofing stands out as a silent yet significant threat, frequently underestimated and brushed off as spam. This series aims to shed light on the complex tactics used to circumvent Sender Policy Framework (SPF) checks, essential for email verification.
A Closer Look at SPF Bypass
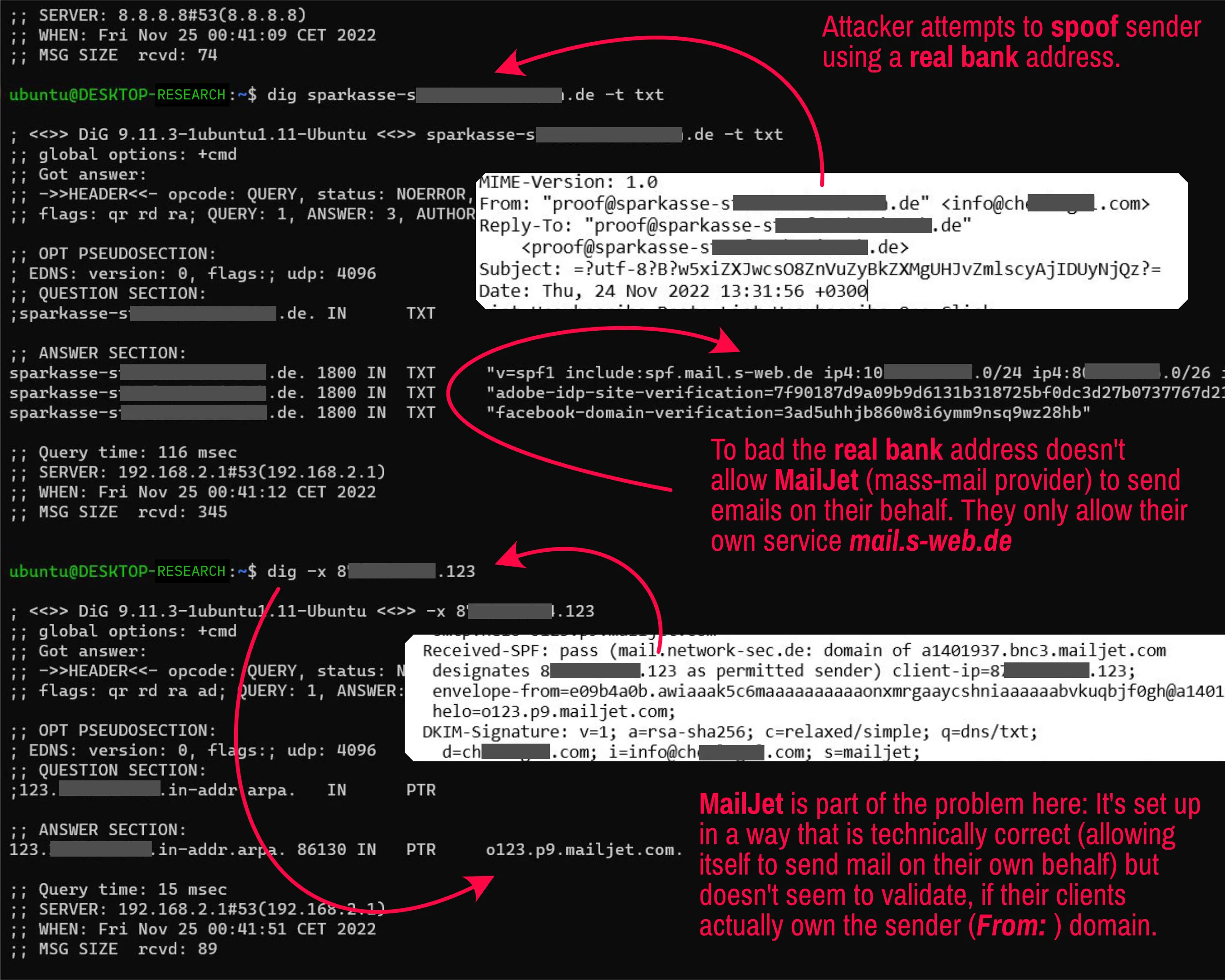
An intriguing case of SPF bypass demonstrates the complexity behind email spoofing efforts:
- The Initial Ploy: Attackers use a spoofed email, appearing to be from ”proof@sparkasse-s_redacted_.de”, leveraging the trust associated with the domain to evade initial filters.
- The SPF Dilemma: The legitimate domain of “sparkasse” only permits emails from its own service, excluding third-party services like MailJet.
- MailJet’s Configuration Issue: Although MailJet’s SPF is set up correctly to allow emails on its behalf, it doesn’t check if clients actually control the ‘From’ domain.
- Leveraging Dual ‘From’ Headers: The attack employs a secondary ‘From’ address with a legitimate SPF record for MailJet, bypassing the SPF restrictions of the spoofed domain.
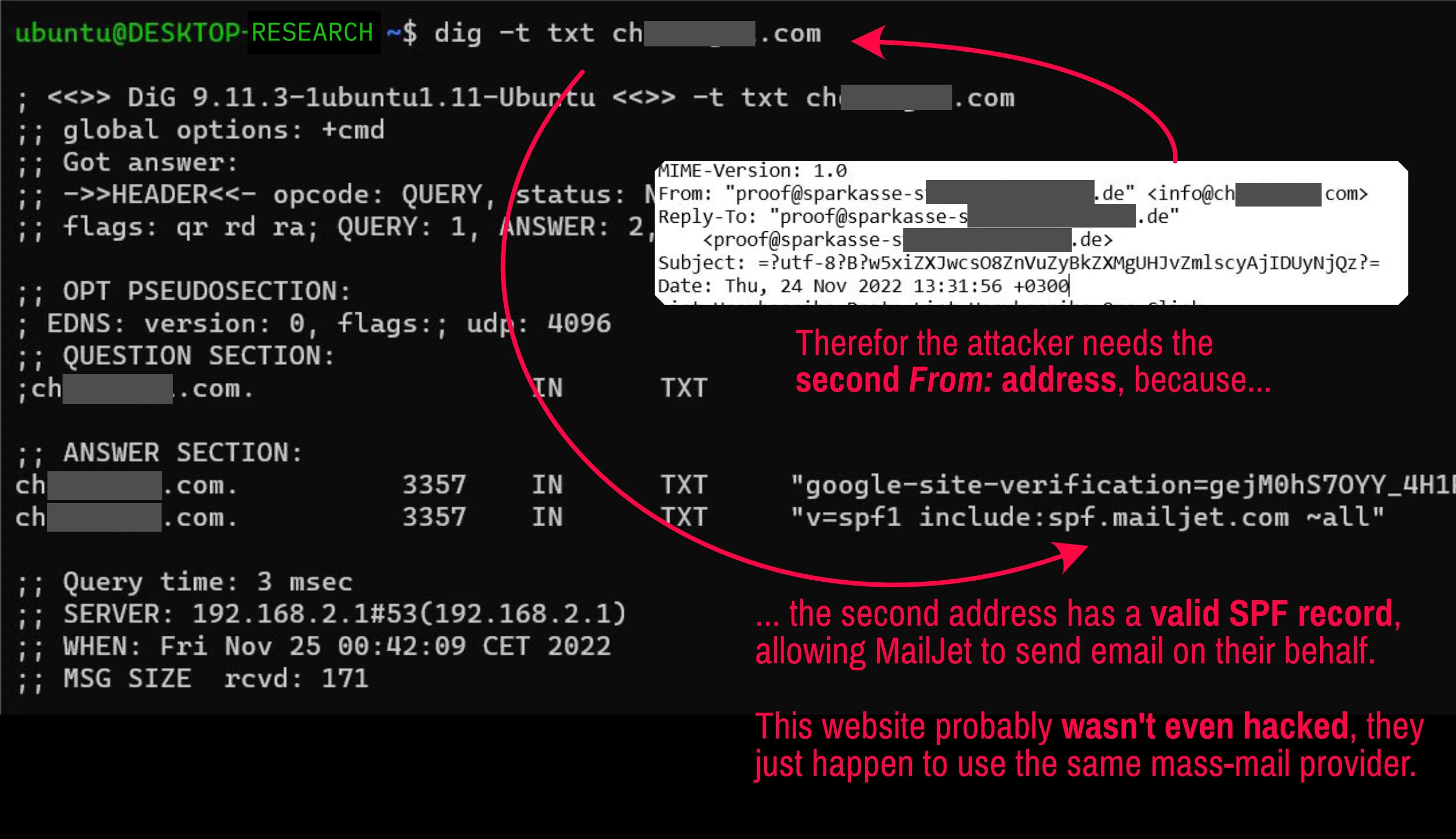
This case underlines the critical importance of stringent SPF checks and highlights the challenges in combating email spoofing. The exploitation of dual ‘From’ headers is a notable SPF bypass technique that calls for increased vigilance and improved validation mechanisms.
Insights and Reflections
This exploration emphasizes the need for rigorous SPF enforcement and the nuanced challenges in email spoofing prevention. It showcases a common yet effective SPF bypass technique, using dual ‘From’ addresses to navigate around direct domain restrictions.
Caution
Understanding SPF bypass techniques comes with the responsibility to use this knowledge ethically. This discussion aims to educate and inform, fostering stronger defenses against cyber threats.
As we continue to explore the realm of Email Spoofing, we’ll provide further insights and strategies to protect against these covert attacks, highlighting the importance of staying informed and proactive in the ever-evolving cybersecurity landscape.